The Scenario
I’ve been asked to prepare a security audit—and I only have the weekend! So I start to do my research, of course reading the many posts on LogRhythm’s website…but the weekend gets away from me. Instead of preparing, I spend my Saturday afternoon enjoying the beautiful fall colors. Now I’m down to football Sunday! What to do?
The Solution
Not to worry! I’ve just upgraded to LogRhythm 7. Armed with the DatabaseInstaller, LogRhythmInstallWizard, WebConsole Installer and the Install Guide, I have the confidence that I can accomplish my assignment. Just over an hour later, I have configured the server and I’m collecting my first stream of logs. I accept the pending ASA, NetMon and WiFi AP syslog streams—then step away for some BBQ.
I fire up a Chrome instance of WebUI—and of course, I play with the new dashboard features. Immediately, I see interesting data—a smattering of impacted regions across the world. The world? Really?!
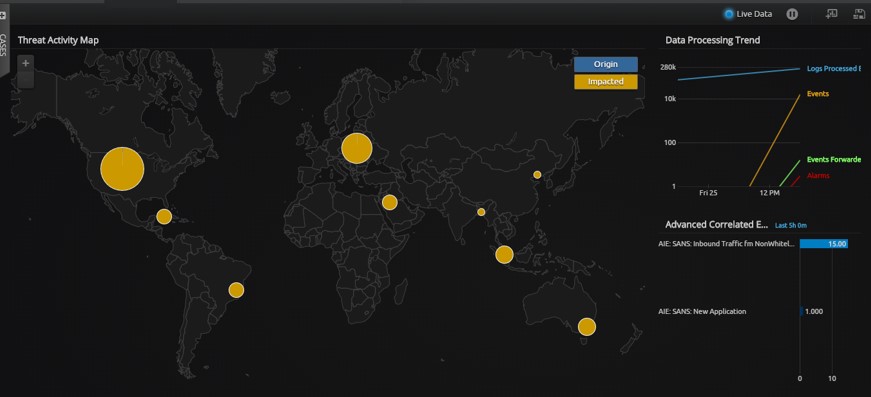
Red flags fire. I can also see the AI Engine: SANS Inbound Traffic from Non-Whitelisted Countries reporting this. A quick drilldown on this destination port confirms what NetMon is already picking up from the wire. But I don’t yet have the complete picture. NetMon was lacking the details on the process.
Fortunately, I have an agent on this host and I enable Process Monitor. I wait five minutes to get some data. Then I investigate.
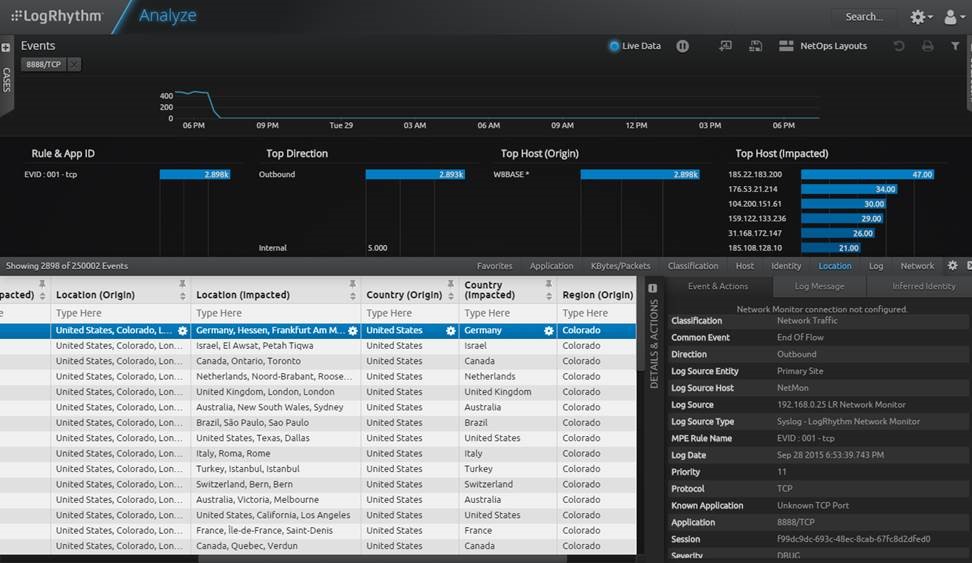
Next, I dive deeper into local host forensics / network connection monitoring:
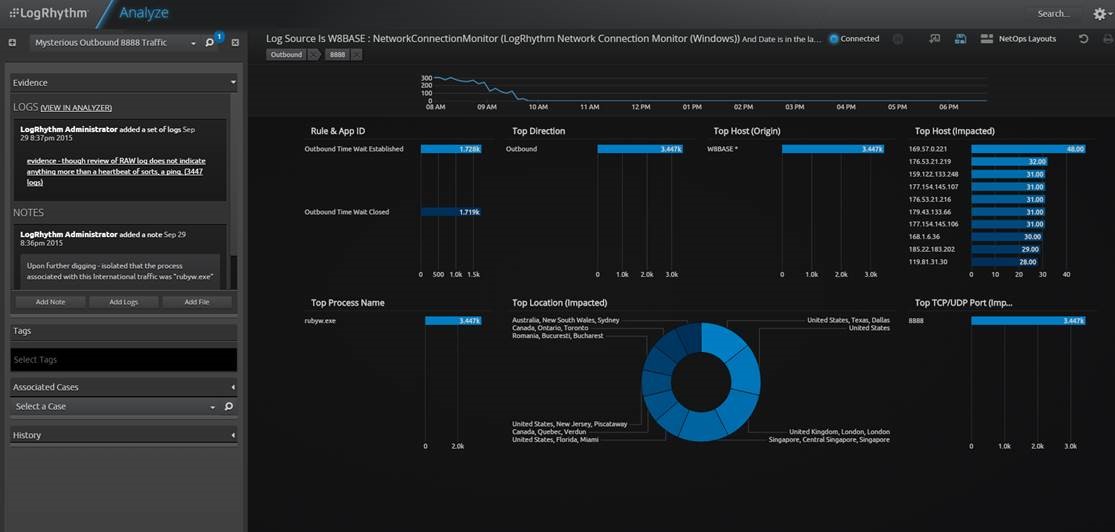
Bingo! I found the sneaky bugger! Using Case Management, I pull the log evidence aside. I come back from walking my dog and with one tweak of a widget on my layout, I see the culprit—Rybyw.exe!
It turns out that this is a known subservice of a PIA VPN that I subscribe to: https://www.privateinternetaccess.com/forum/discussion/790/questions-regarding-the-backround-network-scans-of-rubyw-exe
The moral of the story is that this was a false positive. But to be honest, it did freak me out at first. I thought I had been pwned.
But wait folks—there’s more! If you buy in the next 20 minutes, you’ll get a free set of Ginsu knives! (No, not really, but you know you want them.)
What I can actually offer you is the ability to update your Whitelist Processes List quickly! Bam!
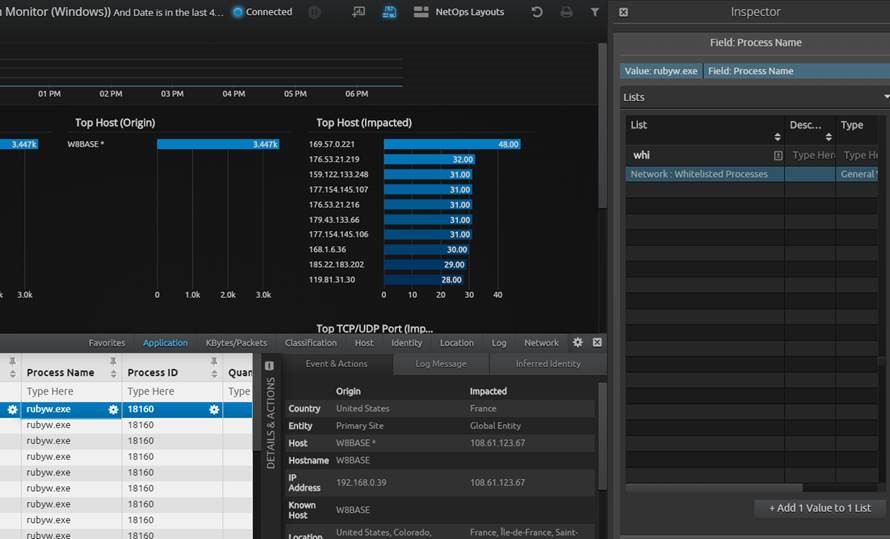
The Benefit
So what’s the benefit from all of this? Faster time to detect and respond! I accomplished all of this while I suffered through a terrible Chicago Bears performance. But in all seriousness, the amount of work I had to do from an administrative standpoint was pretty effortless. Cheers to LogRhythm 7!