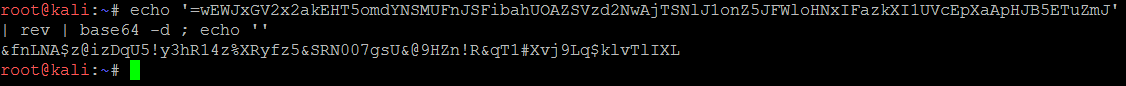Collaboration between, Greg Foss, Nathaniel “Q” Quist, and Michael “Swish” Swisher
For the LogRhythm Challenge at Black Hat USA this year, we wanted to give participants the opportunity to use several different analytic skills in their attempt to beat the challenge. The goal of the challenge was to identify exfiltrated data from Swish Inc., a fictional video streaming company who was recently exposed as having data leaked to a public file sharing site.
The challenge was to correctly identify five hidden flags within a supplied PCAP file. To mislead participants and increase the difficulty of the challenge, several Easter eggs were scattered through the PCAP.
For those of you who rose to the occasion and completed the challenge, congratulations! For those of you who failed, we’ll tell you how to find each of the hidden flags within the PCAP. But before we do, let’s go over the results.
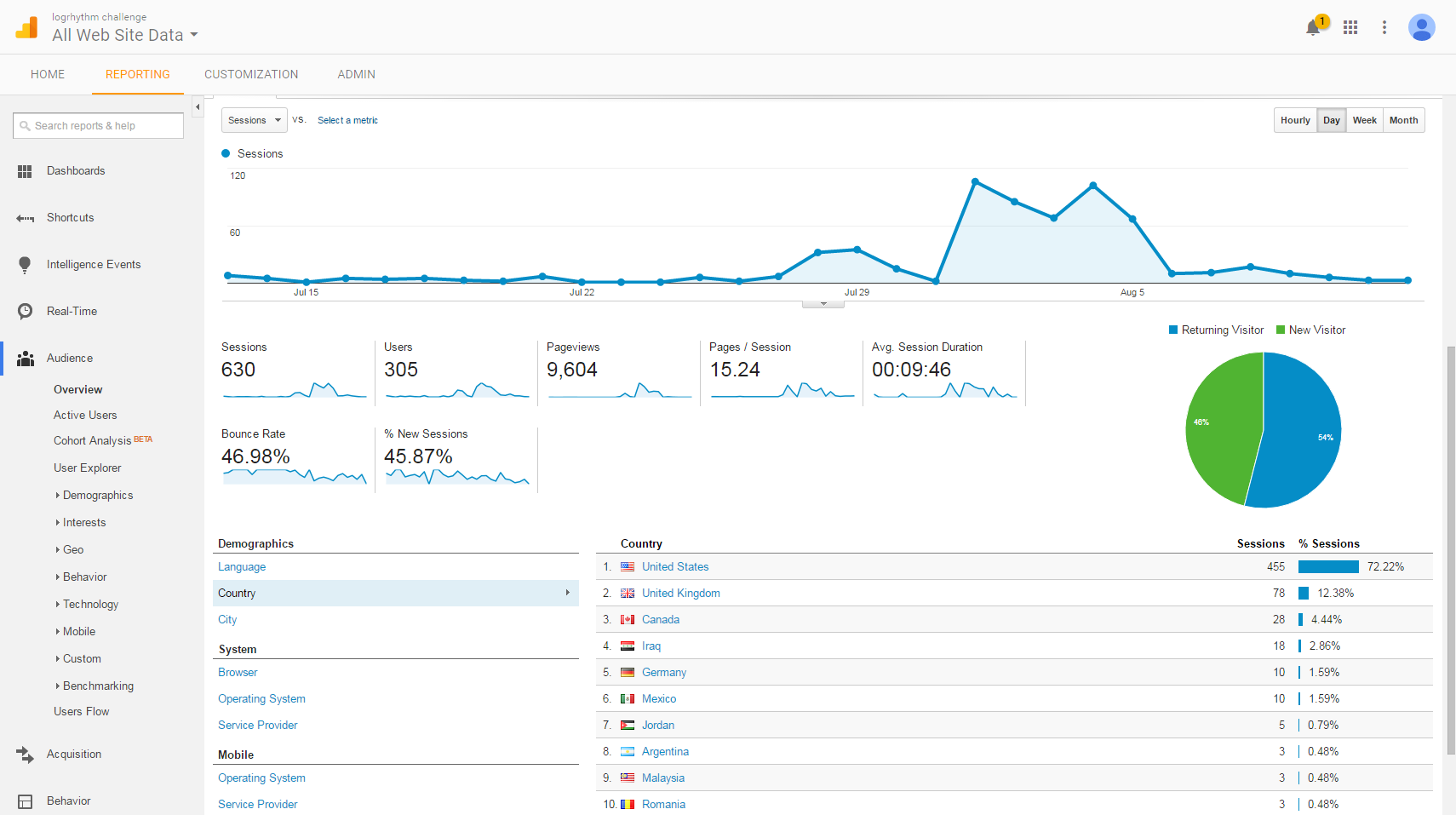
The Results
In total, we had 92 participants and 18 people successfully solve the challenge!
Click on images to view larger
Participants ranged from those attending the Black Hat Conference to talented security professionals from all over the world.
The Solution
As mentioned above, the following post will give you a detailed walkthrough of how to overcome the challenge—flag by flag.
Flag No. 1: Embedded Haiku
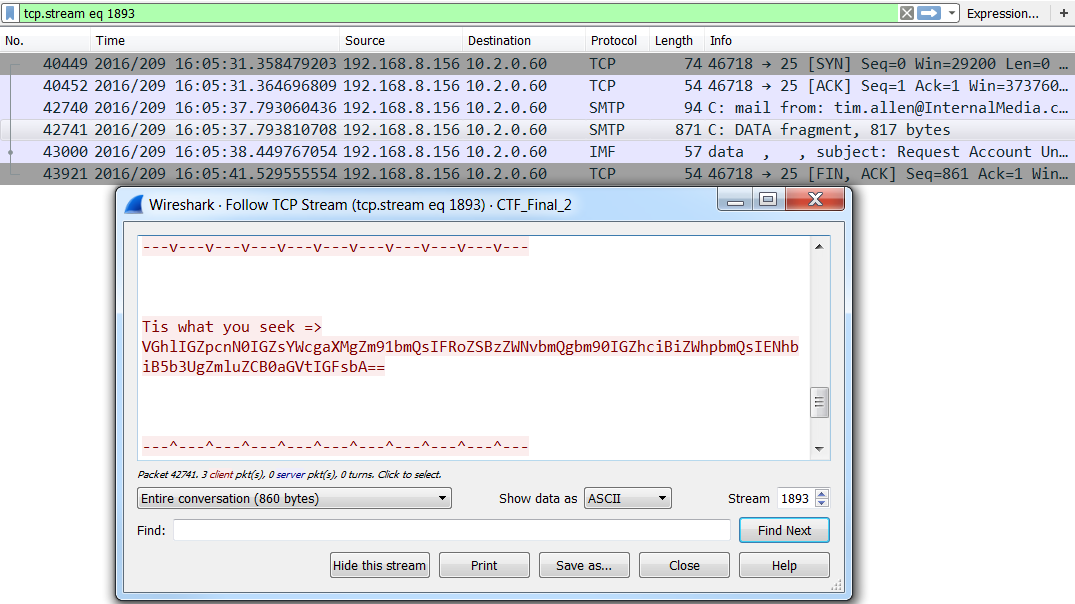
The first flag was a spoofed email directed towards the IT helpdesk. The email requested the resetting of a user’s password so they could successfully meet demands of upper management who requested an emergency meeting. Tim Allen was the spoofed sender of this email. This flag is easily identified by filtering the PCAP file to just SMTP traffic and reviewing the traffic.
The flag was located at the bottom of the password reset request, and contained the following Base64 encoded string:
Tis what you seek => VGhlIGZpcnN0IGZsYWcgaXMgZm91bmQsIFRoZSBzZWNvbmQgbm90IGZhciBiZWhpbmQsIENhbiB5b3UgZmluZCB0aGVtIGFsbA==Upon decoding the string, the resulting haiku proved a success:
The first flag is found, The second not far behind, Can you find them all.Flag No. 2: A Quote
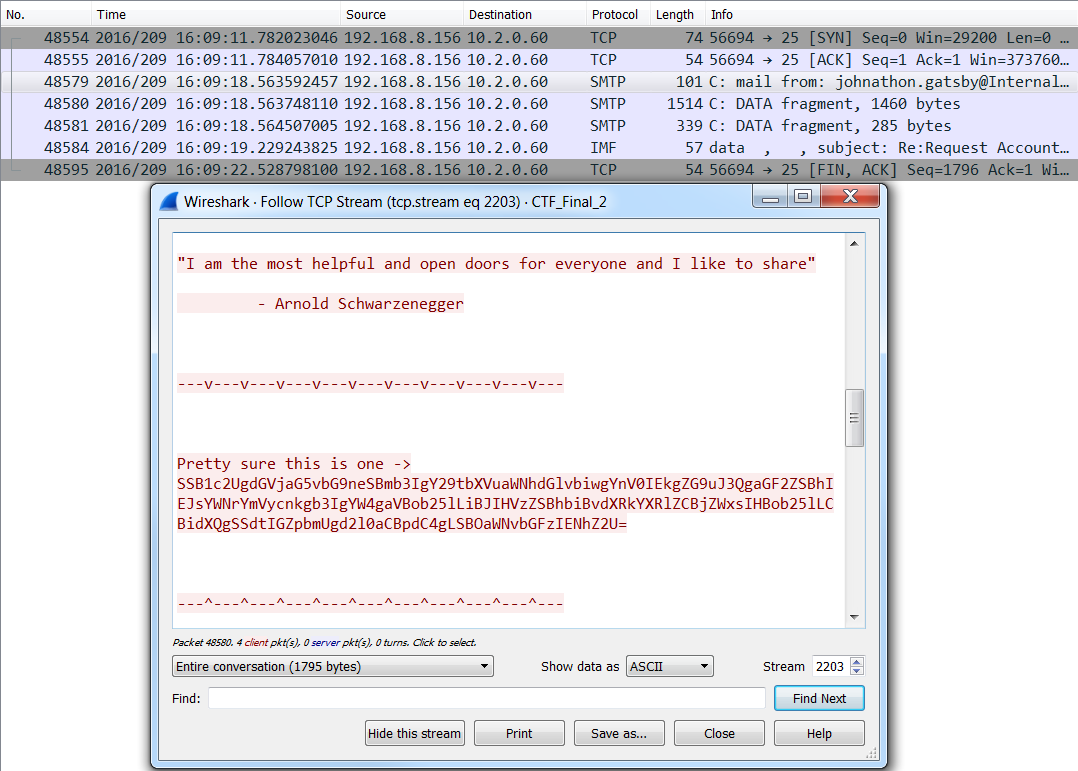
Like the first, the second flag was contained within a reply SMTP message. This SMTP message was the return email from the IT helpdesk technician Jonathan Gatsby (the target of the first spear phishing email). The attacker was listening to network traffic sent to Tim Allen’s machine and was able to successfully intercept the temporary password supplied by the IT helpdesk.
The flag was located at the bottom of the SMTP reply message and contained the following Base 64 string:
Pretty sure this is one -> SSB1c2UgdGVjaG5vbG9neSBmb3IgY29tbXVuaWNhdGlvbiwgYnV0IEkgZG9uJ3QgaGF2ZSBhIEJsYWNrYmVycnkgb3IgYW4gaVBob25lLiBJIHVzZSBhbiBvdXRkYXRlZCBjZWxsIHBob25lLCBidXQgSSdtIGZpbmUgd2l0aCBpdC4gLSBOaWNvbGFzIENhZ2U=This string, when decoded, revealed the following message:
I use technology for communication, but I don't have a Blackberry or an iPhone. I use an outdated cell phone, but I'm fine with it. - Nicolas CageFlag No. 3: Covert ICMP
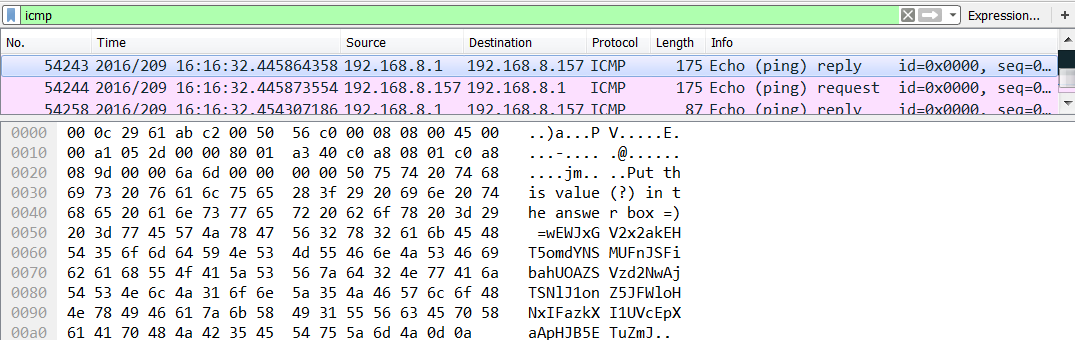
ICMP packets contained the third flag. The attacker attempted to dissuade the analyst by performing a series of SYN and FIN scanning operations designed to mask the transmission of the covert ICMP packets. Identification of the correct ICMP packet revealed another Base64 string:
Put this value(?) in the answer box =) =wEWJxGV2x2akEHT5omdYNSMUFnJSFibahUOAZSVzd2NwAjTSNlJ1onZ5JFWloHNxIFazkXI1UVcEpXaApHJB5ETuZmJThe above Base64 string does appear to be correct. But, actually, it requires an extra step. If you decode this string as is, the result is as follows:
EevftgX5#rR&څCe%swcp46Ruvy$Usq
Vr5QW
vrADfbThis string contains characters which are not native to ASCII, and will they not be of value. But if you reverse the order of the Base64 you get the following:
JmZuTE5BJHpAaXpEcVU1IXkzaFIxNHolWFJ5Zno1JlNSTjAwN2dzVSZAOUhabiFSJnFUMSNYdmo5THEka2x2VGxJWEw=Then when you decode the string, you reveal the following (and correct) string:
&fnLNA$z@izDqU5!y3hR14z%XRyfz5&SRN007gsU&@9HZn!R&qT1#Xvj9Lq$klvTlIXLThis string is the correct answer for Flag No. 3 and plays a key role in uncovering Flag No. 5.
Flag No. 4: Robin Hood
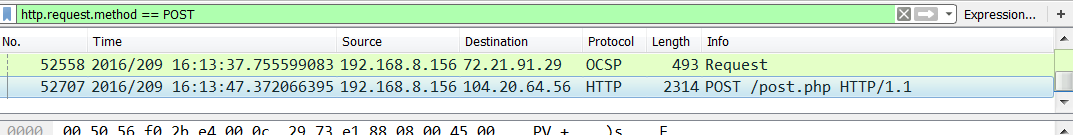
HTTP post transactions contained the fourth flag. This represents the attacker’s use of a third-party file-sharing site to exfiltrate data from the Swish Inc. network. If you search for HTTP post commands within the PCAP, you’ll quickly identify the correct network traffic containing the flag. Like the previous flags, the fourth flag was also a Base64 string.
You funda un floogin =} SWYgeW91IGZpbmQgYSBSb2JpbiBIb29kIHdpdGggYW4gQW1hemluZyBSYWluYm93IGFuZCB0aGVuIHlvdSBmaW5kIHRoaXMuLi4gWW91IGxvb2tlZCBhIGxpdHRsZSB0b28gZGVlcC4gQnV0LCBhIHN0aW5naW5nIHBhdCBvbiB0aGUgYmFjayBmb3IgbG9va2luZyB1bmRlciBldmVyeSByb2NrIQ==To further obfuscate this flag, instead of having the decoded phrase as the answer, we decided to make the answer the Base64 string itself. To hint at our trickery the decoded phrase read:
If you find a Robin Hood with an Amazing Rainbow and then you find this...You looked a little too deep. But, a stinging pat on the back for looking under every rock!Flag No. 5: The Final Test
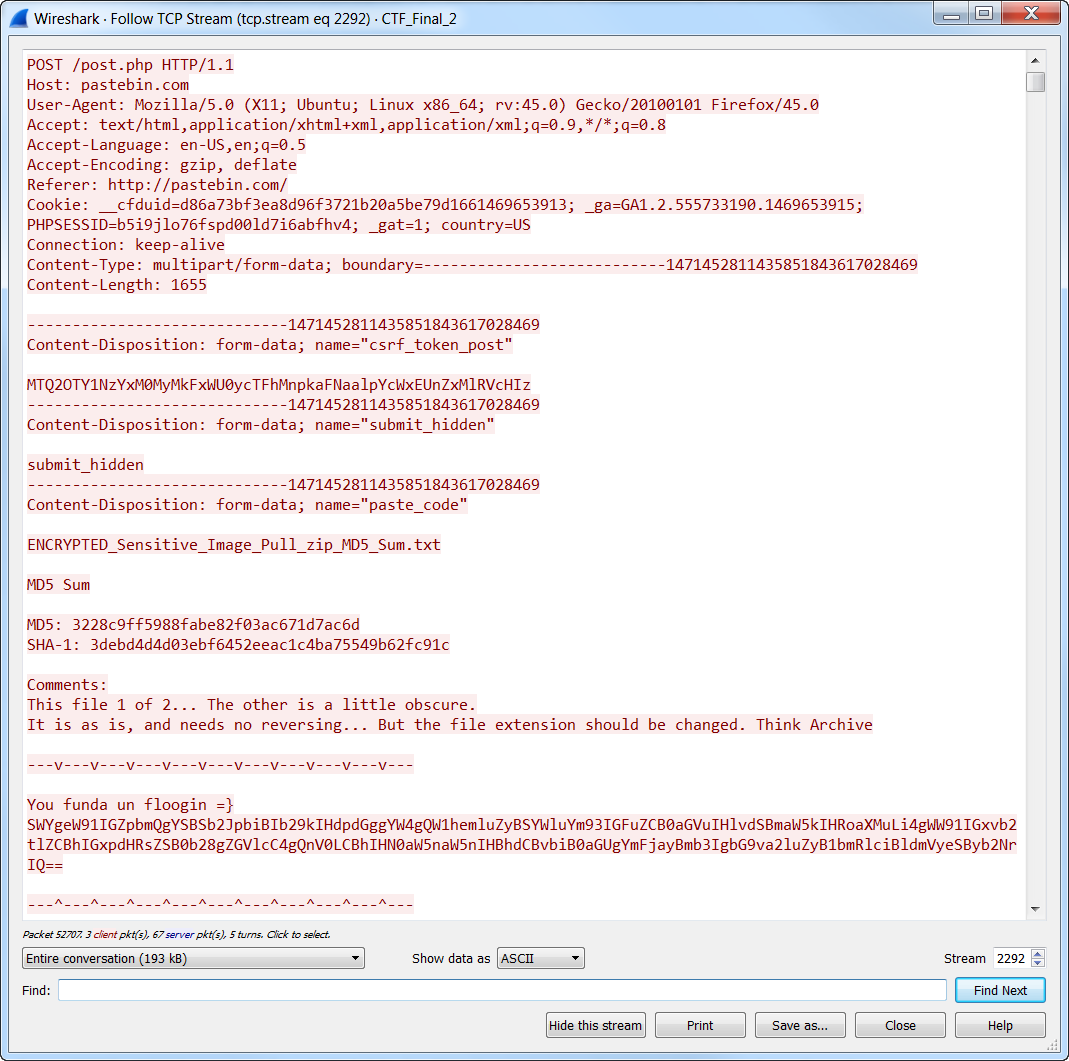
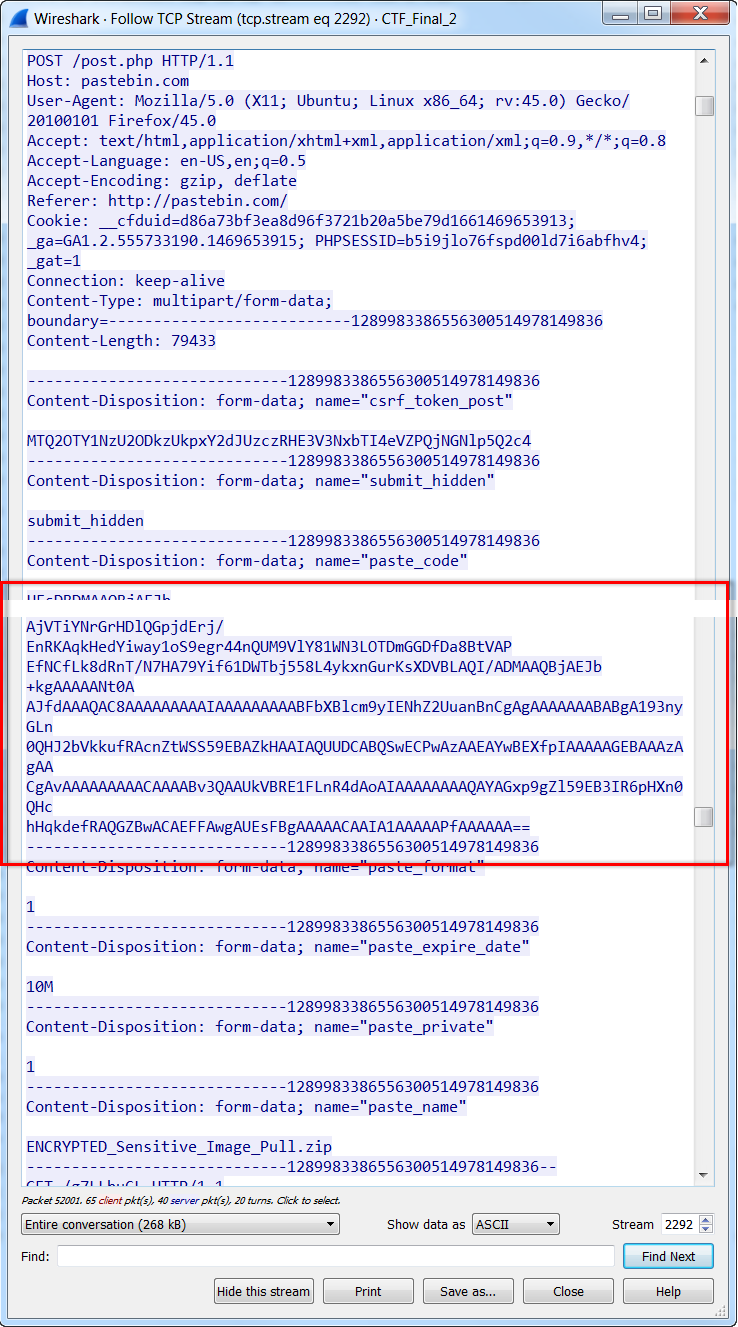
To find the fifth and final flag, you had to successfully solve both Flags No. 3 and No. 4. But ultimately, an encrypted zip file contained the final flag. The key to this encrypted file is the reversed and decoded key found within Flag No. 3. Flag No. 4 was also paired with Flag No. 5 and pointed you to the uploaded data. Using a packet analyzer, you are able to pull the code directly from the HTTP post session.
If you extract the Base64 text, and then decoding the text, you reveal a binary pattern associated with a known file extension: ZIP.
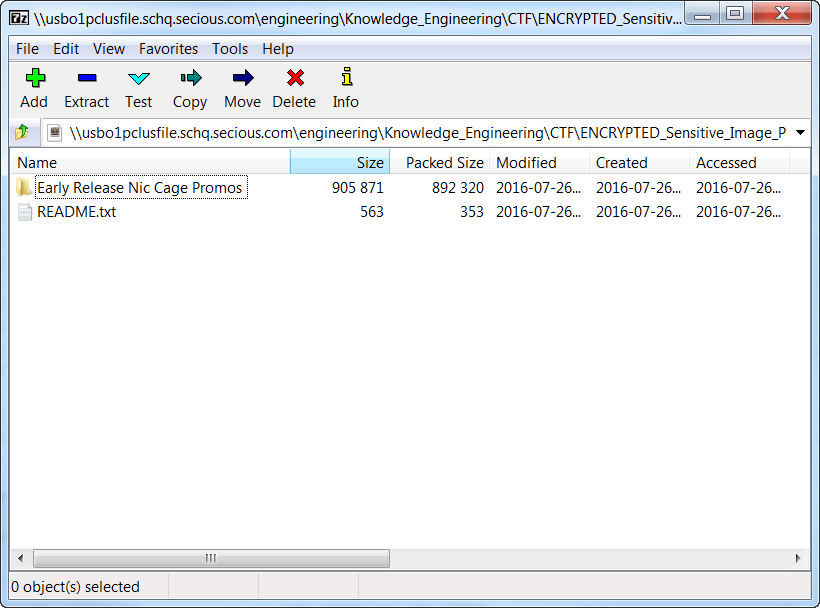
Simply renaming the text file with a .zip extension will allow you to open the zip folder. A password prompt is now presented to extract the contents of the ZIP File. To find the final flag, you must use the reversed and decoded key (obtained from Clue no. 3) to the password prompt and examine the contents of the zip folder.
The final flag is contained within a Text File titled ‘README.txt’, and it includes instructions for not distributing the very delicate image stolen from Swish Inc. The final flag was also a Base64 string:
La bandera final :) WW91IGZ1bmRpbiB1biByb3V0aW4gdHJ1IGRhIGZsb29naW5zIQ==When decoded the final flag was:
Fundin un routin tru da flooginsThere you have it: the complete breakdown of the 2016 LogRhythm BlackHat Challenge!
We hope that you enjoyed testing your network analysis and forensics skills. We had a blast putting the challenge together. Looking forward to challenging you next year!