A new sophisticated, layered and targeted malware has been hitting Russia and Russian interests lately, and is starting to spread out.
This has been named “Inception Framework” because of its massively layered design, in reference to the 2010 “Inception” movie.
The malware is very ingenious:
- exploits at least CVE-2010-3333, CVE-2012-0158 and CVE-2014-1761
- exists only in RAM
- polymorph
- targeted
- multilayered
- C&C hidden in normal traffic and to legitimate servers
- attacks both computers and mobile phones
- etc…
But all is not lost, as there are a very few things that can still be caught when a person is infected.
As per BlueCoat’s very informative blog post:
Signs of compromise:
- Unauthorized WebDAV traffic
- exe continuously running in the process list
Ways to prevent infection:
- Keep software updated
- Don’t jailbreak mobile phones
- Don’t Install apps from unofficial sources
Signs of being targeted:
- Unsolicited emails containing rtf documents
- Unsolicited emails or MMS messages suggesting smart phone applications need updating
All the above vectors that are italic are covered by the correlation set below.
Layered approach to detection
For such a layered malware, it only sounds appropriate to engage in a layered detection method:
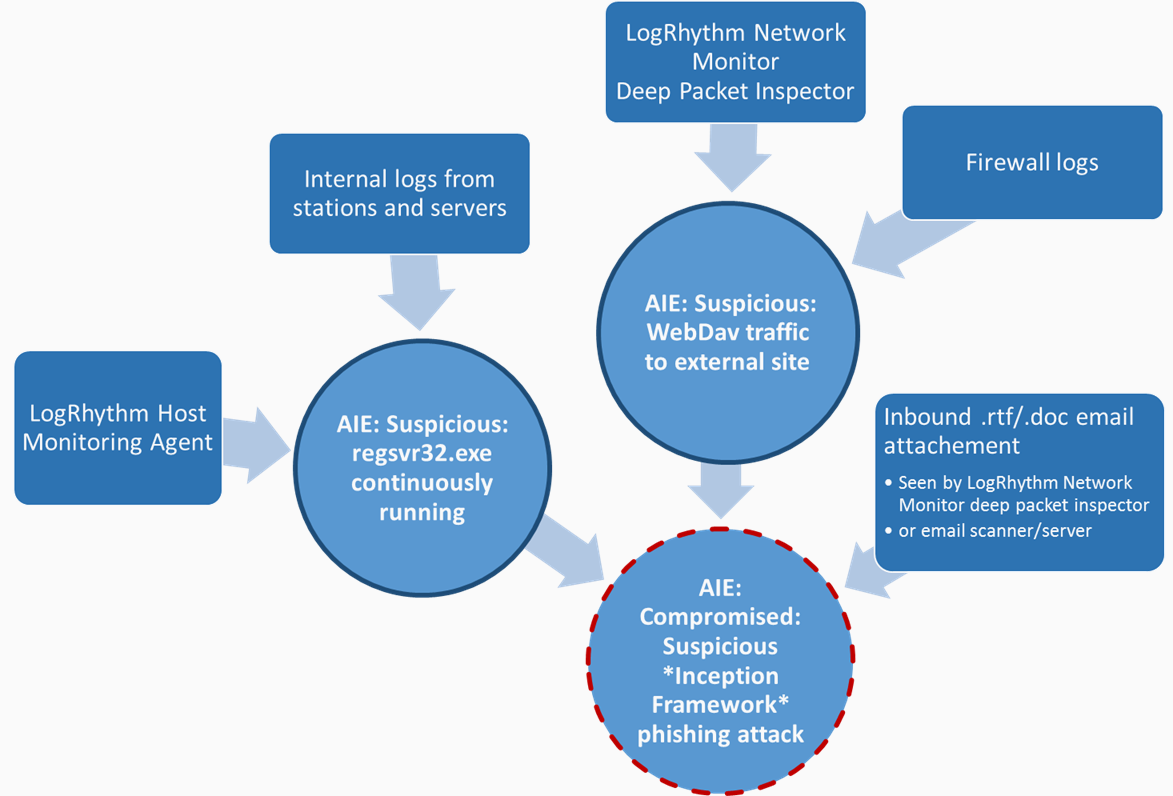
- So, first we will track any “regsvr32.exe” process that starts but never stops, on servers and workstations, using one real-time AIE correlation rule, that will spit out an Event flagged as Security: Suspicious and an Alarm.
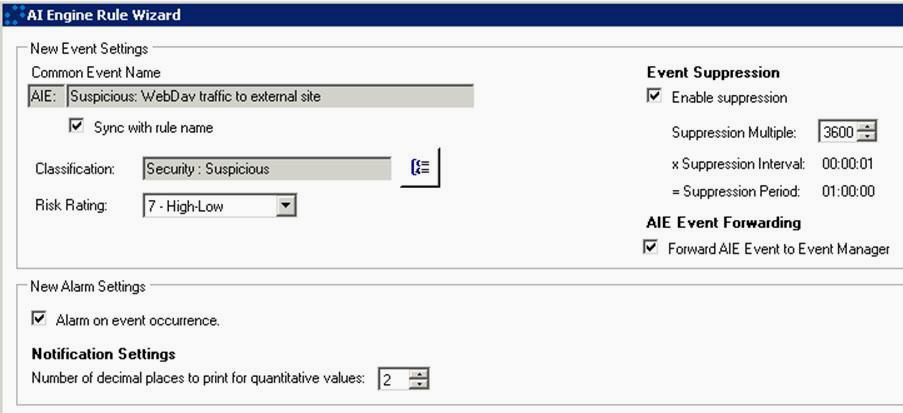
- In parallel we’ll keep an eye on any outbound WebDav traffic, using a second real-time AIE correlation rule and generate a Security: Suspicious Event and an Alarm here too.
- Finally, we will corroborate all these correlations together and if they both occur on the machine of someone who just received an inbound email with an RTF or Word documents attached, then raise a Security:Compromised Event as well as an Alarm.

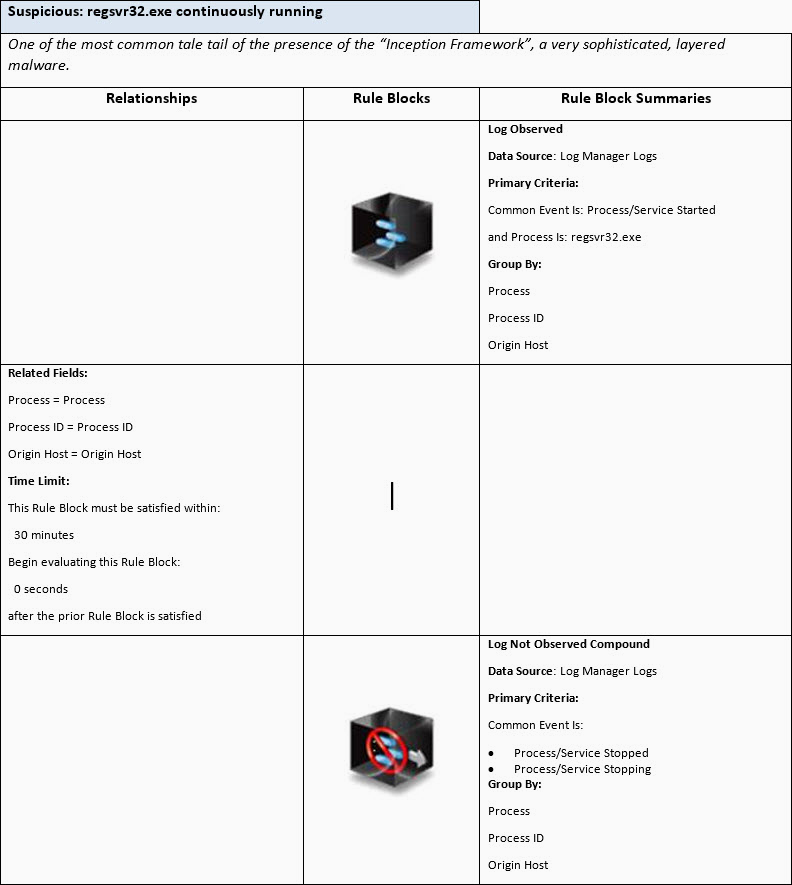
Rule 1, detecting the (too) long running regsvr32.exe:
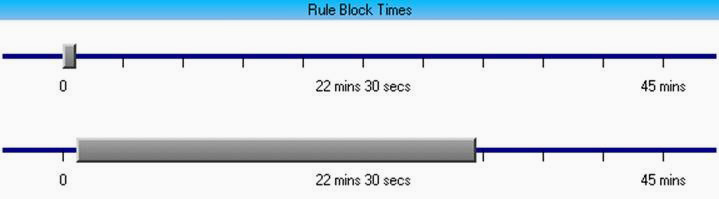
Time line:
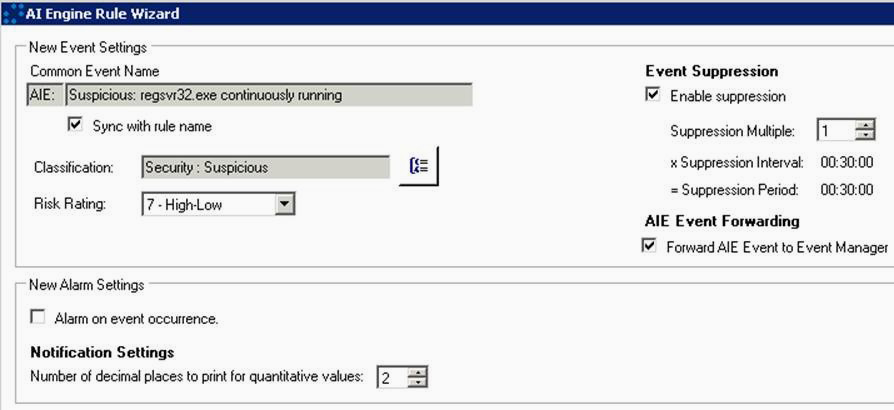
Settings:
Rule 2, detecting outbound traffic using WebDav protocol:
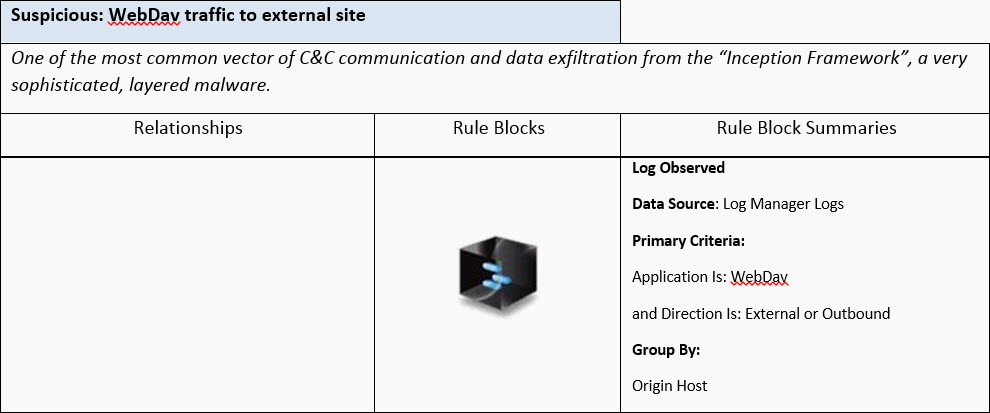
Settings:
Rule 3, corroborate all the above and check precedence of inbound RTF or DOC email attachments:
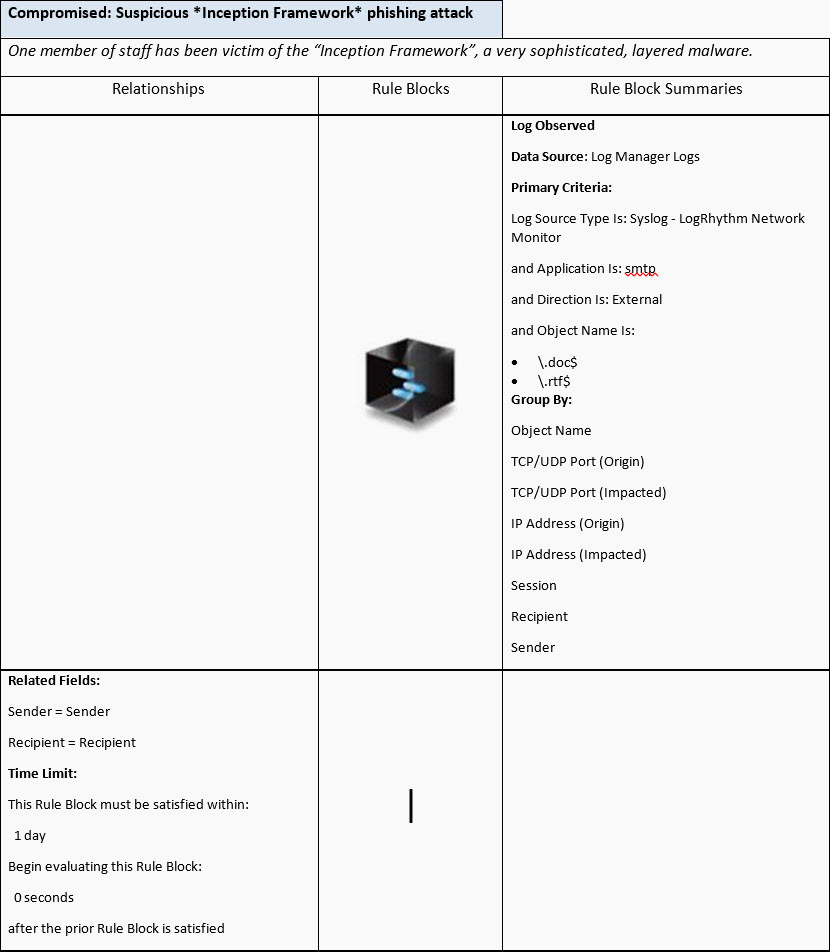
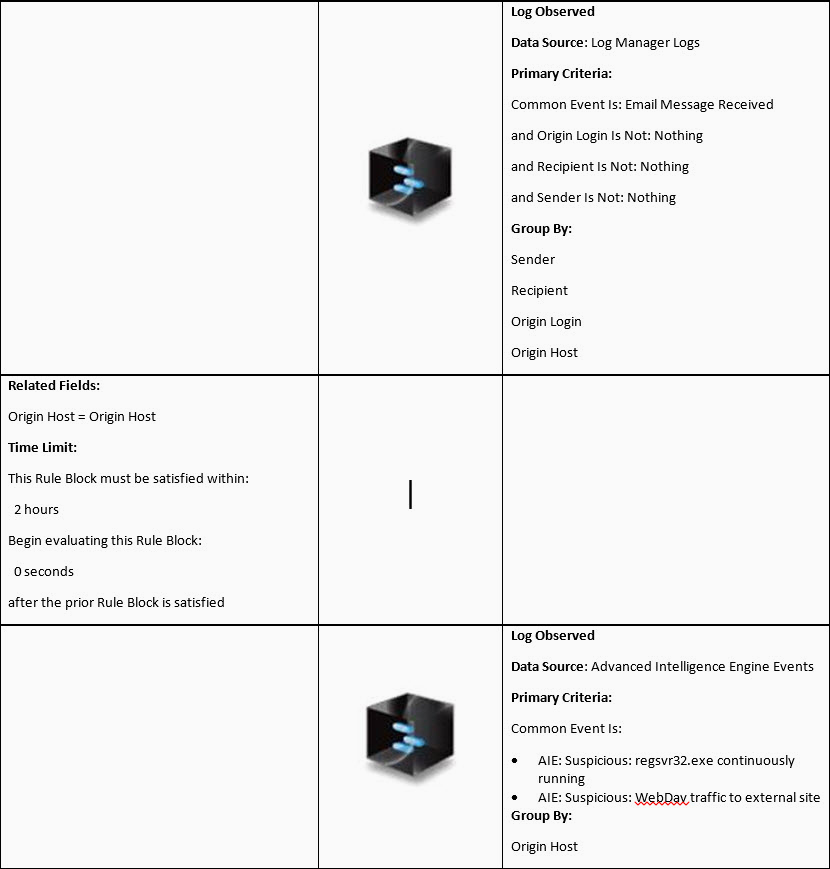
Time line:
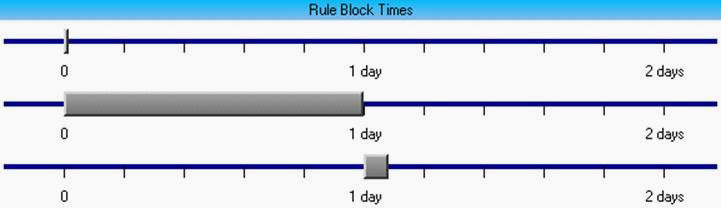
Settings:
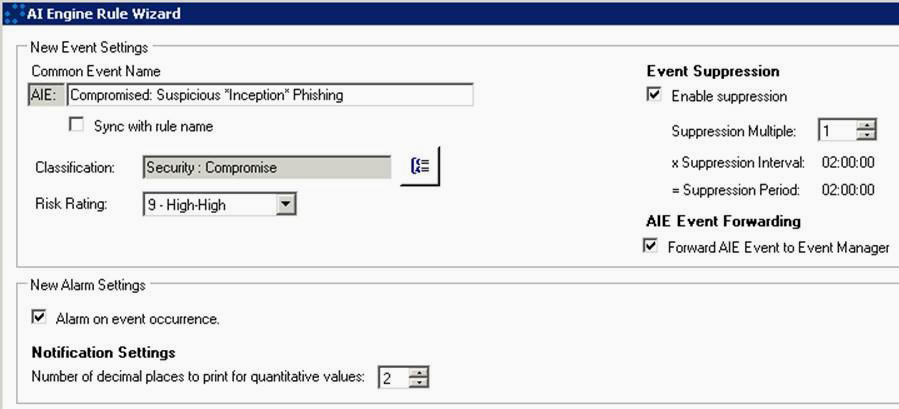
Equipped with these little helpers, you should now be able to relax for this festive season with the knowledge that any Inception style incursion into your workstations will be flagged.
Moreover, you’ll be made aware of who in your organization is being targeted by the attack early enough before any critical data is siphoned out.
Sources:
- https://www.bluecoat.com/security-blog/2014-12-09/blue-coat-exposes-%E2%80%9C-inception-framework%E2%80%9D-very-sophisticated-layered-malware
- http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2010-3333
- http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2012-0158
- http://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-1761