Over the last few days, we have been identifying another new phishing attack attempting to steal domain credentials. This particular example is isolated around the jimdo.com web hosting service. If you are not familiar with Jimdo, they essentially allow anyone to create their own free website within the Jimdo domain. Jimdo HQ is in Hamburg, with other locations around the globe, including the US.
Like any web hosting service, fighting against malicious use of its services is a constant battle. The example identified below was reported to Jimdo on July 7th. Unfortunately, with Jimdo, reported malicious websites are rarely taken down in addition to being “the easy way to create your own (phishing) website”.
The Bait
User receives the following phishing email. The sender address is nothing noteworthy in this particular example. Typical for such emails to come from spoofed or hijacked email accounts, both personal and corporate.
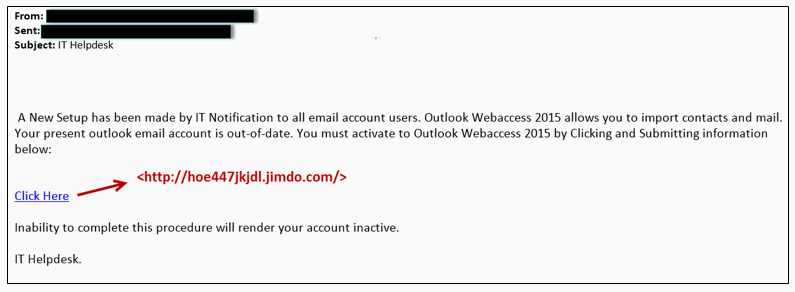
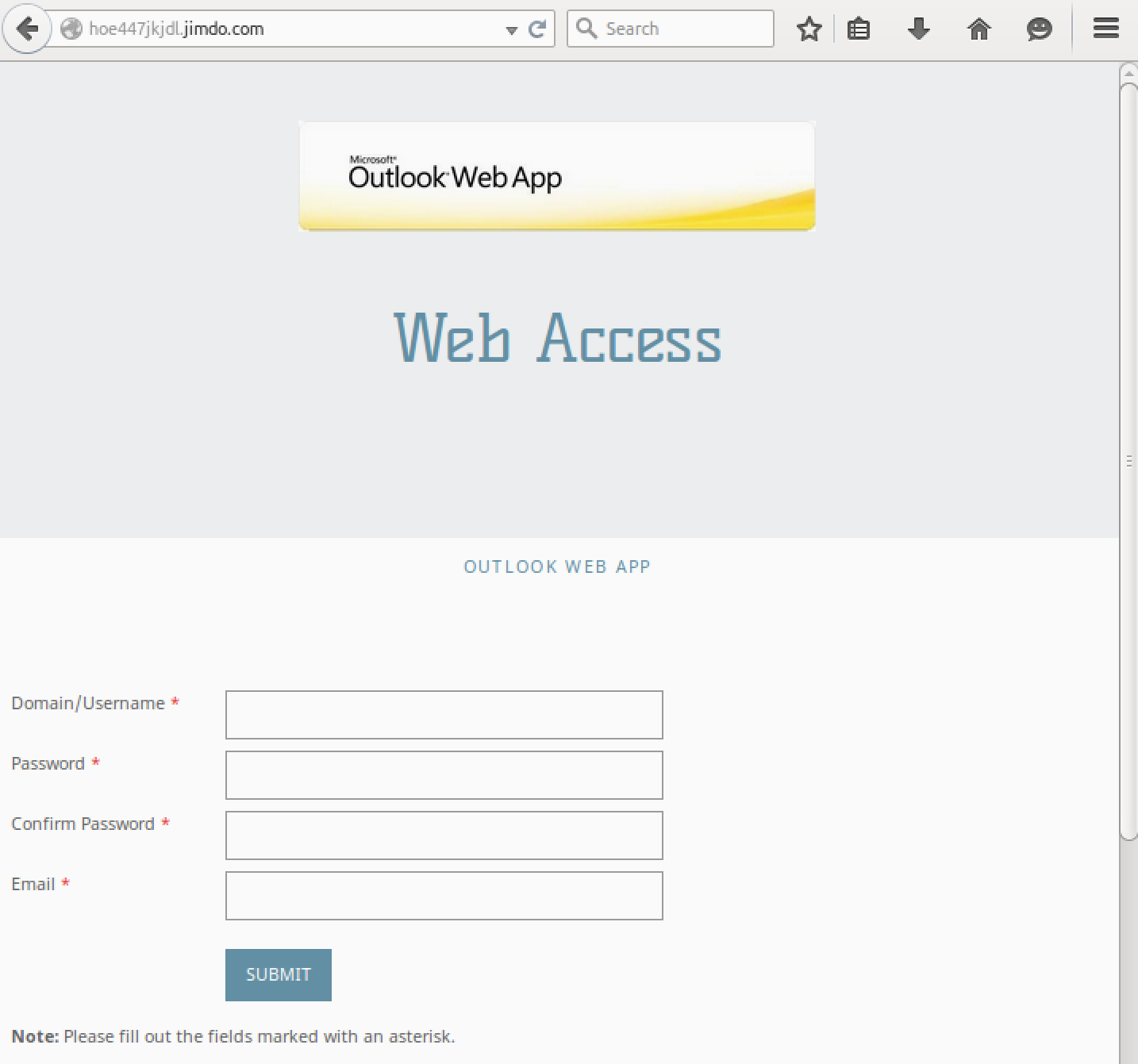
Clicking the “Click Here” link, the victim navigates to the site hxxp://hoe447jkjdl.jimdo.com that happens to provide an amusing result, as seen below.
Detection
VirusTotal scan can be found HERE.
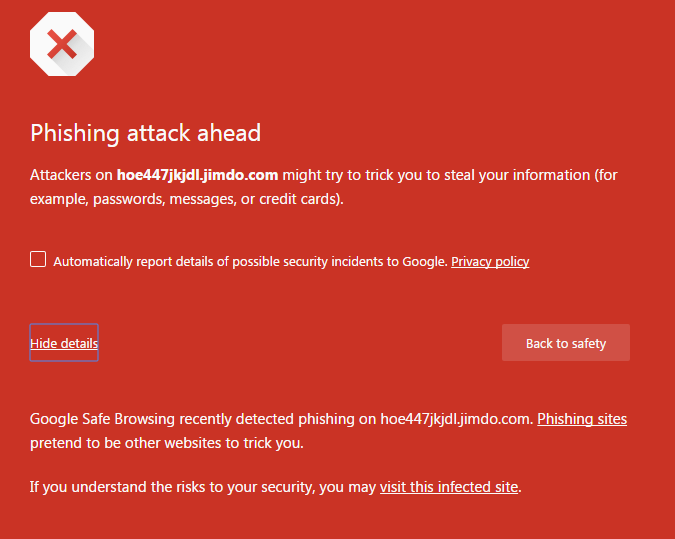
Chrome has already classified the site as phishing and provides its user base the following warning:
Spotting the Phishing Attempt
The site is clearly attempting to steal domain credentials from unaware users. While the site looks formatted rather well, Jimdo requires a banner at the bottom of their free pages that are easy to spot.
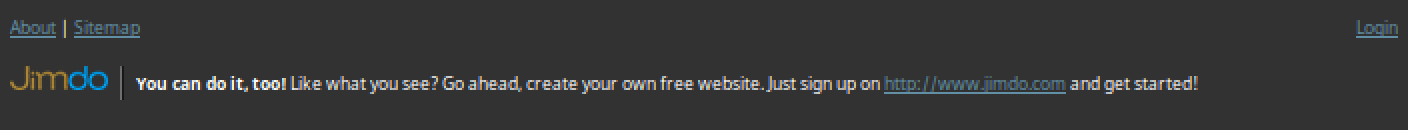
In terms of training users to identify such phishing attempts, this is a great example. Focusing user training on spotting those malicious “red flags” is a beneficial way to limit their risk to the organization. Such flags can focus around sender address, URLs, and possible attachments. While many attacker techniques commonly spoof or hide such flags (email spoofing, URL redirecting, etc.), it is still a great place to start educating your users.
An Update from Jimdo
LogRhythm began to receive communication from Jimdo’s “Abuse Assassin,” Peter Rudek on July 29th, with the following official response on July 30th. While the Jimdo team was unable to share specifics on their defense, they have provided this information about their anti-abuse practices and incident response process.
- We’re sourcing moderation and Threat Intelligence Providers
- The data we collected over the years allows us to develop in-house-tools suited to the patterns the attackers are using on our system.
- As these suspects are changing their patterns fast, that’s where our manual(i.e. human intelligence) kicks in to analyze the change and adjust our automated-systems accordingly
Comparing our auto-elimination-count with the alerts we receive via various channels (blacklist-aggregators, anti-malware-companies, certs, copyright-holders and individuals) I’d say we have approx 80% recognition-rate. After an alert is received it shouldn’t take more than 20min to very few hours (depends on the time of day + the load) to have that site taken down.