Ransomware’s Rage
We have built economies and business infrastructures on modern electricity utility companies. These companies touch and power our lives on a daily basis. The ubiquity and vast amount of sensitive data they store, combined with our deep dependence on them, make them major targets for cyberattacks. In this blog, we dive into LogRhythm NextGen SIEM for Electricity Utility use cases.
Ransomware attacks have cost electricity companies in dollars, downtime, and reputational damage. The Lansing Board of Water & Light (BWL) was targeted with a sophisticated attack, costing them $2 million dollars. That same year, a major electricity supply provider in Johannesburg was attacked, resulting in localized blackouts for a sustained period of time. Both of these incidents demonstrate the importance of providing stringent cyber protection to critical infrastructure facilities, like electricity power systems. These two examples are just a small sample of incidents, while there are other incidents that can cause severe impact to physical electricity devices and gravely impact human life.
Ransomware-as-a-service (RaaS) has also grown, given how ransomware has proven to be a highly lucrative business. RaaS is a business model in which ransomware developers lease ransomware variants, allowing malicious actors to quickly launch ransomware campaigns without needing much skill or time to develop their own.
Now the big question is how can electricity utility organizations effectively manage today’s risks while speeding up detection and responding to modern threats? Let’s dive into practical use cases specific to electricity utility organizations, based on the most recent real-world attacks, such as how to detect ransomware.
Use Case: Detect Physical Access Control Violation
Critical infrastructure providers such as electricity suppliers deliver essential services for communities across the world. Electricity generators and providers must make sure reliable services are supplied on a 24×7 basis, making Physical Access Control one of the most important access controls for this sector. It is critical to authorize only the personnel that is required to have physical access to electrical equipment, and only authorize activity executed by authorized personnel. A continuous review on physical access logs for all personnel and their activities is also a must for electricity utility providers.
The Challenge
Security threats don’t originate exclusively from cyberthreat actors, and the most impactful threats in security actually originate from social engineering. The simple gesture such as holding the door for someone without verifying their identity can result in an impactful attack of similar or even greater scale than one from cyberthreats. It is important to provide security awareness training for every employee to ensure they are aware of and able to detect possible instances of a threat actor attempting a social engineering attack. A combination of awareness training on physical attacks and cybersecurity threats can significantly reduce the chances of an attack from the human element.
The Solution
LogRhythm augments control on physical access by monitoring for any access provisioning activities within the environment. Further, authentication or access activities to both physical and electronic access points are monitored. Privileged accounts or groups, both by default or defined by the organization, are also monitored for access provisioning, authentication, and access activities due to their impact within the environment. LogRhythm’s module content provides reports, alerts and investigations, enabling the organization’s periodic access review process. LogRhythm both augments and directly addresses control objectives within Physical Access Control by alerting and reporting on access deprovisioning due to reassignment, transfer, or termination. This enables the organization to measure policy adherence for timely modification or removal of access.
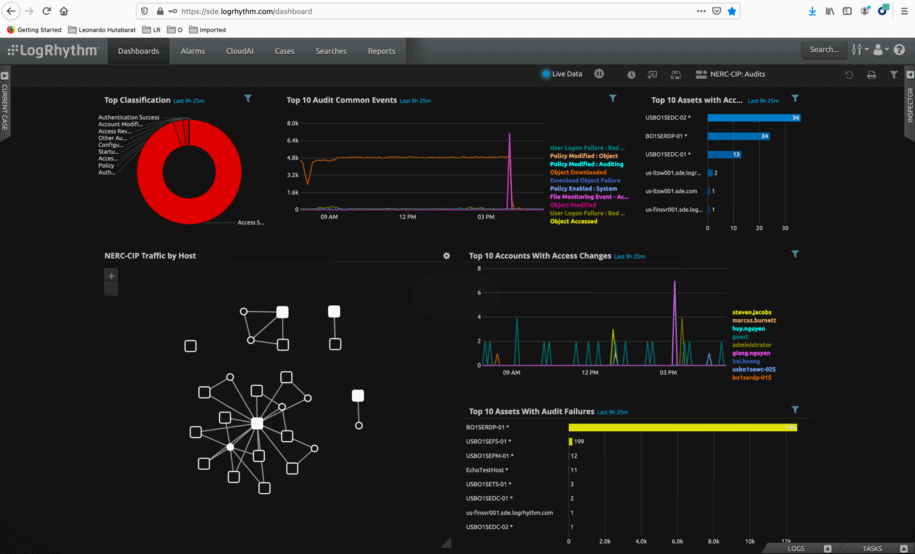
LogRhythm utilizes AI Engine (AIE) use cases to detect Physical Access Control Violation such as when someone breaks the security glass on any physical barriers. Once this happens, AIE will trigger an alarm with Risk Based Priority (RBP) based on the risk value of that incident.
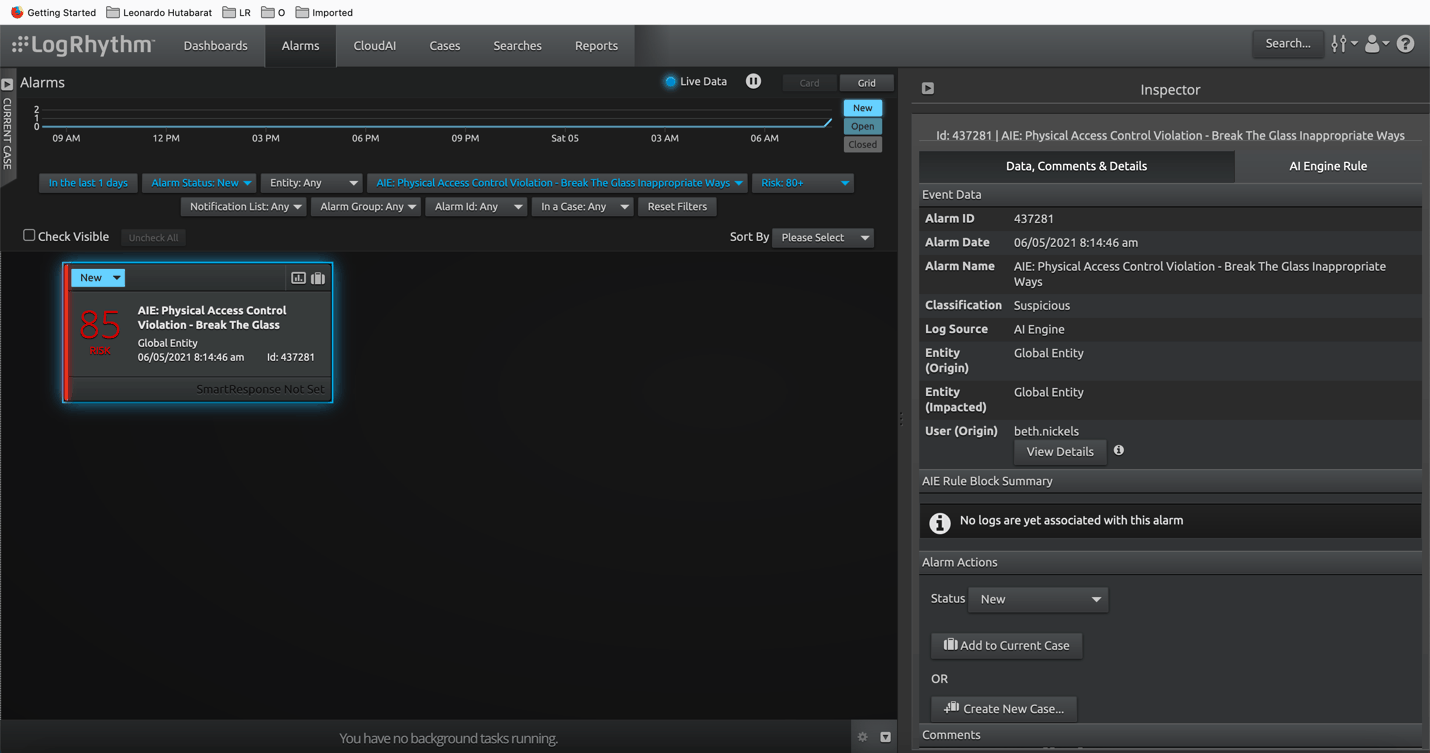
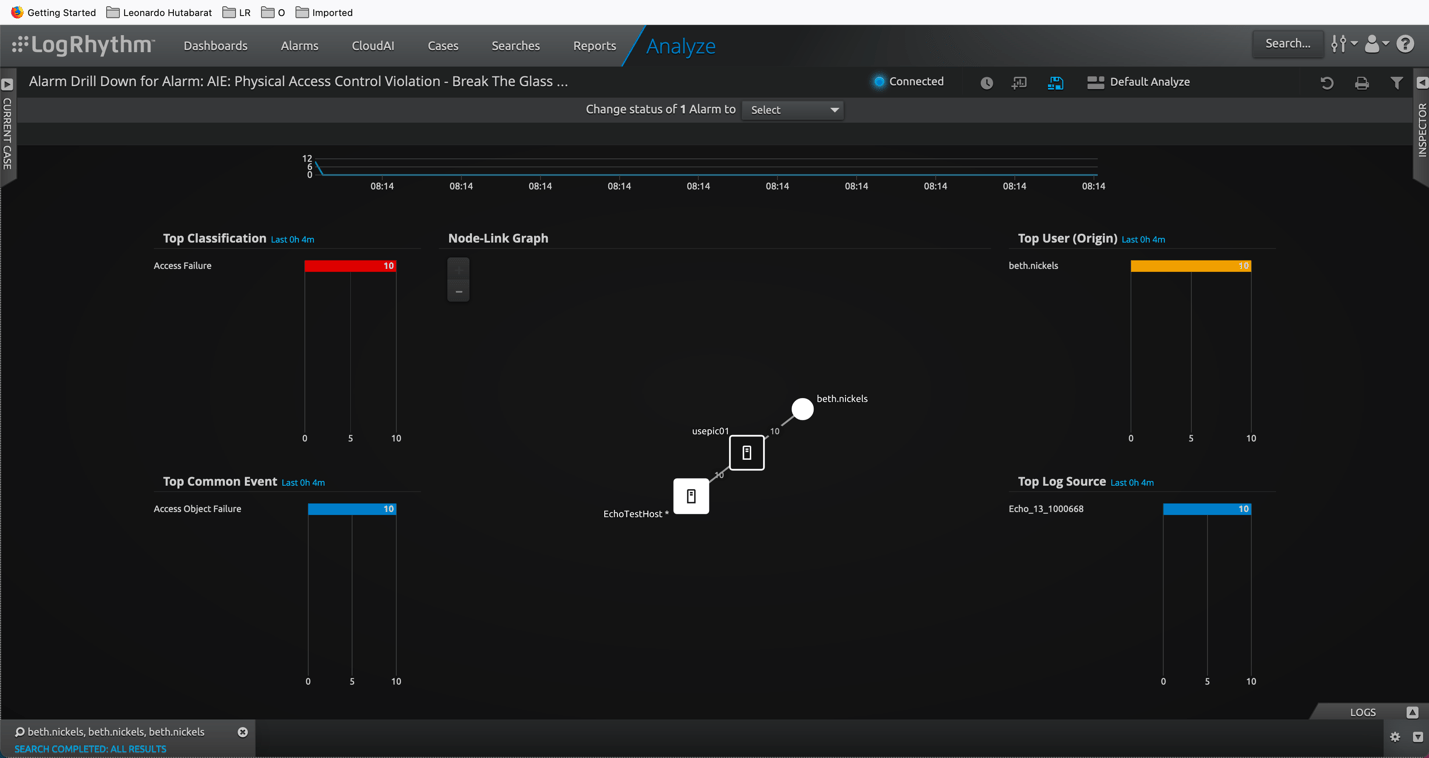
With Drill Down Alarm, LogRhythm will provide different security perspectives which will inform the security team about who broke the glass, with other additional information to enrich understanding on the incident.
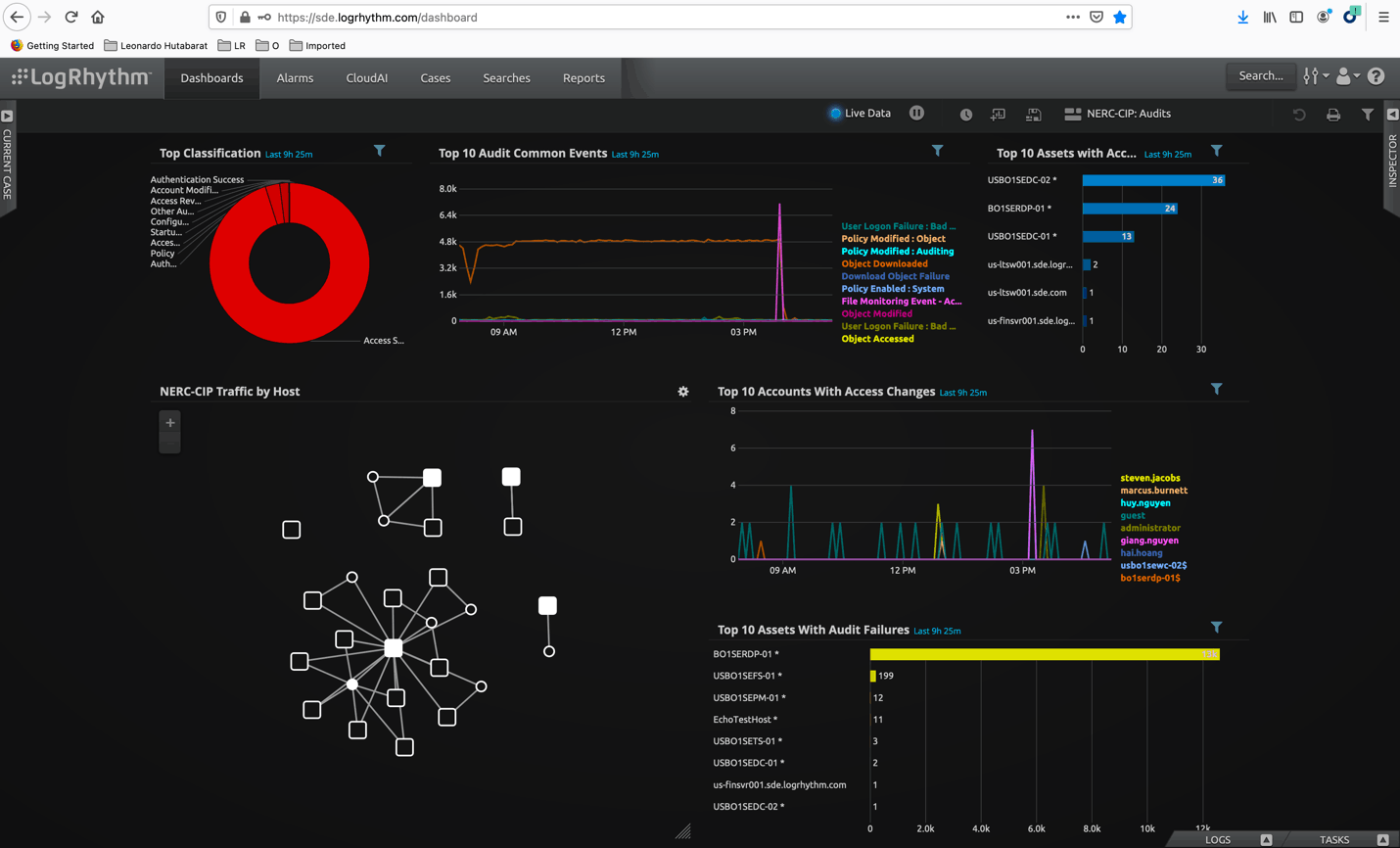
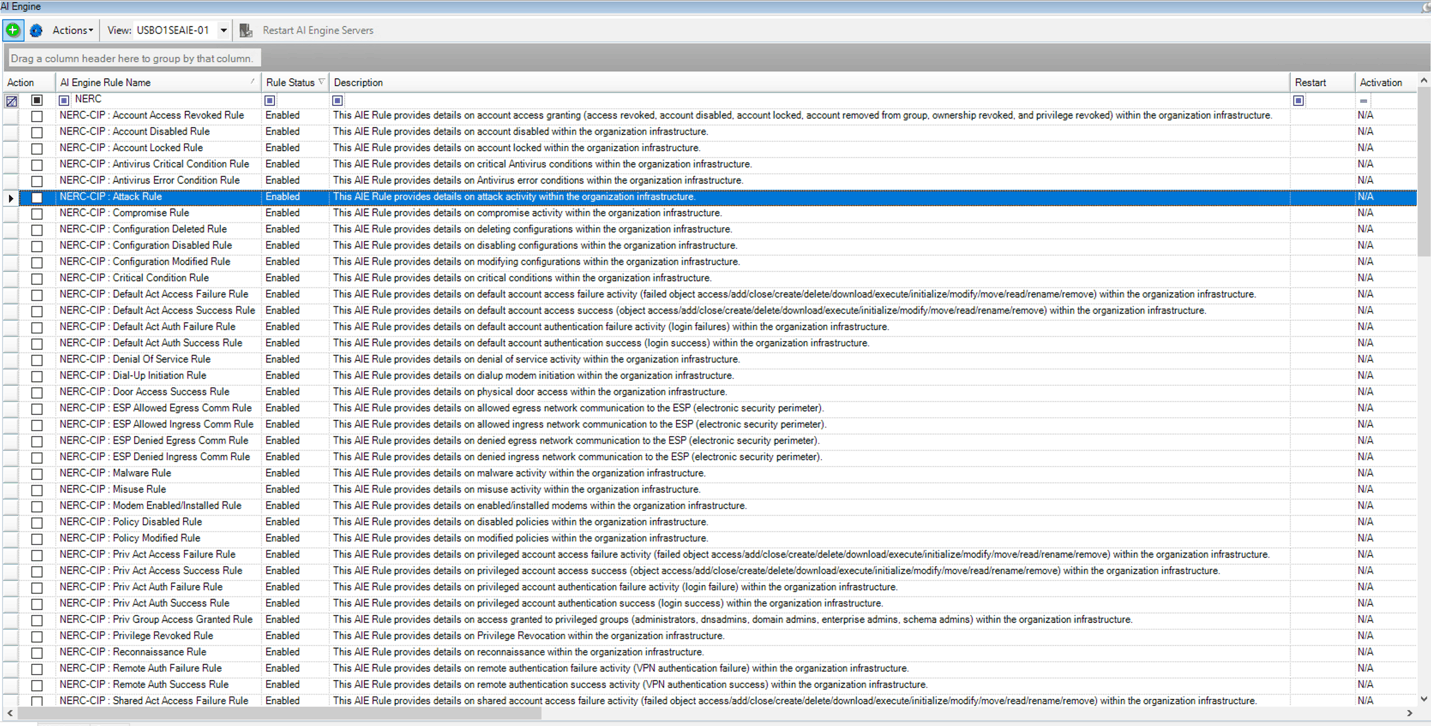
Use Case: NERC-CIP Compliance Monitoring and Assurance
The North American Electric Reliability Corporation (NERC) is a nonprofit corporation dedicated to ensuring that “the bulk electric system in North America is reliable, adequate and secure.” As a federally designated Electric Reliability Organization (ERO), NERC maintains comprehensive reliability standards that define requirements for planning and operating the collective bulk power system. Among these are the Critical Infrastructure Protection (CIP) Cyber Security Standards, which are engineered to ensure the protection of cyber assets critical to the reliability of North America’s bulk electric systems.
Due to its popularity and acceptance, NERC-CIP is not only followed by North America’s energy sector, but NERC has been adopted as best practice for global energy companies while CIP guides organizations to implement and perform procedures to effectively capture, monitor, retain, and review log data. This can be challenging because IT environments consist of heterogeneous devices, systems, and applications reporting log data, and because millions of log entries can be generated daily, if not hourly.
LogRhythm’s NERC-CIP compliance automation modules help companies meet these challenges. Further, to support companies transitioning from NERC-CIP V3 to NERC-CIP V5, we offer compliance automation modules for both regimes. The new V5 module leverages an entity-based structure to integrate “impact categorization” scoring into the logging, reporting, and real-time analytics and alarming capabilities of LogRhythm. LogRhythm uses this information to identify when activities of interest occur to high-, medium-, and low-impact Bulk Electric Systems (BES) cyber systems.
The Challenge
Compliance and best practice take time and resources to be deployed and maintained. Specifically on compliance, it can be a hurdle or it can be an enabler for businesses to run.
The Solution
LogRhythm provides NERC-CIP compliance module out of the box, so it can help energy companies implement, monitor, and continuously manage NERC-CIP compliance. LogRhythm’s NERC-CIP module ensures that bulk electric systems operate within the requirements of applicable policies, legislation, and regulations. It also enhances other security countermeasures, providing a complete “defense in depth” approach and facilitating automated responses for threats targeting bulk electric systems.
Follow Industry Security Best Practices
Compliance and best practices are key driving factors for security teams to roll out security information event management (SIEM) as the heart of their security operations center (SOC).
Regulatory compliance is a necessary, but often complicated and expensive, component of modern business. LogRhythm enables you to address cybersecurity regulations by providing preconfigured compliance automation modules that adhere to many common regulations and frameworks.
Use Case: Detect Ransomware
Ransomware has surged in magnitude and frequency and is proving to be costly. The Lansing Board of Water & Light (BWL), the provider of electricity and water to the residents of the cities of Lansing and East Lansing, Michigan, fell victim to a ransomware attack. This cost them $2 million for technical support and equipment to upgrade their security. During the incident, the city-owned utility was forced to shut down its accounting and email systems after an employee unknowingly opened an email with an infected attachment.
In the same year, a major electricity supplier in Johannesburg was hit by a ransomware attack. The company found all their databases, applications, and network encrypted. It also kept City Power’s website offline, affected their customers’ ability to buy prepaid electricity, and hampered the firm’s efforts to respond to localized blackouts.
The Challenge
Ransomware attacks have multiple entry points — from an administrator using a default password, to phishing attacks, to unpatched systems with any known vulnerabilities. It is challenging for electricity utility organizations to detect ransomware due to the nature of encryption of data compared to leaking the data out of their environment. Electricity utility organizations often only realize that ransomware has struck them when they encounter the ransom email and find their systems encrypted.
The Solution
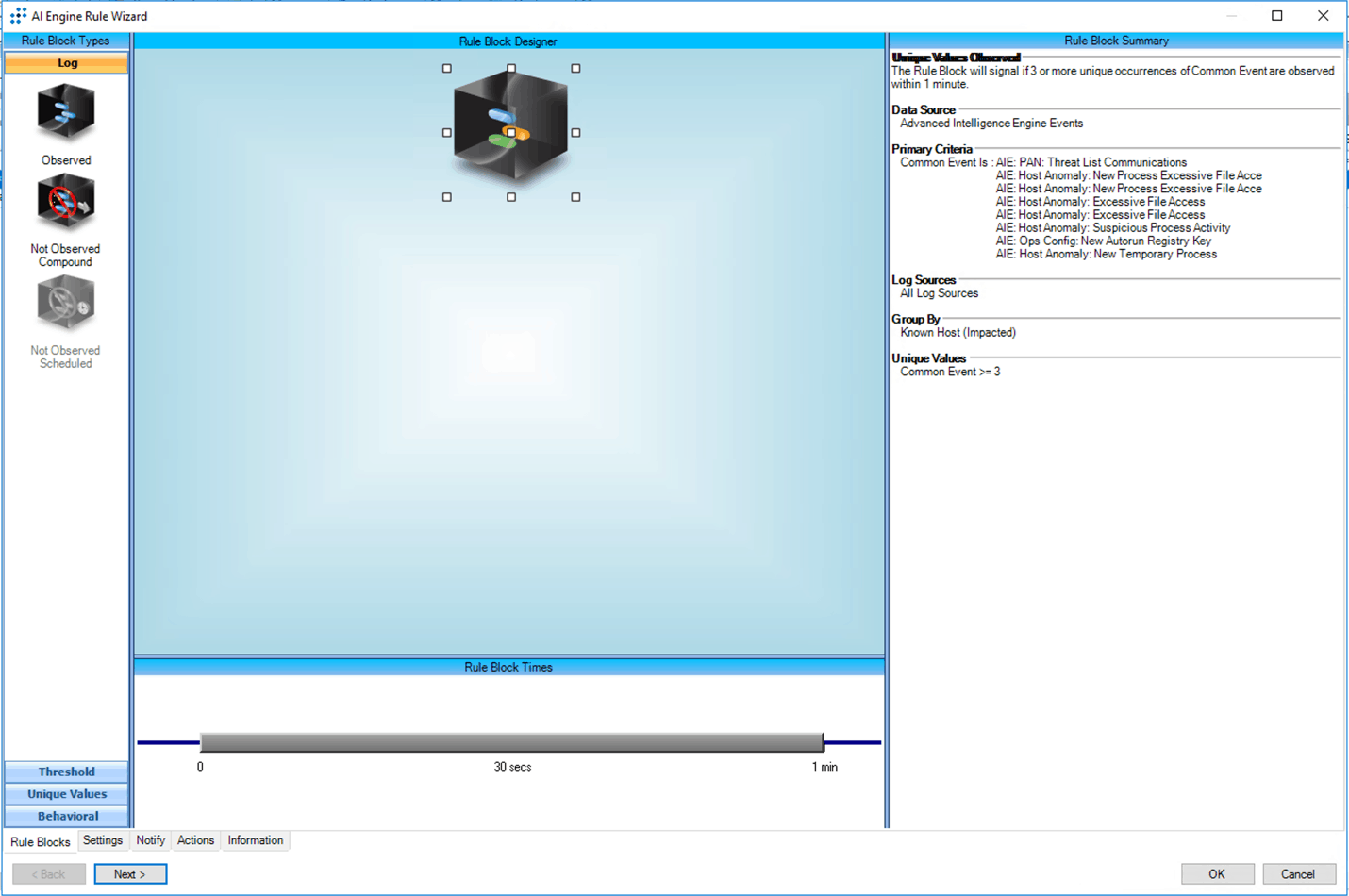
The LogRhythm XDR Stack enables the detection of ransomware attacks through a combination of LogRhythm’s AI Engine rules and LogRhythm’s File Integrity Monitoring (FIM) solution, known as LogRhythm’s SysMon Pro. Most ransomware attacks have the goal of encrypting files. Thus, extensive file access from a new process will be one of the indications of anomalous behavior.
Combining extensive file access with other behavior such as auto-run registry key will confirm if it is indeed a ransomware activity. AI Engine’s Risk-Based Prioritization builds trends and exposes statistical anomalies based on the risk level associated with specific network activity. By drawing visibility on and enabling teams to understand these behaviors, LogRhythm empowers security teams to detect ransomware and classify potential ransomware behavior.
Detect Ransomware and Rapidly Mitigate It
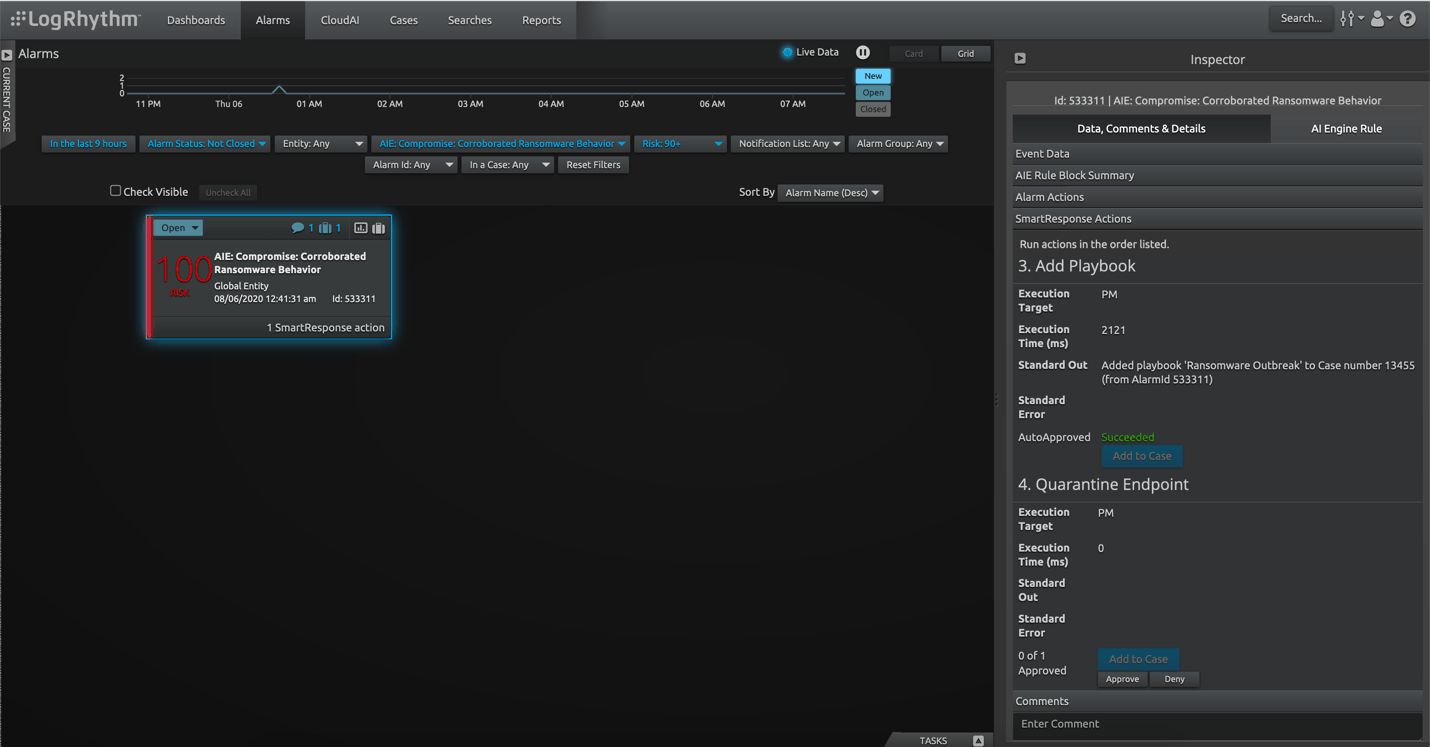
LogRhythm’s AI Engine enables security teams to detect high-risk ransomware behavior and identify anomalous behavior as early as possible, even if signature-based detection fails to detect ransomware. This provides multiple layers of detection.
To mitigate the ransomware threat, LogRhythm’s unique SmartResponseTM enables automated incident response. SmartResponse improves time to response (TTR) by providing automation that can integrate with other solutions. Analysts can execute fully automated remediation actions such as quarantining or isolating an infested host. Specific users (e.g., senior incident analysts) can review before they are executed in semi-automated, approval-based response actions. Teams can decide which actions to automate so they can focus on more complex incident response tasks that require more thought and creativity.
Use Case: Detect Advanced Persistent Threats (APTs)
Advanced Persistent Threats (APTs) have increased in scale and prevalence, and they are proving to be very effective against electricity utility organizations. The biggest challenge posed by APTs are their nature of persistence and their targeting your weakest link – your employees. A simple combination of phishing and social engineering can easily entice your organization’s personnel to click just one phishing link and infect the whole organization.
It’s critical to secure critical infrastructure. To discover how LogRhythm can help you and your team quickly detect and mitigate APTs and other electricity-specific use cases, download the LogRhythm NextGen SIEM for Electricity Utility Use Cases White Paper.