I’d like to talk a little bit about a new POS Malware variant called LogPOS. Being a researcher at LogRhythm I feel it is my duty to talk about any Malware with the word “log” in it. Ironically this malware does not store its stolen credit card data in a log, instead it utilizes mailslots. Mailslots, just like the name implies, are a virtual representation of a physical mailbox. It’s a mechanism developed by Microsoft that allows processes to communicate with each other. A process can write to a mailslot with the intention that another process can read from it later on. They are similar to named-pipes only they are not connection oriented and can be used for broadcast. The use of mailslots by malware is nothing new and their existence helps this malware fly under the radar of simple POS malware scanners—scanners that look for plain text credit card information which is stored locally on the POS terminal.
LogPOS starts by creating a mailslot named \\.\mailslot\LogCC. Once that mailslot is created the malware systematically searches the host for processes that are not in the white list, shown below. My guess is that these are known common processes that you might find on POS terminals (with the exception of steam.exe) that are not used for scanning credit card data. So, it’s eliminating a few processes right off the bat, maybe for efficiency, but more likely to remain undetected.
- windbg.exe
- logounui.exe
- taskmgr.exe
- skype.exe
- thunderbird.exe
- devenv.exe
- steam.exe
- winlogon.exe
- wininit.exe
- csrss.exe
- smss.exe
- svchost.exe
- firefox.exe
- chrome.exe
- explorer.exe
- psi.exe
- pidgin.exe
- System
Once the malware finds a process not included in the list above, it will inject shellcode into that process. That newly compromised process will then repeat the search looking for more new processes to pwn (again, ignoring white listed processes) and injecting shellcode until all other processes have been hijacked. At this point the malware uses Luhn’s Algorithm to search for credit card numbers. Once a credit card is found it is written to the opened mailslot where the main program will read from it. Once a credit card is read it is then sent to a remote server via GET request.
If you want to take a look and see if you’ve been hit by LogPOS in your environment, you can use this simple search in the LogRhythm NetMon to reveal any outbound communication from the POS malware:
Method:GET AND DestPort:(80 OR 443) AND HeaderRaw:(encoding= AND t= AND cc= AND process= AND track=)
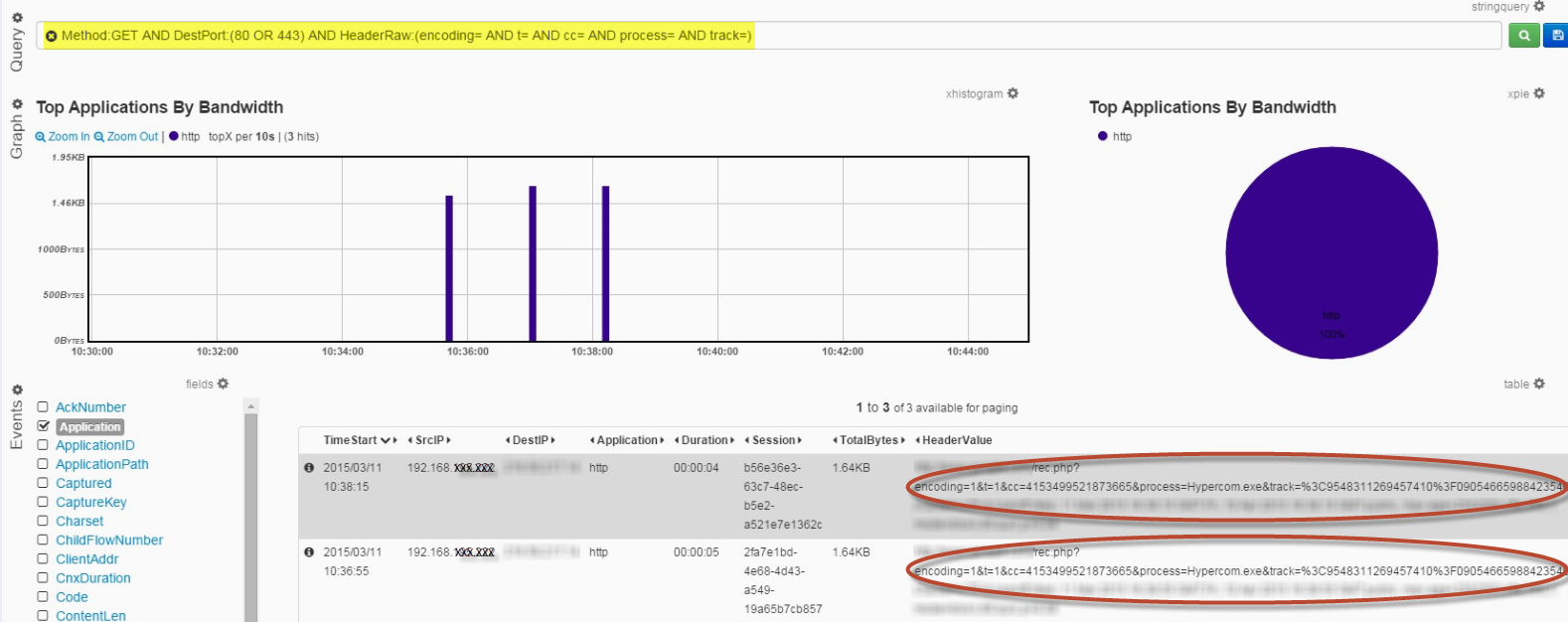
Figure 1 : Example LogPOS Traffic in LogRhythm NetMon
On Top of that you can also utilize LogRhythm’s Advanced Intelligence Engine’s white listing capabilities to detect new outbound connections from your POS terminals. This rule along with dozen more are part of LogRhythm’s Retail Cyber Crime Module.
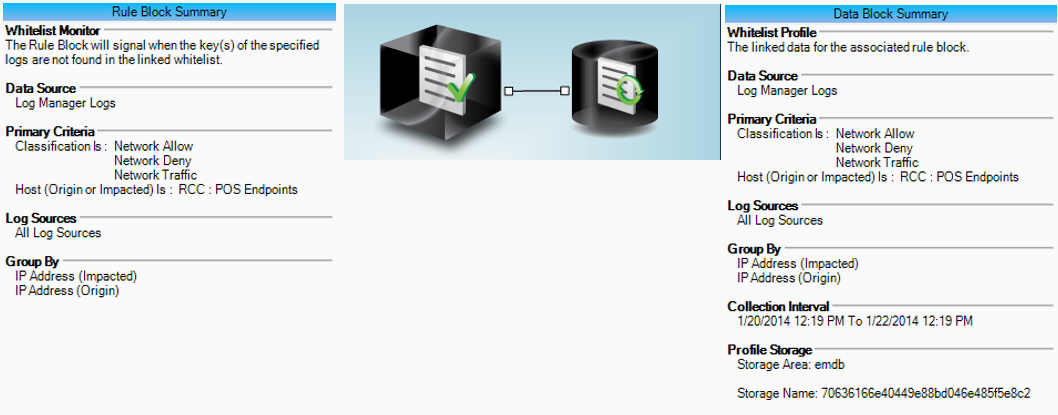
Figure 2 : POS: Abnormal POS Network Communication Detection