Continuously detecting and responding to malware threats can be an operational challenge. It can also be riddled with inefficiencies and risk. The reality is many organizations do not have the staffing resources to operate a 24×7 security operations center (SOC). This limits their ability to respond to security incidents that occur in their environment in a timely manner. Ultimately, the longer an infected endpoint is attached to a corporate network—even if just for a few hours—the risk of malware spread, lateral movement, data leakage, or ransom exponentially increases.
Understanding the risk of delayed remediation and the benefits of rapid response, I recently worked with a customer to harness LogRhythm’s security orchestration, automation, and response (SOAR) capabilities to help them achieve 24×7 monitoring and response to malware threats. Here is how we did it.
Detecting the Threat
The first step was to create and tune AI Engine rules to analyze endpoint protection technology log data and spot indications of malware activity. In this particular set of rules, we excluded a select set of logs from endpoints that we don’t want to automatically isolate (i.e., critical servers). Don’t worry. We set up additional rules and alarms to notify an analyst of potential issues that should be manually handled.
Click on images to view larger
Automated Actions for Response
Once the rules were analyzing and alerting on indicators of malware activity, we set up the associated actions that will automatically execute once activity has been detected.
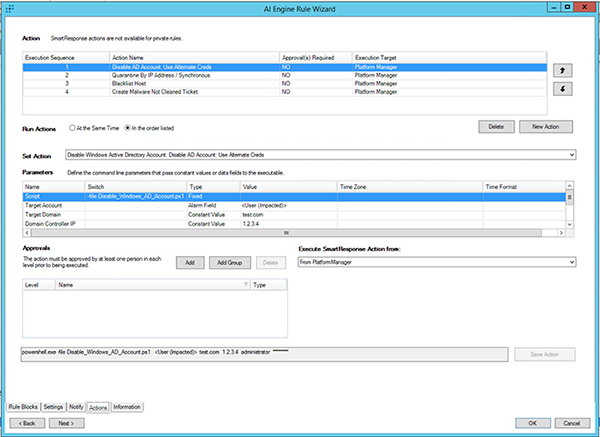
The first action is set up to automatically disable the Active Directory (AD) account of the user that has been compromised. This action ensures that the user’s access to other network resources is limited, thus protecting those network resources from potential misuse. The results of this script are written to a file for later use.
In the second action, LogRhythm instructs our network access control (NAC) system (in this example Cisco Prime) to query which switch port the compromised user is connected to and then issue a port shut, effectively isolating the host from the network. Again, the results of this script are written to a file for later use.
Because the compromised machine has wireless connectivity, we need to disable access to the wireless network to stop further spread of the infection and to effectively quarantine the breach. The third action automatically instructs our wireless platform (in this example Aruba) to blacklist the specific connection. The results of this script are written to a file for later use.
Finally, the fourth action will automatically send an email alert to the helpdesk ticketing system that will notify necessary staff that an incident has occurred and post-incident follow-up is necessary. This message will incorporate the insights from the files generated in the first three steps and provide crucial incident details to analysts. Details included in the email are:
- The name of the malware detected
- The compromised endpoint on which it was detected
- The user affected (including when their account in AD was disabled)
- The port switch that was disabled and when it was disabled
- The wireless network connection that was disabled and when it was disabled
Automated Detection and Response with LogRhythm
By the time the help desk team receives the email that malware has been detected, the appropriate immediate isolation actions have already taken place and the only task left for them is to perform incident recovery. Furthermore, all necessary information needed for recovery tasks is included in the email communication providing further assistance.
With LogRhythm, the entire process of malware discovery and response has been completely automated, effectively reducing organizational risk and maximizing the effectiveness of limited resources.
To see other ways LogRhythm is helping reduce mean time to detect and respond to threats, read more posts like this below or log in to the LogRhythm community.