As a cybersecurity pro, you already know that a user is both an organization’s greatest asset and its greatest vulnerability. Users have access to sensitive information and systems with the ability to inflict immense damage to an organization.
Insider threats are unique in that they render many traditional security technologies and controls obsolete. These threats often have a knowledge of established security programs and use legitimate credentials and permissions to access or alter sensitive materials.
To make matters worse, security teams face in-company political barriers. Traditional analytics tools don’t typically have what it takes to effectively baseline and monitor end user behavior.
The Challenge: Detecting an Insider Threat Attempting to Exfiltrate Sensitive Data
Recently, a customer came to me with a unique challenge. He wanted to be able to detect an insider threat attempting to exfiltrate sensitive data from within a completely isolated network. And when I say isolated I mean isolated—this network has no connection to the internet or outside networks and its physical security is top notch.
Despite the first-rate security controls in place, he knew that he had to be prepared for anything, no matter how improbable an attack might be.
My team and I sat down and began to think like a bad guy. We used our knowledge of the customer’s environment—as an insider threat would—to come up with a variety of use cases to defend the network.
Below you’ll find the details of one of the use cases that we came up with.
Setting the Scene: Thinking Like a Bad Guy
In this particular use case, the insider threat creates a dummy user account and gives this new account privileges to access a file server by adding him to a local or a domain admin group. From there, the dummy account would be used to access and copy confidential data to the rogue insider’s workstation. Unable to exfiltrate the data digitally, the rouge insider will print the document through his local printer. Like any good thief looking to cover his tracks, he’ll attempt to then delete the dummy account as if it never existed.
UBA in Action
Typically, this type of attack would be difficult to detect with traditional perimeter defenses and security analytics solutions. Luckily, we have the LogRhythm NextGen SIEM Platform.
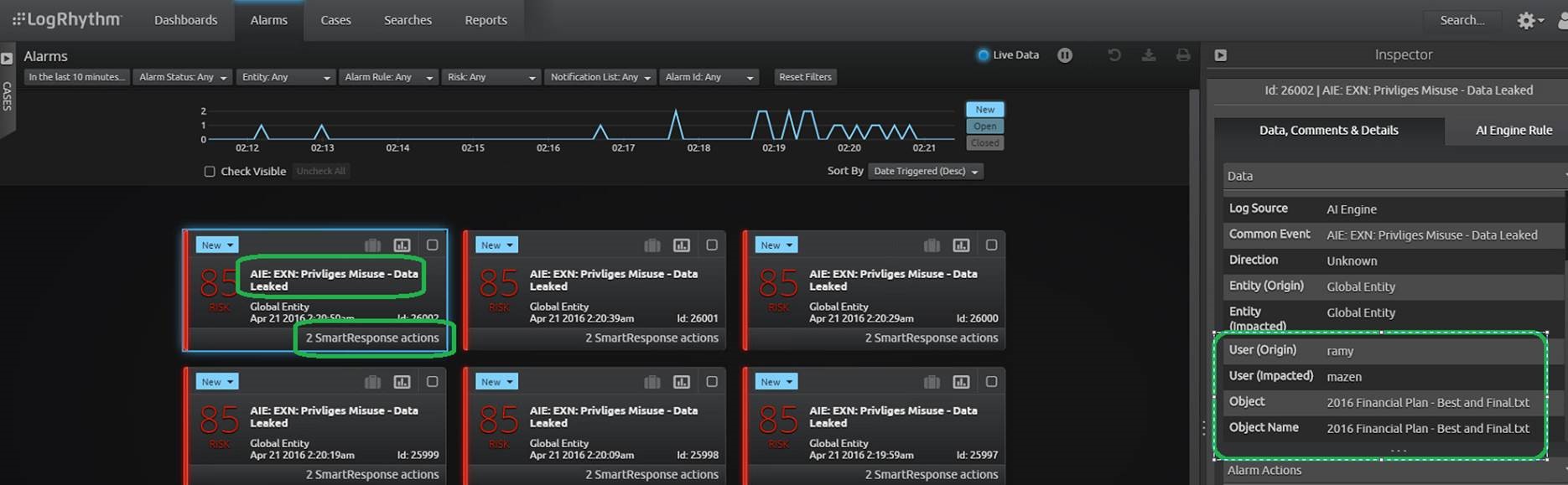
In LogRhythm, I configured the analytics algorithms and set our use case into action. Once LogRhythm detected that data was being improperly exfiltrated, the following alarm was generated.
Click images to expand
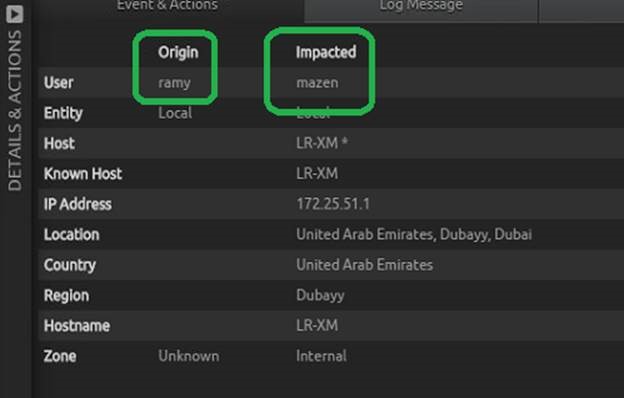
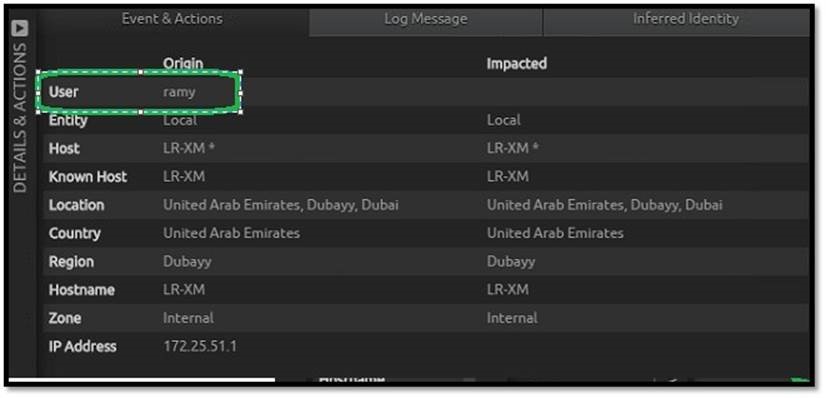
The high-priority alarm indicated privilege misuse and subsequent data leakage. From the inspector pane, we see the account responsible.
This account seemed to be a privileged user with legitimate access and credentials. A quick check against employment records would indicate that the privileged user does not work for the organization.
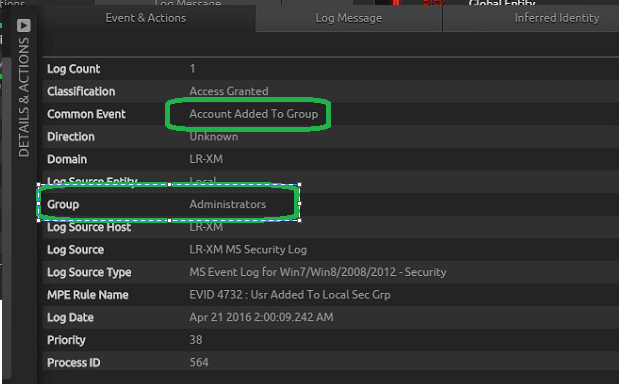
Further drill-down revealed that the bogus account was actually created and added to the “Administrators” group by a privileged admin.
Now that we know a privileged admin created the dummy account, the next question is: What did this admin do with the newly created user account?
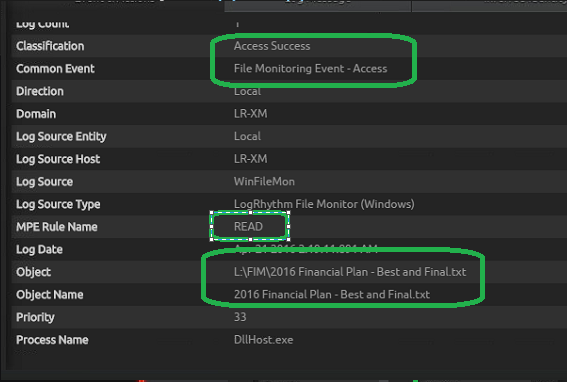
With just a click, LogRhythm revealed the account connected to a critical server and copied confidential data to a local machine. Right in the web UI, both the machine and the name of the confidential data is revealed.
LogRhythm also detected that data has been leaked over the local printer connected directly to his workstation or laptop. We are able to see what account was used to print the sensitive data, as well as which file was printed, the number of pages printed, and the name of the printer used.
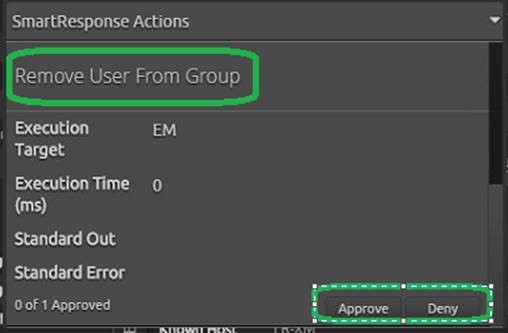
After we investigated the incident and verified a response was warranted, we used LogRhythm’s SmartResponse™ feature to spring into action. With two quick clicks, we approved the SmartResponse actions associated with the alarm, immediately adding the user to a watch list disabling the account and removing him from the admin group.
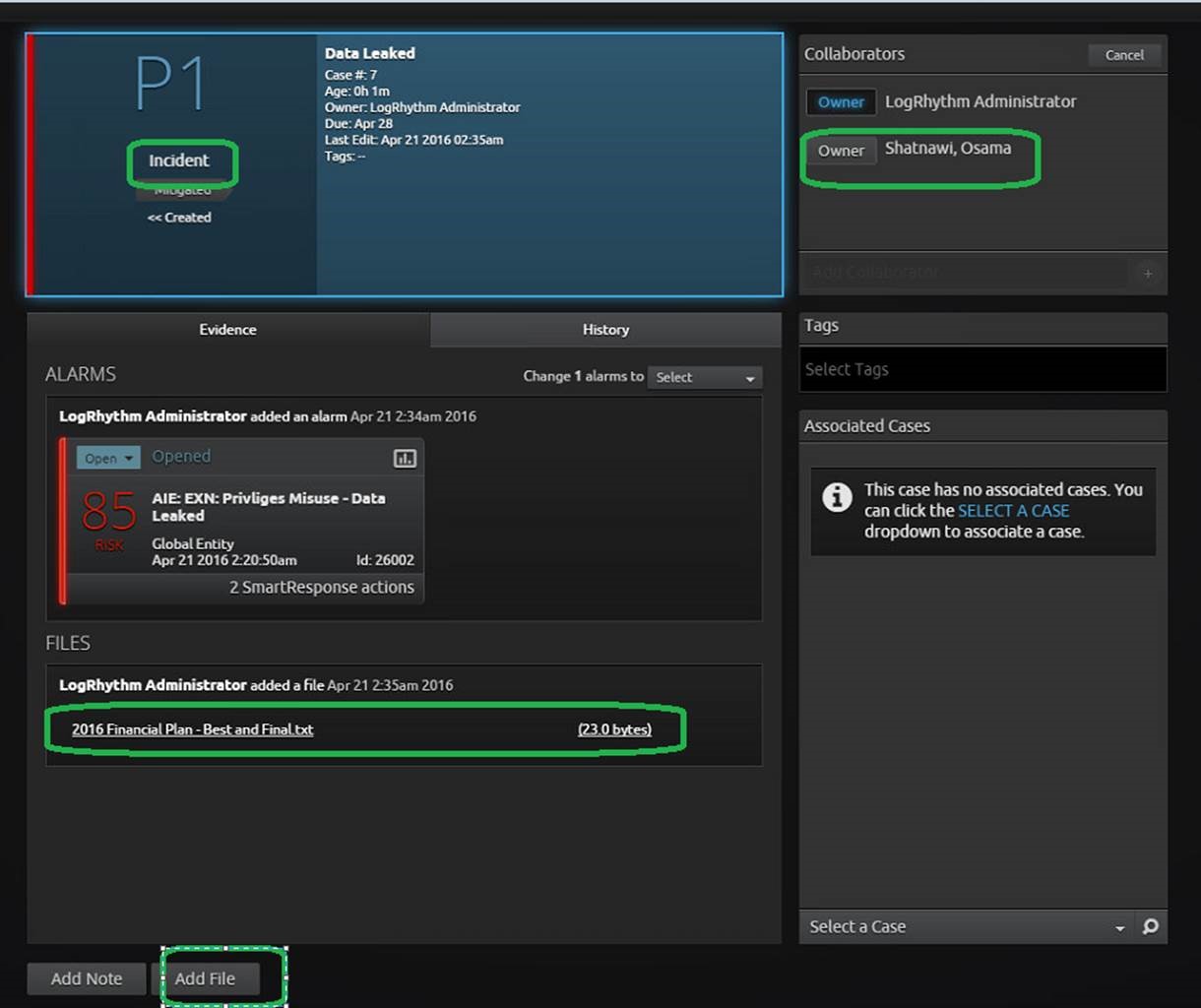
After confirming that the account was disabled and removed from the privileged group, I created a case and added all of the relevant alarms files. I escalated the alarm to a P1 and added a manager to the case to perform a comprehensive incident debrief. At this point—if this case was real—authorities would be contacted and the rouge insider detained.
Breach Averted
This use case is just one of many examples of how advanced security analytics can track end user activities and correlate with other network and endpoint data to allow expedient, automated response.
In the fight against insider threats or any other threats, the faster you can detect and respond, the better off you’ll be. I challenge you to continuously prepare for the “impossible” by thinking like a bad guy. Generate a number of use cases and then implement proactive defensive rules and alarms to meet those challenges.