I’ve been running a test Network Monitoring (NetMon) Mini device at home for the past few weeks and, up until recently, I didn’t notice anything “unexpected” on my home network.
Figure 1: Miniature NetMon Home Appliance (Click on images to view larger.)
From time to time, I’ll stand servers up in the DMZ so that I can reach them externally and use them for projects. So, to ensure that I can always reach these boxes, I use DynDNS to link domain names to my home IP address. This is necessary, as most home Internet Service Providers will periodically rotate IP addresses unless you have a dedicated business line.
DynDNS provides the ability to dynamically update your DNS addresses to point to the new IP address whenever it changes. I do not normally like leaving guessable DNS entries tied to my home network and I prefer to change my DNS settings from time to time, so I usually log into DynDNS and manually create new entries as needed.
Trouble with DDClient Updater
I recently decided to try out the DynDNS updater client DDClient (use apt-get / yum instead of the download link) to dynamically update my configuration. DDClient is essentially a Perl script that you can configure on a Linux host to periodically update your DynDNS entries with your current IP address.
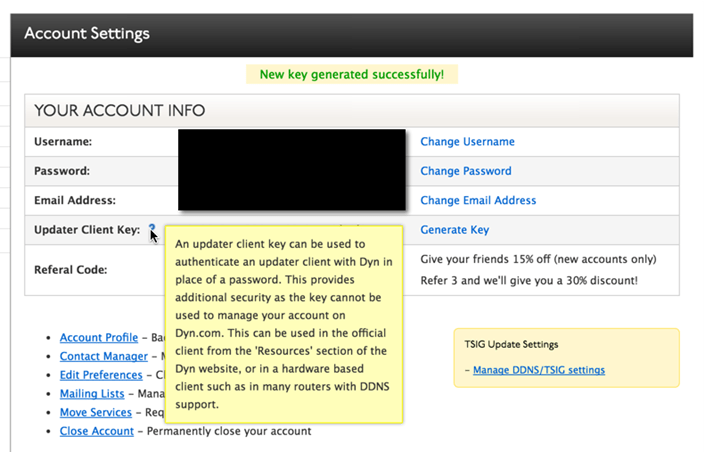
As I followed the default configuration, I noticed one item that raised some red flags. It looked like the updater client was storing credentials in plain text within the configuration file. Fortunately, it’s possible to configure a key to use for this, as opposed to a password.
Figure 2: DynDNS Client Updater Setting (Click on images to view larger.)
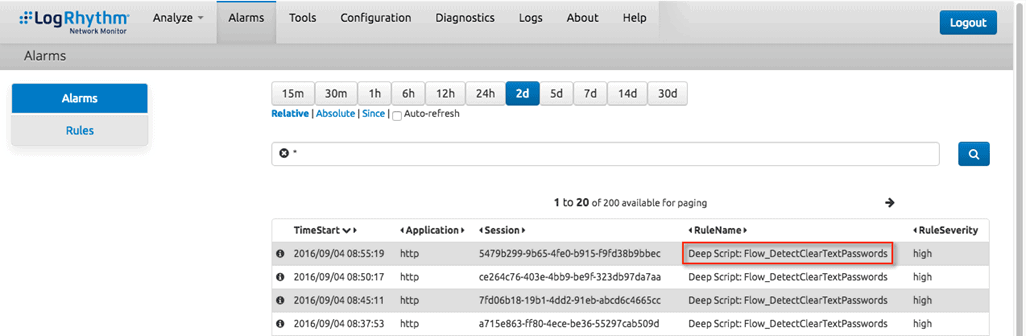
Now that I had the key set and DDClient running as a service on my server, I called it good and went about my business. The next day, I logged into the NetMon dashboard and reviewed the alerts. Surprisingly, the “Detect Clear Text Passwords” deep packet analytics (DPA) rule was firing consistently about every five minutes.
Figure 3: Detect Clear Text Passwords DPA Alarm (Click on images to view larger.)
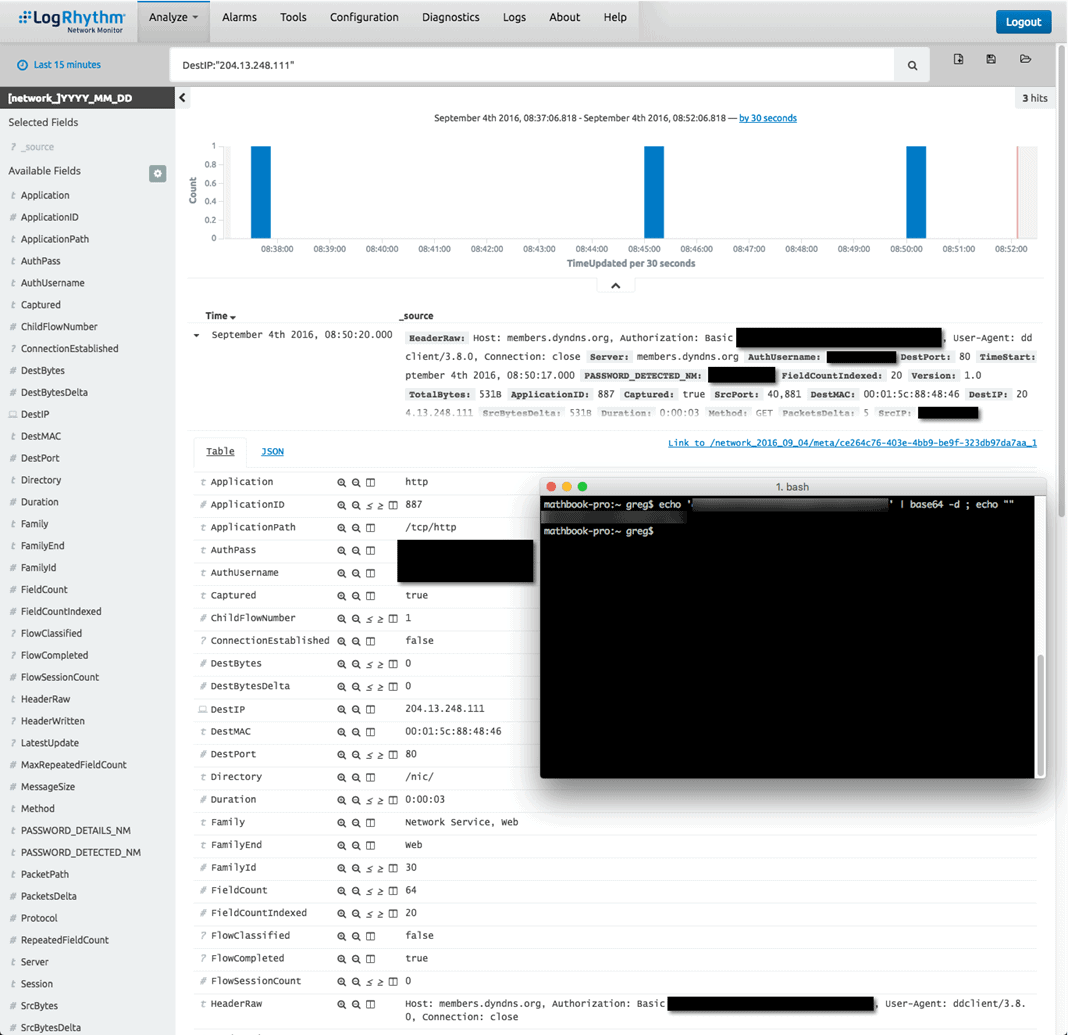
After a quick drill down into one of these alarms, I immediately found out that that the culprit was DDClient. Unfortunately, the DDCLient service sends username and password information over HTTP using only basic base64 authentication (which NetMon can automatically decode) to check in with DynDNS every 5 minutes. Meaning anyone could sniff that traffic, log in as me, and point my DNS entries wherever they wanted.
Figure 4: Alarm Drill Down (Click on images to view larger.)
Clear Text No More
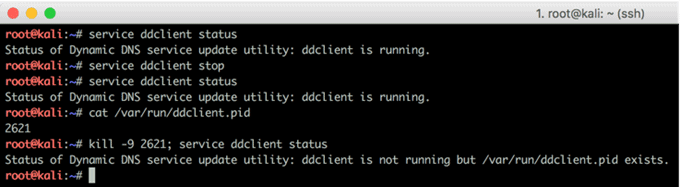
After realizing my information could easily be captured, I killed DDClient right away—which turned out to be a bit trickier than anticipated.
Figure 5: Having Trouble Killing the DDClient (Click on images to view larger.)
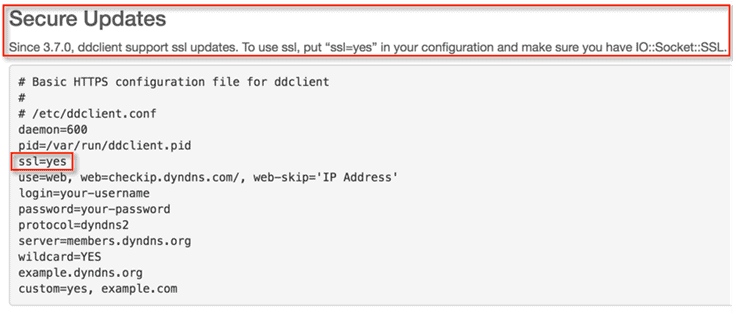
Once I had the DDClient down, I did some research and found out that it’s relatively easy to configure DDClient to use SSL. However, I found it a bit disappointing that this isn’t the default configuration and that you need to dig for it.
Figure 6: DDClient is SSL Compatible (Click on images to view larger.)
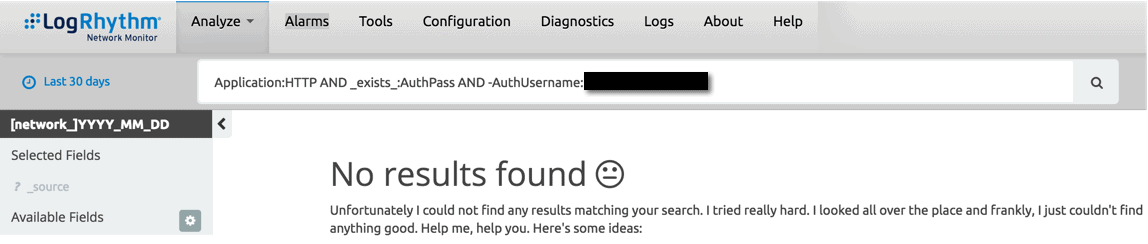
Fortunately, after getting this issue locked down, I confirmed that no other basic authentication credentials were being passed over the network in clear text.
Figure 7: All Clear (Click on images to view larger.)
Key Takeaways
A lot of people use DynDNS or similar services to create dynamic DNS entries for their home network. Unfortunately, they trust that the product they are using has taken reasonable measures to ensure the security of their account credentials. Many times this isn’t the case.
Also, most people don’t analyze the packets that are traversing their hosts, let alone their home network as a whole. (Meaning something like this could go undetected for months and even years.) In reality, this type of misconfiguration has the potential to be rather damaging if someone used a password that they use elsewhere, and another party was able to sniff that traffic.
Analyzing home network traffic can be highly valuable as you can find previously unknown issues smoothly and efficiently by using built-in rulesets within NetMon. In addition to security issues, you can also track usage statistics and determine what (or who) is utilizing the most bandwidth on your home network.
The good news for you is LogRhythm has released NetMon Freemium. You can easily use hardware that you might have lying around to capture and understand the data traversing your network. For free. Download it below. Do it.