What is the MITRE ATT&CK framework?
MITRE ATT&CK™ framework is a constantly evolving hub of attacker tips, tactics, and techniques used by IT and security teams to pinpoint their organization’s risks and prioritize and focus their protection efforts. It helps cybersecurity teams assess the effectiveness of their security operations center (SOC) processes and defensive measures to identify areas for improvement.
“MITRE ATT&CK™ is a globally accessible knowledge base of cybersecurity adversary tactics and techniques based on real-world observations. The ATT&CK knowledge base is used as a foundation for the development of specific threat models and methodologies in the private sector, in government, and in the cybersecurity product and service community.” – MITRE Corporation.
When and why was the ATT&CK framework created?
MITRE started the creation of the ATT&CK (Adversarial Tactics, Techniques, and Common Knowledge) in 2013 as a solution to help teams achieve more effective cybersecurity by studying attacker methods. Released in 2015, the MITRE ATT&CK framework enables the sharing of adversarial behaviors across the attack lifecycle and provides a common taxonomy for threat analysis and research.
How to use MITRE ATT&CK?
The goal of the MITRE cybersecurity knowledge base is to enable teams to take on an adversary’s perspective to better understand the motivation behind an attacker’s actions and tactics for holistic threat detection and response. This approach provides context to the individual parts of an attack to help teams predict an adversary’s behavior and next move, and quickly and effectively respond to an attack.
MITRE ATT&CK techniques, tactics, and procedures for prioritizing threat mitigation and uncovering security gaps
MITRE first developed the ATT&CK framework as a standard way to document common real-world adversarial tactics, techniques, and procedures (TTPs). This database of information is then applied by security teams to help prioritize which areas of coverage need to be addressed first, and uncover gaps in security controls, processes, and tools. The relationship between tactics, techniques, and procedures is outlined below and can be explored in more detail at the MITRE ATT&CK Matrix™.

What are ATT&CK tactics?
The MITRE ATT&CK framework consists of 11 Tactics that outline the “why” behind an adversary’s approach and represent the objective of their attack. Under ATT&CK, the importance of having security coverage for each Tactic is weighted equally.
What are ATT&CK techniques?
Each Tactic that’s used includes a variety of associated Techniques. ATT&CK Techniques are “how” an adversary achieves an objective — the action they take to get what they are seeking. The framework includes detailed descriptions on how techniques are used and why security teams need to take a deep dive.
What are ATT&CK procedures?
ATT&CK framework Procedures are the specific steps an adversary takes to execute and implement a Technique.
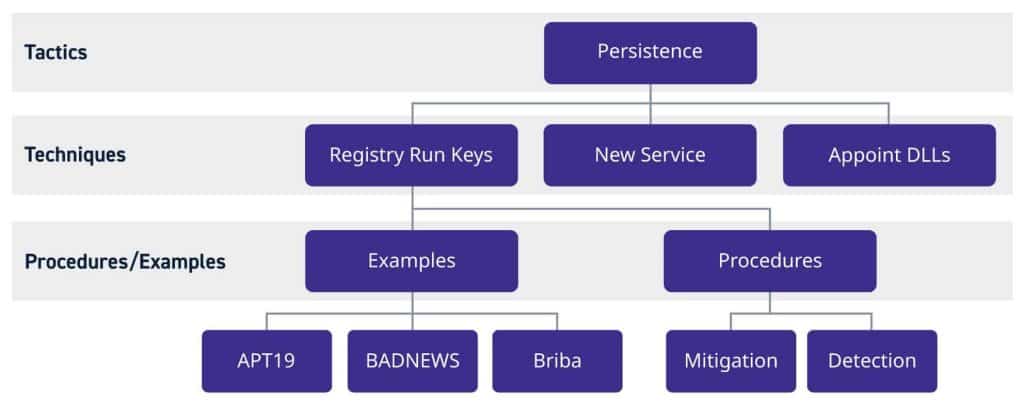
Figure 1: Hierarchal model of ATT&CK tactics, techniques, and procedures.
MITRE ATT&CK for threat hunting and detection
Learn more about using MITRE ATT&CK techniques to identify critical gaps in visibility, enhance your threat detection, and test the accuracy of your detection rules.
Using MITRE ATT&CK™ in Threat Hunting and Detection

Harden your security operations to the MITRE ATT&CK framework with a SIEM solution
Detecting adversaries requires pervasive visibility across your security data and a proactive approach to efficiently identify suspicious behavior. Teams can use SIEM solutions for high fidelity visibility into the ATT&CK tactics, techniques, and procedures of the most skilled adversaries’ for accurate threat detection.
As the constant evolution of the MITRE ATT&CK framework shows, security operations teams must continue to update their methodologies as fast as adversaries iterate to detect new threats and prevent damaging breaches. LogRhythm SIEM is a solution that provides a set of diagnostic tools that teams can use to assess their security program coverage and gaps, so they can prepare for future threats that leverage similar exploits.
The LogRhythm MITRE ATT&CK Module
Organizations can use MITRE ATT&CK’s threat model with the LogRhythm SIEM platform using network and user analytics, compliance modules, and threat feeds to generate higher-value alarms that more accurately detect adversaries.
The LogRhythm MITRE ATT&CK Module, provides prebuilt content mapped to ATT&CK for the LogRhythm SIEM platform, including analytics, dashboard views, and threat hunting tools. This content enables security teams, and in particular, Red Teams to detect adversaries and improve their security program as prescribed by the MITRE ATT&CK framework.
