Contributors to this blog include Nathaniel Quist and Dan Kaiser.
Last week, we provided background on Spectre and Meltdown vulnerabilities in our LogRhythm Labs Security Advisory on Spectre and Meltdown blog. In response to these vulnerabilities, LogRhythm Labs has developed content to assist clients in the detection of potentially malicious activities. This content includes two AI Engine rules and one PowerShell script—all designed to help you protect your environment from the Meltdown and Spectre vulnerabilities.
LogRhythm customers can use PowerShell scripts and custom AI Engine rules to determine if their organization’s security is at risk due to Meltdown and Spectre. If your network is open to attack from these vulnerabilities, PowerShell scripts and AI Engine can quickly notify you and help you detect potentially malicious activity.
These vulnerabilities impact a broad range of modern systems and can lead to exposure of extremely sensitive information. Implement the following AI Engine rules and PowerShell scripts to ensure your system is appropriately patched from the Meltdown and Spectre vulnerabilities.
The Scope of Spectre and Meltdown
Spectre and Meltdown are vulnerabilities found in most Central Processing Units (CPUs) available on the market today, including those manufactured by Intel, AMD, and ARM. The vulnerability allows for the processor to expose kernel memory to a user program running on the vulnerable system. The kernel level memory then becomes accessible and can contain information about any process currently active on your computer, including usernames and passwords.
Address Vulnerabilities with Microsoft Patches and LogRhythm AI Engine Rules
AI Engine is a fully-integrated component of your LogRhythm platform. Both LogRhythm AI Engine rules created in response to these vulnerabilities address the same target functionality: the manipulation of a Windows Registry value. As addressed by Microsoft Support, the only method by which systems can be patched against Spectre/Meltdown is to enable the operating system to control where and how speculative execution is allowed. Microsoft implemented this fix with patches for each of their major system families via: KB4056890 (Server 2016 and Win10), KB4056898 (Server 2012R2 and Win8.1), and KB4056897 (Server 2008R2). Additional information about these patches can be found here.
The Microsoft patches add two DWORD values to the Registry key “HKLM:\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management”
These two DWORDs are:
- FeatureSettingsOverride
- FeatureSettingsOverrideMask
LogRhythm AI Engine rules are designed to identify if the DWORD FeatureSettingsOverride value is manipulated from a value of “0” to a value of “3.” A value of 0 indicates a system is currently protected against these vulnerabilities, while a value of 3 represents a system that is still vulnerable. Although both AI Engine rules can fire on the same event, the purpose of the two rules are to determine the type of log source used by a client to identify Registry key value changes.
AI Engine Rule 1: Spectre Registry – RIM
The first AI Engine rule, Spectre Registry – RIM, is designed specifically to use LogRhythm’s System Monitor tool: Registry Integrity Monitoring (RIM). RIM monitors a series of pre-specified Windows Registry keys and provides actionable metadata regarding the keys’ creation, modification, and deletion. As such, it is required that the key “HKLM\System\CurrentControlSet\Control\Session Manager\Memory Management” be added to the LogRhythm RIM policy, which is assigned to the LogRhythm System Monitor Agent on each Windows system being monitored for this vulnerability.
As seen below in Figure 1, the AI Engine rule is designed to trigger when the DWORD FeatureSettingsOverride is modified to have a value of “3,” meaning your system is no longer protected against the Spectre Vulnerability. If the Registry key was maliciously altered to this value, and the system subsequently rebooted, a user or process kernel memory could be inappropriately accessed.
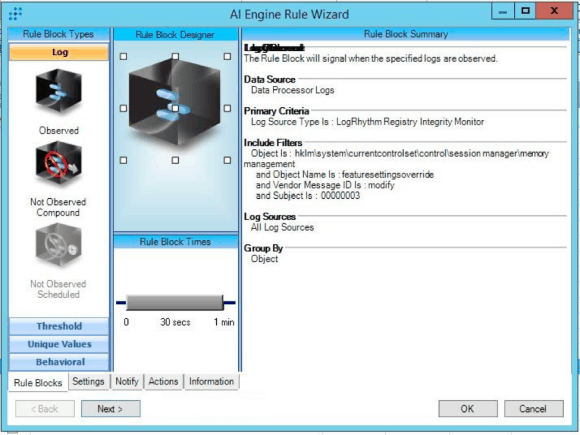
Figure 1: Spectre Registry – RIM AI Engine Rule
AI Engine Rule 2: Spectre Registry – SysMon
While Spectre Registry – RIM is focused on LogRhythm’s RIM functionality, Spectre Registry – SysMon is focused on the usage of Microsoft’s SysInternal tool: SysMon. SysMon is a very powerful tool that allows for nearly every aspect of a computer to be monitored and logged to a Windows Event Viewer log file. This includes process start and stops, parent process start and stops, MD5, SHA1, SHA256, IMPHash collection, and Windows Registry monitoring. The LogRhythm platform is able to collect, parse, and correlate metadata collected from the Microsoft SysMon tool.
Spectre Registry – SysMon is designed to trigger when the DWORD value of ‘FeatureSettingsOverride’ has been modified. Since this value must be ‘0’ to be considered a protected system, a potentially malicious instance could occur if at any time that value is altered. While this particular rule does not currently contain the actual DWORD value itself, Microsoft SysMon is very easy to configure and use, even with little resources—allowing for the ability to monitor Windows registry keys.
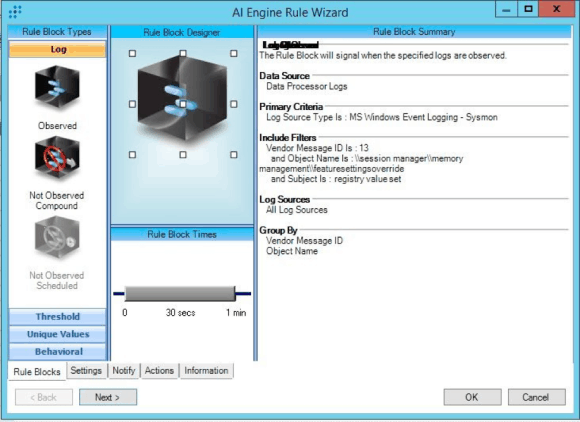
Figure 2: Spectre Registry – SysMon AI Rule
Using LogRhythm PowerShell Script to Ensure Your System is Patched
LogRhythm Labs created a PowerShell Script designed to perform the following functions on a system:
- Check to see if your system is vulnerable to Spectre
- Check to see if your system is patched against the Spectre vulnerability
- Install Microsoft SysMon
- Configure Microsoft SysMon to monitor the Windows Registry Key, “HKLM:\SYSTEM\CurrentControlSet\Control\Session Manager\Memory Management”
The PowerShell script will download and install the official Microsoft Speculation Module “Get-SpeculationControlModule” to confirm if your particular system is vulnerable to the Spectre vulnerability. Next, the system will check to see if Microsoft SysMon is currently installed on your system. If so, the PowerShell script will provide you with a SysMon configuration log designed to monitor the memory management Registry key. If Microsoft SysMon is not installed, the script will download Microsoft SysMon version 7, prompt you to accept the EULA, and install and configure SysMon to monitor for the memory management Registry key.
After the script has completed, SysMon will then be running the system. However, the LogRhythm platform will not be configured to collect the SysMon Logs from the system. Please use the following guide to configure the collection. If you’re already using SysMon, you can skip down to the Downloads section.
Configuring LogRhythm to Collect SysMon Logs
If you are not using SysMon, you may need to configure your LogRhythm platform to collect SysMon logs. The following is an example of a default configuration of a log source configured to collect using the “MS Windows Event Logging – SysMon” log message source type. In this instance, you can learn how to collect the SysMon output from a Microsoft Windows Server 2012 R2 x64 host, using the default SysMon XML configuration.

Figure 3: Log Message Source Properties Basic Configuration Window
For the Flat File Settings, you will want to ensure that the File Path is specified correctly:
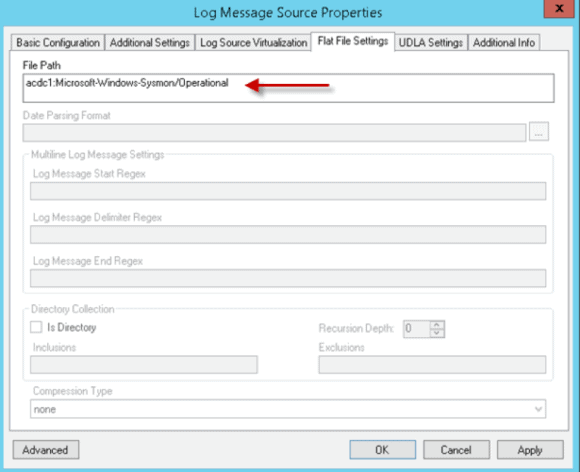
Figure 4: Log Message Source Properties Flat File Settings Window
Note: The file path is found by opening any event contained in the Event Viewer > Applications and Service Logs > Microsoft > Windows > SysMon > Operational log. After clicking the Details tab and selecting the XML view, you simply need to note the channel name and copy/paste this into the Flat File Settings > File Path field.
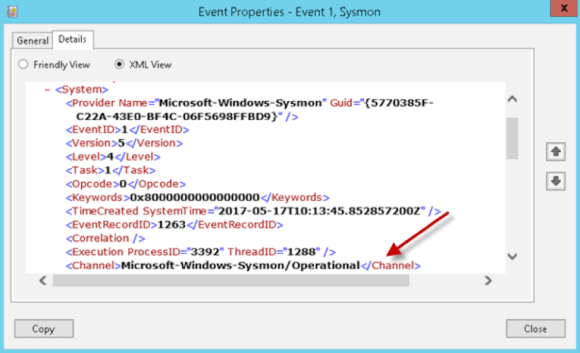
Figure 5: Event Properties XML View
Downloads
When successfully exploited, Meltdown and Spectre vulnerabilities can result in the exposure of privileged information and endanger your organization. You need to be prepared to patch and continuously monitor your system. LogRhythm AI Engine and PowerShell script can help streamline the patching process, enabling you to protect against these vulnerabilities.
Download the LogRhythm AI Engine rules and PowerShell script to secure your network from Meltdown and Spectre vulnerabilities:
AI Engine Rules
Download the Spectre Registry – SysMon AI Engine rule here.