Designing an Adaptive Security Architecture with Unisys Stealth and LogRhythm
Detecting internal reconnaissance and lateral movement along the Cyber Attack Lifecycle—also known as the Cyber Kill Chain—can help organizations catch threat actors before they can realize target attainment. However, many security operations teams face barriers as they work to stop threats and recognize progression from one stage to the next.
Gaining early visibility into threats, such as insiders or external actors utilizing compromised credentials, can be impeded or complicated if threats are sufficiently stealthy. Meanwhile the sheer scale of “east-west” data center and cloud traffic, with heavily virtualized environments, increases the likelihood of laterally moving threats.
Unisys and LogRhythm Increase Visibility into the Cyber Attack Lifecycle
Unisys and LogRhythm have partnered to developed a powerful integration to detect and stop attacks early in the Cyber Attack Lifecycle. Unisys’ robust micro-segmentation technology, Stealth, utilizes identity-assigned VPN communities or communities of interest (COI) to isolate network activity to only users who need access. Users can’t see into or out of Stealth enclaves unless their COI privileges permit them to do so.
This level of visibility and control prevents internal reconnaissance, while any attempt at pivoting is easily seen—and it is likely indicative of a threat trying to move laterally. If someone is pushing the boundaries of a community, immediate visibility into that activity from Stealth can be leveraged by LogRhythm to help an organization quickly detect movement and respond immediately.
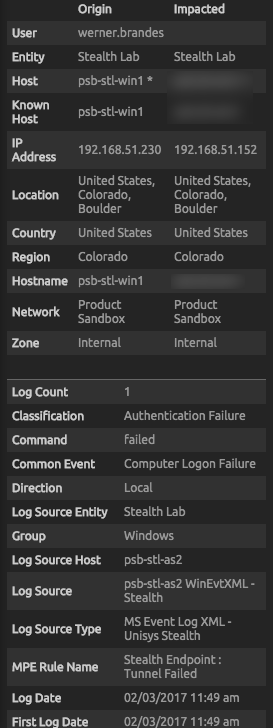
Network traffic with a destination outside of the assigned COI never egresses the computer. This leaves many standard recon detection techniques ineffective, even with LogRhythm’s out of-the-box analytics. Stealth, however, does log this activity as a VPN tunnel failure. LogRhythm’s normalized meta data adds context to these failures, indicating intended network traffic direction, users involved, and even geolocation.
Figure 1: Normalized Meta Data
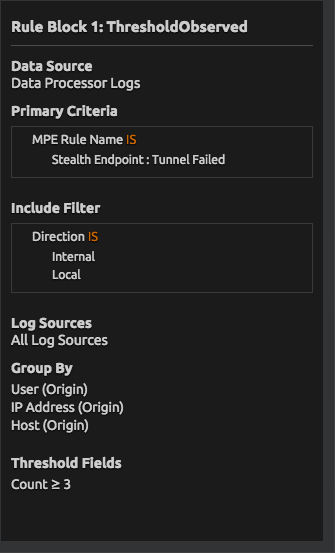
In a Stealth deployment with appropriately tuned Communities, these tunnel failures should be minimal. LogRhythm AI Engine rules can look for a certain threshold of these events and alarm if too many are seen within a given period. This can be adjusted to minimize false positives and group behavior in a way that makes sense for your environment. Slow, distributed reconnaissance from multiple hosts can even be detected, as network access is defined by the user account, not the switch and router topology.
Figure 2: LogRhythm AI Engine Rule Looking for Excessive Tunnel Failures Over a Given Period
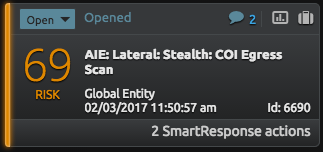
Figure 3: LogRhythm AI Engine Alarm Indicating Excessive Tunnel Failures Over a Given Period
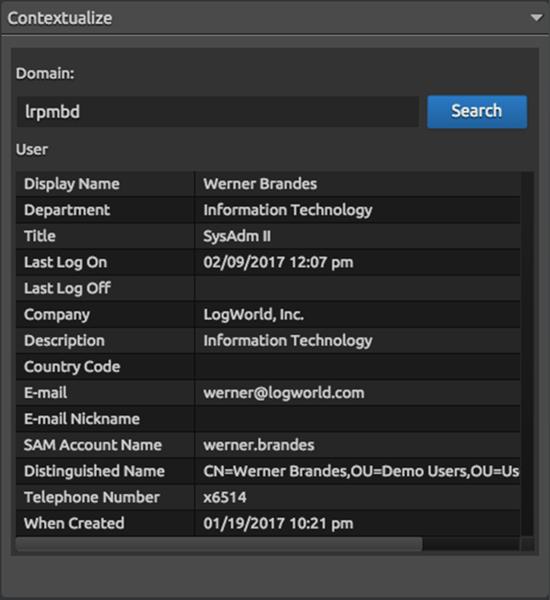
Using a drill-down search to gather the logs generating these alarms, analysts can quickly add context to the situation.
Figure 4: AI Engine Alarm Drill Down
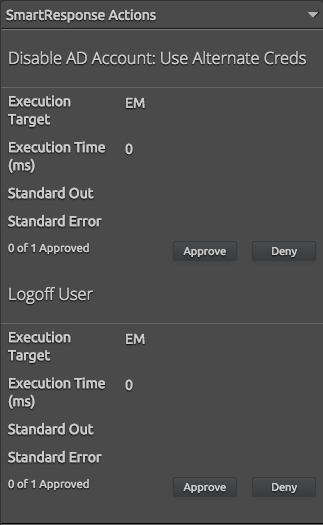
If warranted, an analyst can take immediate and decisive action directly from the alarm card using LogRhythm SmartResponse™ automated playbook actions. In this case, disabling the user’s Active Directory account and logging them off their active sessions effectively stops the probing and prevents additional compromise using this user’s credentials. Highly corroborated, high-risk alarms can execute these actions in a fully automated fashion, further optimizing not just time to detect and respond to incidents, but freeing security personnel to work where they are most needed.
Figure 5: LogRhythm SmartResponse Disabling a User’s Active Directory Account (Click on images to view larger.)
With Stealth’s user-centric approach to isolated, secure, software defined networking (SDN) and LogRhythm’s user, endpoint, and network analytics, a dynamic network architecture capable of responding to internal and external stimulus at the speed of the network can be realized.
To learn more about the Unisys and LogRhythm integration, download the joint white paper.