Compliance doesn’t guarantee prevention against a breach, and it never will. Various frameworks, legislation, and regulations are meant to lay part of the foundation for organizations to build and expand on; though this rarely is the case. While different industries demand different compliance commitments, foundational approaches to manage compliance are similar across the board.
In today’s world of scare tactics, growing threats, and different vendors pushing their version of the “next big thing,” you may be buying various tools to strengthen your organization’s security. But if you don’t understand the purpose of each tool and how they align with your overarching security goals, you might be on the path to alarm fatigue and inefficient processes.
You need to start with the basics. Beyond knowing the tools you need to ramp up your security, you must understand where your organization lies with the maturity of its security operations.
Aligning Compliance Maturity with Security Maturity
When we talk about tailoring compliance to a single company, there are so many variables to consider. No two companies operate the same or have the same priorities. The common result for many organizations is to implement just enough practices to check the box, effectively eliminating much of the value compliance is designed to drive. The same holds true with compliance efforts for organizational security. Real-world threats advance faster than the adaption of any framework or set of best practices, leaving even the most compliant organizations exposed.
Enter LogRhythm’s Security Operations Maturity Model — a framework that helps you assess your team’s effectiveness in a variety of areas, including Threat Lifecycle Management (TLM) capabilities and organizational/risk characteristics that align with compliance maturity. When done well, TLM helps teams more effectively realize foundational workflows that determine organizational mean time to detect (MTTD) and mean time to respond (MTTR) to threats.
It’s been well established (and documented by hundreds of tech vendors’ blog posts and field experts) that compliance does not equal security. However, compliance can drive security initiatives from both a budgeting and prioritization standpoint.
So how does compliance maturity align with security maturity? And how do you build that connection to bridge the gap between the two? Ideally, as your organization strengthens its security posture, it will become more compliant as a byproduct. When the foundational aspects of compliance are so immersed in your organization’s operating procedures, audits turn from a burden to a benefit creating business efficiencies.
As it relates to security, an audit is a snapshot of a much larger security mission. But when you introduce compliance initiatives to help drive the security roadmap from the beginning, the benefits are apparent immediately in processes that don’t hinder performance, but enhance it.
Applying LogRhythm’s Security Operations Maturity Model
Below is an example of results gathered during an initial LogRhythm SOMM assessment and an actionable roadmap of goals to show how you can strengthen your security maturity.
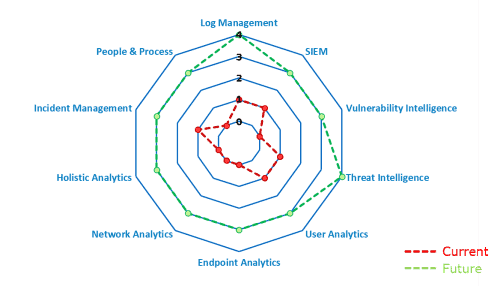
Figure 1: A radar chart of current and target SOMM levels shows how you can strengthen your security maturity over time.
Here’s what we learned from the SOMM, with a compliance perspective.
Level 0: Blind
During the define and design phase of any organization’s road to compliance maturity, teams spend a significant amount of time developing policies to conform with one or many compliance frameworks, regulations, and legislations. A first-time adopter organization entering an audit or pushing policies internally is practically blind, as are the individuals it’s trying to convince to follow. If you fall into this group, you are most likely attempting to be prevention-oriented, developing restrictive policies, and buying technologies quickly to make your organization more “secure” without understanding what value you are gaining. In compliance terms, these technologies are not offering any value.
Level 1: Minimally Compliant
Whether it is mandated by your organization’s management, board, industry, or customer, if you are at this level, you likely have adopted some security-directed framework as a best practice framework or invested in other efforts to raise your organization’s security posture. This generally requires that you buy a litany of tools mandated by a best practices framework or policy. Many of these tools are expensive and require personnel and processes to measure effectiveness and provide value.
Having the tools in place can significantly reduce risk, but only if they are tailored to your organization’s policies and operating procedures (hopefully based on generally accepted best practices), not to mention they need to have (somewhat) dedicated personnel actively reviewing their outputs. At this point, your organization probably does not have dedicated resources to manage the tools properly and may be just checking a box from a compliance standpoint. Your organization is acting reactively, so it’s still basically blind, but sees the need to invest in resources.
Level 2: Securely Compliant
This is where we begin to see the transition from efforts focused squarely on meeting compliance demands to efforts that increase the overall organizational security posture. If your security maturity is at a Level 2, the foundation is set and your organization is seeking process efficiencies, optimizations, and assurances across different verticals. Personnel understand their roles, and tools are operating in line with established policies and practices. This is where many organizations expand the best practices and foundational steps they’ve adopted from various compliance initiatives.
If you are at a Level 2, your company is tailoring its tools and gaining more proactive, value-driven outputs. Many organizations stop here, as they’ve proven they are no longer doing the bare minimum. This is good, but it’s not great — as the goal and this level for your organization is compliant, but not necessarily secure.
Level 3: Vigilant
At this stage, your tools are targeted, your organization performs a variety of assessments on an ongoing basis, and you are establishing metrics for continual improvement. Now that your organization is probably “compliant as a byproduct of security,” you are likely focused on continued enhancements, holistic visibility, and overall development of your organization’s resources.
Well-established and repeatable processes use tools tailored to specific organization goals, and proficient personnel make audits an ease, far surpassing the minimum standards requirement. This is where compliance and security split, and initiatives are purely based on furthering the operational effectiveness of existing tools to become resilient. Metrics are now established and communicated to the broader audience within your organization. At this point, the goal is further improving the tools.
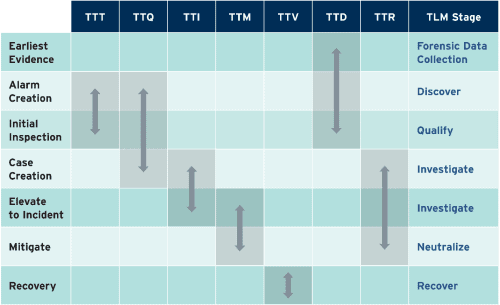 Figure 2: Seven key metrics for measuring the effectiveness of TLM
Figure 2: Seven key metrics for measuring the effectiveness of TLM
Level 4: Resilient
Finally, an organization that is resilient from a security operations perspective, is predictable. At this level, your organization has established playbooks and matured processes to breed a cross-organizational commitment to security. An investment in automation allows your security team to do what it does best — analyze anomalies, secure the organization, and secure the human element in a proactive manner.
If you are at this level, proactive compliance has been and remains a way of life for your organization. It comes naturally and is no longer a point of contention. Your organization is always informed, and transparency is fluid. This is a level that every organization should strive to achieve.
Finding a Balance
So, does compliance equal security? No, and why would it? Any framework you find to use as your basis is also available to your adversaries. If your organization is simply meeting the minimum standards, the other team already knows your plays.
So does maturity help your organization stay ahead of possible attacks? We’d certainly argue it could.