Managing multiple accounts across various cloud and on-premise infrastructures centrally is a challenge for most security operations centers. To address this ever-increasing need, the LogRhythm Office of the CISO recently implemented Okta.
Okta enables a nearly seamless management process for IT, the Office of the CISO, and global employees. It is a key component to LogRhythm’s vision of embracing a Zero-Trust security model, helping to expand services between on-premise and in the cloud. While integrating applications and visualizing this data within the SIEM is a great first step, it’s beneficial to take this process a bit further by fully automating Identity Access Management (IAM) with the SIEM at the center.
Please note: All of the items covered in this blog can be downloaded here: https://github.com/LogRhythm-Labs/Invoke-Okta
Visualizing Okta Data
To begin implementing a Zero-Trust model using Okta, you need to first visualize the Okta data you’re ingesting into the SIEM. This is pretty straightforward. You can use LogRhythm’s Okta Integration Guide to develop a dashboard to quickly and easily visualize the diverse authentication activity occurring within your organization.
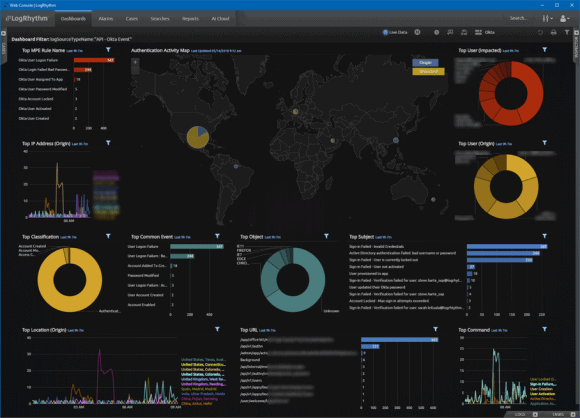 Figure 1: LogRhythm Web Console Used to Quickly and Easily Visualize Okta Data
Figure 1: LogRhythm Web Console Used to Quickly and Easily Visualize Okta Data
When analyzing the dashboard, you can pick up on key data points that make this data a vital resource for understanding employee authentication activity. However, there is more you can do with this information. For example, leverage LogRhythm AI Engine to trigger alarms on suspicious activities.
Okta and AI Engine Rules Alert to Account Compromise
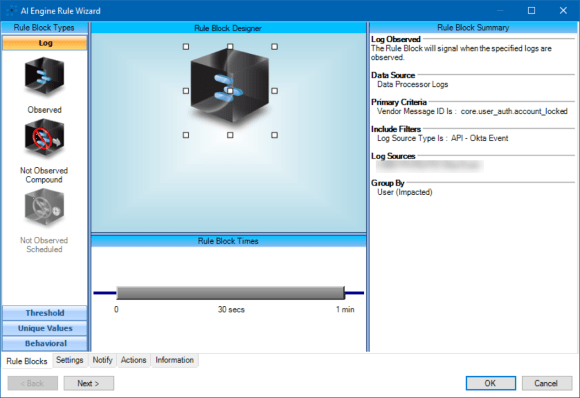 Figure 2: Alarm Fires to Alert to a New Okta API Key Creation
Figure 2: Alarm Fires to Alert to a New Okta API Key Creation
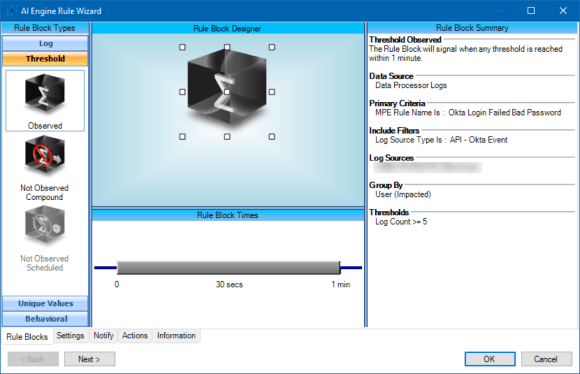 Figure 3: Detecting Brute Force Activity
Figure 3: Detecting Brute Force Activity
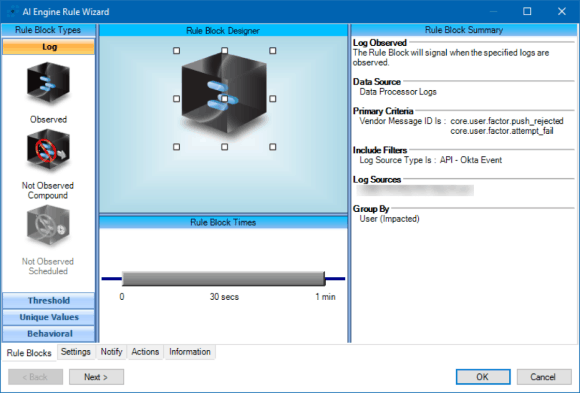 Figure 4: Alarming When an Account Has Been Locked Out
Figure 4: Alarming When an Account Has Been Locked Out
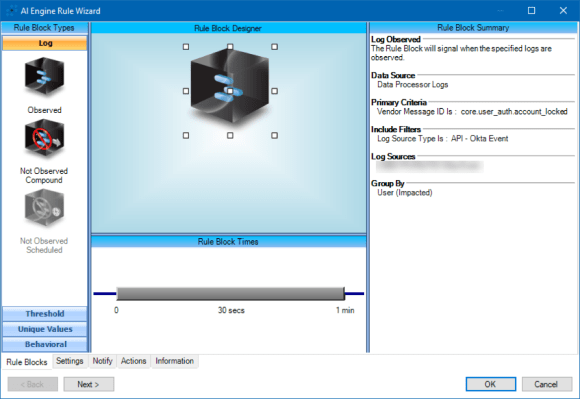 Figure 5: Triggering on a Successful Authentication, but Failed Multifactor Login (Likely Compromised Credentials)
Figure 5: Triggering on a Successful Authentication, but Failed Multifactor Login (Likely Compromised Credentials)
SmartResponse Integrates with Okta
There are countless security and operations-related possibilities with Okta; however, this example focuses on the account lockout use case. When accounts are locked out, you should do more than simply notify the security operations center (SOC). One option is creating a SmartResponse™ action that sends emails off to the IT and Security Operations teams to let them know when this occurs. In addition, this SmartResponse will send an email to the end user, letting the individual know about their account lockout right away, so that he or she can contact IT to get their resolve system access.
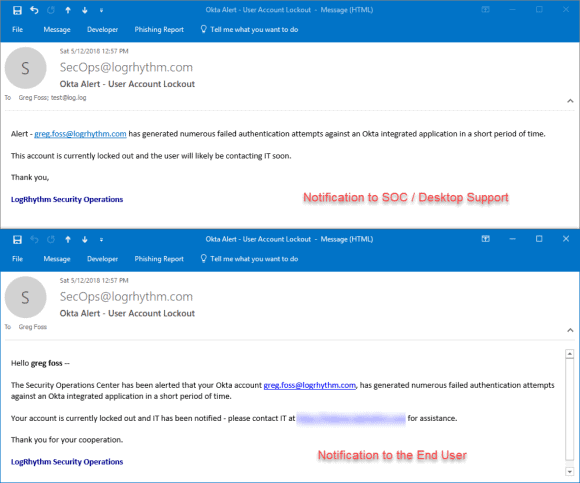 Figure 6: End User Receives Alert of Account Lockout
Figure 6: End User Receives Alert of Account Lockout
This alert is only scratching the surface. In addition to setting up simple notifications, you should fully automate account management. For this reason, I created Invoke-Okta. Invoke-Okta is a PowerShell script that utilizes the Okta API to fully handle a majority of security-focused use cases, such as clearing user sessions across all Okta-integrated applications or resetting a user’s password.
 Figure 7: Invoke-Okta Clears User Sessions
Figure 7: Invoke-Okta Clears User Sessions
Integrating this script into a SmartResponse allows you to perform even more impactful actions within the Okta API from directly within the SIEM.
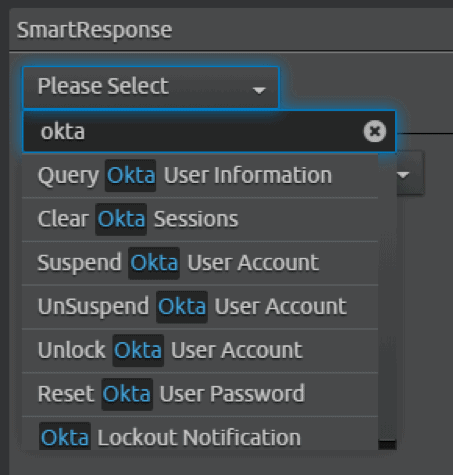 Figure 8: Combine Okta SmartResponse Actions for Successful Outcomes
Figure 8: Combine Okta SmartResponse Actions for Successful Outcomes
You can combine this SmartResponse with the previously mentioned employee notification email, to provide the ability to unlock an account directly from the Alarm page with the click of a button.
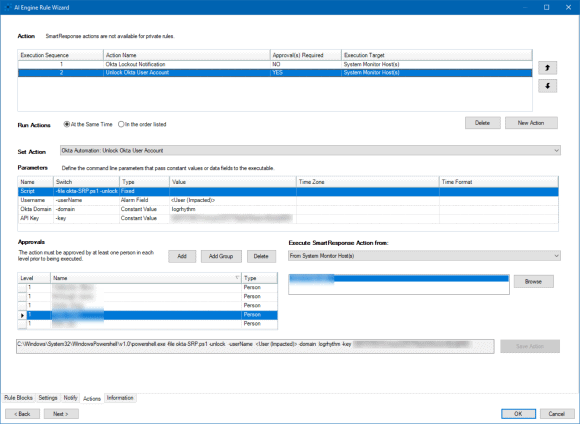 Figure 9: AI Engine Fires to Unlock an Account Following SOC Lead Approval
Figure 9: AI Engine Fires to Unlock an Account Following SOC Lead Approval
These SmartResponse actions can be combined to suit the organization’s needs around both security and operations — simplifying and streamlining the process of IAM automation with the SIEM.
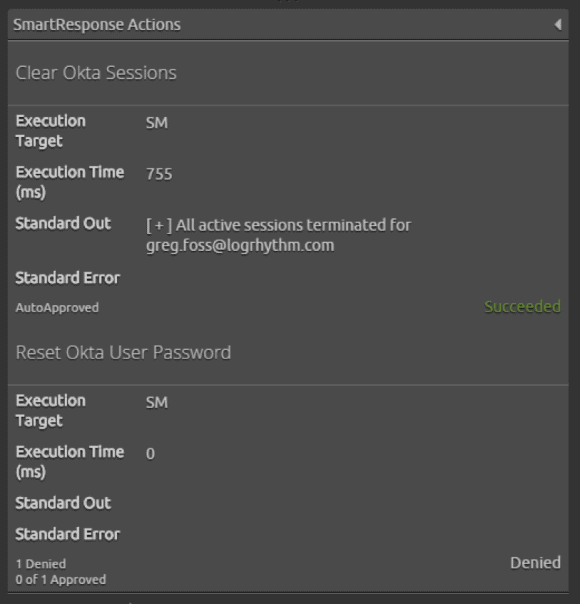 Figure 10: SmartResponse Actions Combined to Suit the Organization’s Needs Around Both Security and Operations
Figure 10: SmartResponse Actions Combined to Suit the Organization’s Needs Around Both Security and Operations
IAM Management in a single User Interface
Many organizations are embracing cloud-centric models and moving toward a Zero-Trust model. However, not many can seamlessly manage and respond to IAM-related attacks from a single user interface. By utilizing the power of Okta and LogRhythm together, you can provide the full capabilities of IAM management to both the SOC and IT Operations, giving these teams the tools they need to understand their threat landscape and respond to threats in seconds, all without leaving the SIEM.