Contributors to this blog include Andrew Hollister and James Carder.
As security and IT teams are dealing with the complications of maintaining security and operations of the business during the stay-at-home order due to the coronavirus and are now managing a remote workforce, new challenges may arise due to limited visibility of your cloud environment. We have been listening, and we hear what you are going through. To help ease some of the challenges, LogRhythm is offering a promotion for remote workforce visibility using LogRhythm Cloud via a monthly subscription for a limited time.
The goal of this limited-time offer is to help ease the pain for security teams by quickly and effectively restoring visibility. With LogRhythm Cloud, your team can have the technology in place to address key remote workforce security use cases — without needing to establish a long-term contract.
How to Maintain Security Visibility with a Remote Workforce
As you transition from operating on-premise (in the office, data centers, etc.) to a remote operation (i.e., working in the cloud from a work-at-home set-up), maintaining security visibility so you can continue protecting your business in this new normal is likely at the top of your priorities.
The world has never dealt with anything like the coronavirus pandemic before. Most of us have never tested our business continuity and disaster recovery plans to this level. When working in a remote environment, you may be asking the following:
- Will my infrastructure support it? Can we operate our infrastructure in this new way?
- If not, then what changes do I need to make?
- How do I sustain the productivity of my workforce?
- Are my security controls and infrastructure built for this, or am I taking additional risk?
- Do I even have security visibility anymore?
- How do I handle operational logistics that require folks in the office or alternative measures when using third parties that are no longer in the office?
- What does BYOD mean now? Has that definition changed for our organization?
- How do I keep my employees safe?
Attackers, as many of us know, love using crisis, emergencies, and the latest global news and events to their benefit. This is nothing new. Attackers masquerade as legitimate organizations, with legitimate websites, and legitimate information. We’ve seen them quickly adjust their tactics to prey on those of us with interest in information related to the current pandemic and hone their attack plans for that.
Security is never something to take lightly — especially now. But we know that some businesses are making decisions based on availability and operational production. Security then falls to the wayside. They may make concessions that increase security risk. In such cases, companies are relying more on monitoring, detection, and response as a compensating control.
Gain Immediate Visibility into Your Remote Workforce with LogRhythm Cloud
With this promotion, new customers can access the LogRhythm Cloud platform with a monthly subscription for a limited time. Focus on technologies that are critical in remote workforce monitoring, such as collection and correlation of endpoint (employees working from home), VPN and other pertinent infrastructure data (employees connecting back into the corporate network), identity and access management (where to, from, and how employees are authenticating and accessing things), and collaboration technologies like Office365 and Teams, Zoom, and Slack.
With LogRhythm Cloud, you will have full access to the LogRhythm Cloud product feature set to drive robust security analytics, security orchestration automation and response (SOAR), and cloud SIEM for the remote workforce visibility use cases.
How LogRhythm Cloud Helps Support Your Security During Remote Work
There are several key areas of LogRhythm Cloud will give your team the visibility it needs to continue to secure your organization during a work-from-home scenario: endpoint, infrastructure, and collaboration. Many of these areas also provide high value to your IT operations team while they monitor the availability of services to the remote workforce. Let’s explore the technical details further.
Endpoint
With all endpoints located at employees’ homes, visibility of what is happening on those endpoints is paramount. The quick win here would be to ensure that any endpoint detection and response (EDR) product in use is correctly configured to log activity, and that those logs can be sent back to the central management hub of the EDR solution, whether that is in the company data center or delivered as a software-as-a-service (SaaS) offering. In addition, tools such as Microsoft Sysmon and the local Windows System Event logs can provide additional insights into user activity.
Infrastructure
Depending on the organizational mix of hosted and cloud services, remote workers may be accessing company resources such as data stores and productivity applications in different ways. Users in a heavily on-premise-based organization will likely be using resources via VPN, so logging activity from across the VPN will provide ideal visibility. In a heavily cloud-based architecture, organizations will likely use cloud access security broker (CASB) offerings, or perhaps other cloud-based access services. These have their own logging facilities and can also be integrated with SIEM. IAM services also provide critical visibility into user behavior, particular when endpoints are remotely located and Active Directory logs can no longer provide the core visibility into user activity.
Collaboration
The use of SaaS offerings, and in particular conferencing, meeting, and chat services has spiraled in the remote working era. Your organization has likely increased its use of these services, and in some cases, you may have had to adopt services quickly to keep your business running. Visibility into these services is critical to keep your organization safe and manage risks, such as data loss, insider threats, and other compromises.
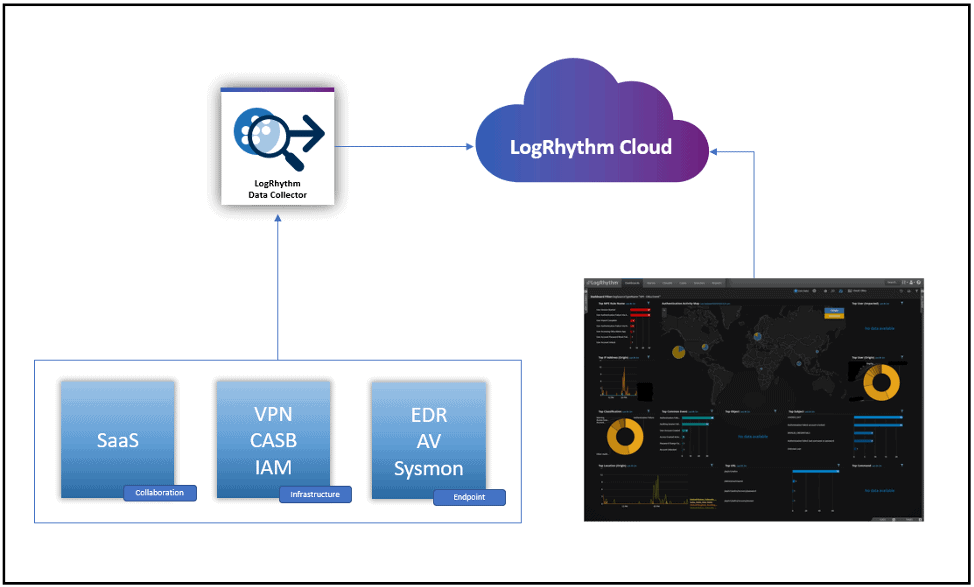
Many of these log sources are relatively low volume, but they provide high-value insights that can assist your security and IT operations teams in delivering an effective and secure remote working capability.
As an example, here are some screenshot examples from some already-implemented remote workforce monitoring at LogRhythm:
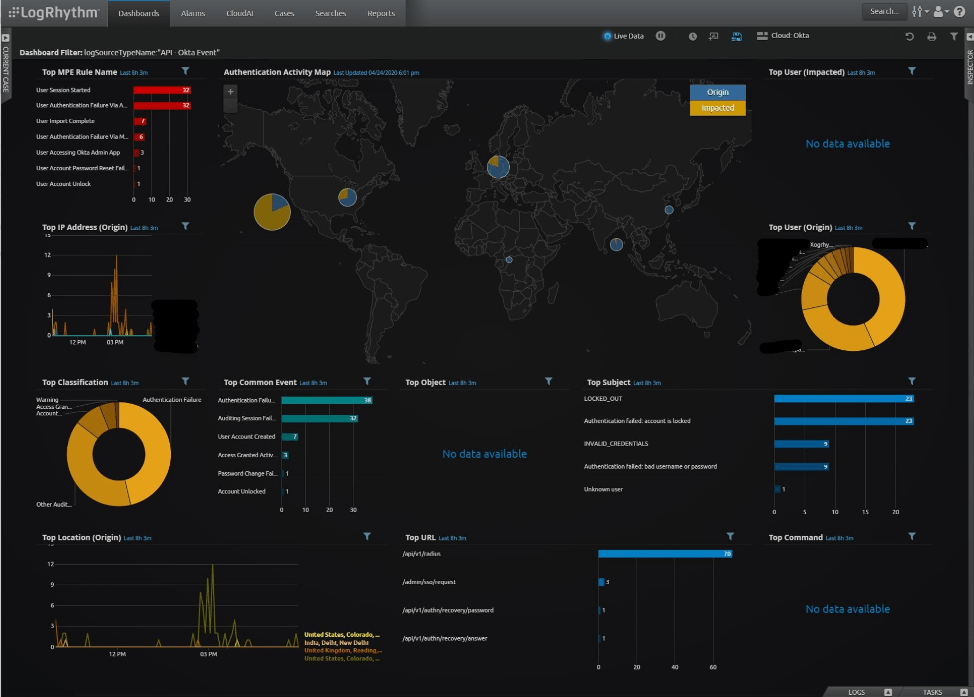
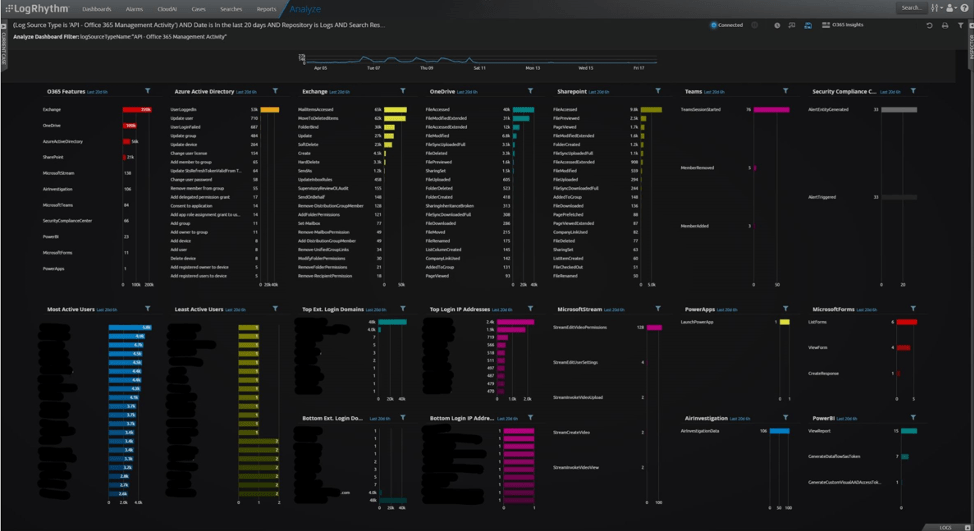
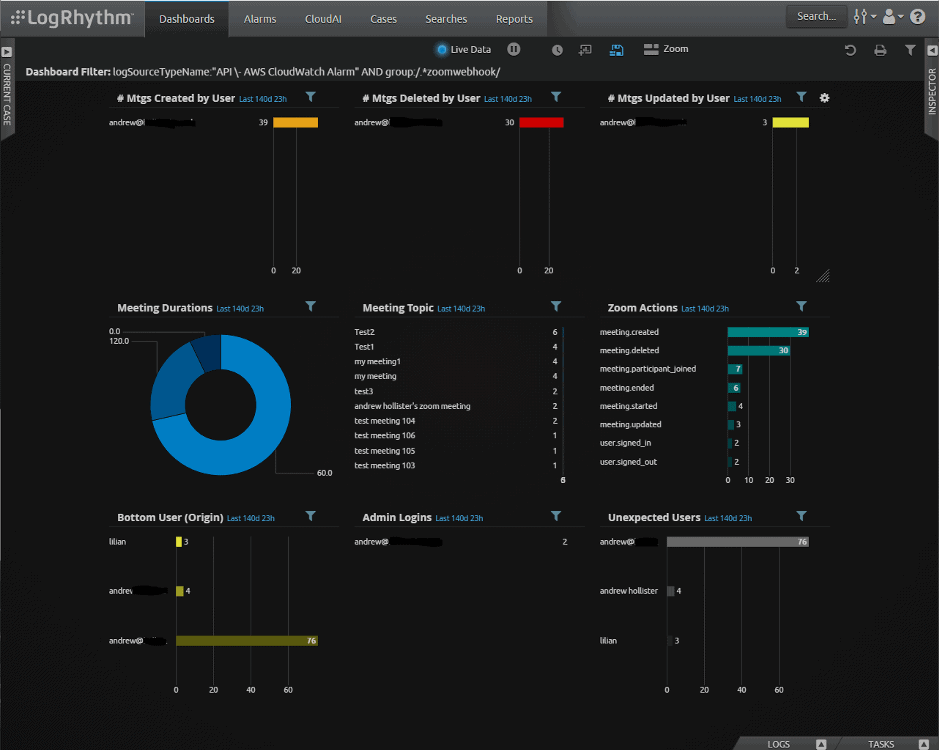
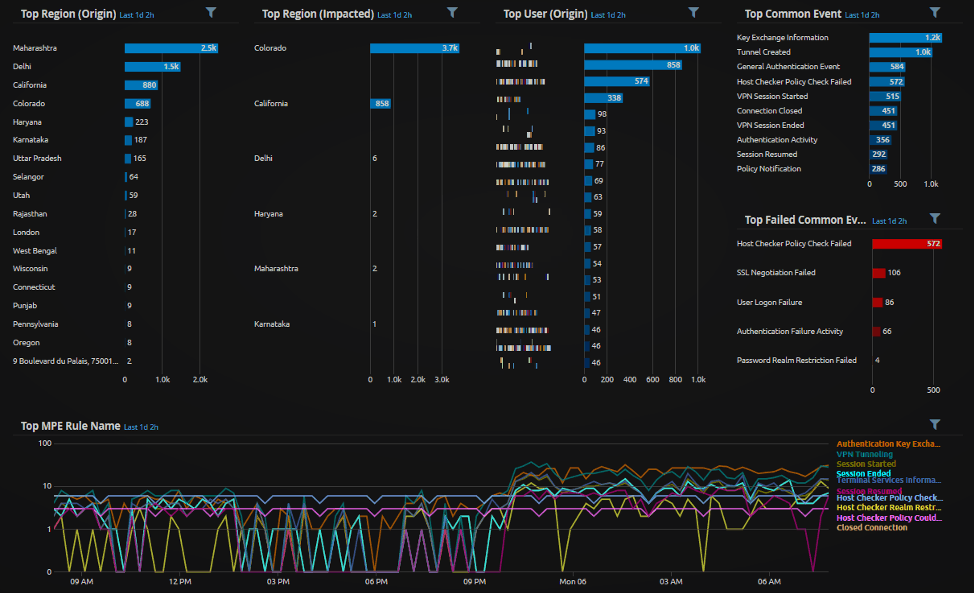
Once your team has insight via dashboards such as these, the focus will often turn to detection and response. LogRhythm Cloud provides all the tools your organization needs for threat hunting, threat detection, and response. You also get access to a huge amount of existing content (over 1,650 out-of-the-box rules and modules), in addition to custom analytics for the remote environment.
Alerts might range from unexpected users joining a Zoom meeting to VPN connections from previously unseen areas of the globe. Using dashboards to gain insight into the remote habits of a workforce can also provide useful pointers for where additional alerts will give the most value.
All the features of the LogRhythm platform are supported in this offer — from log collection of all technologies supported by LogRhythm in the endpoint, to infrastructure and collaboration, search, dashboarding, analytics, alarms, response, and Case Management, in an easy-to-use, integrated interface.
Gain deep visibility into your remote workforce and protect your organization with LogRhythm Cloud.
Get Started
This promotional offer is available to those who are looking for visibility into their remote workforce as well as existing LogRhythm customers. For more information, please request more information below.
