The Challenge
Microsoft Management Console (MMC) hosts administrative tools that you can use to administer networks, computers, services and other system components. These tools are provided as plug-ins. Some of the common ones are Active Directory Users and Computers, DNS and Eventvwr.
Windows ships around 36 of these plug-ins. Because they’re extensible, other plug-ins exist within other Microsoft products, and you can create your own plug-ins should you wish.
The challenge with the MMC-hosted tools is that the binary is always called MMC, which makes it difficult to deduce what the user was actually doing. Were they legitimately administering users? Or were they tinkering with adsiedit?
Just recording the process will not help here, because the process will always be reported as “mmc.exe” irrespective of which plug-in was launched.
The Solution
LogRhythm’s File Integrity Monitoring captures a variety of information about files being accessed. This includes the file name and path, the process responsible for the file access and the user account that initiated the action.
By virtue of our structured data approach, you can take all this information and create an AI Engine rule that will alert you when unauthorized users launch specific MMC plug-ins.
First, you would create a policy to monitor the folder that contains the plug-ins. In this case, you are only interested in read access to .mcs files (the default extension for MMC plug-ins).
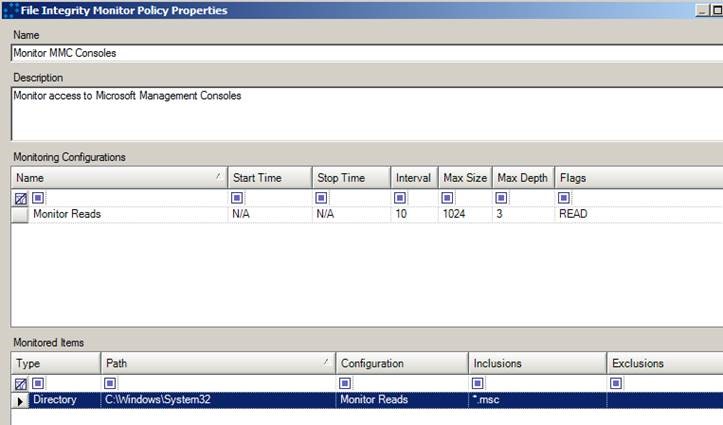
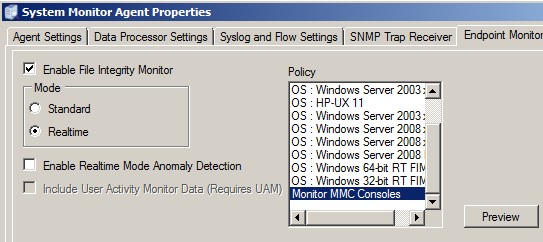
The Active Directory Admin Tools are typically found on DCs, plus any hosts where the admin pack has been installed. Local Windows admin tools also use the MMC framework, so depending on what it is you want to monitor, you may or may not wish to apply this policy to all of the hosts in your network.
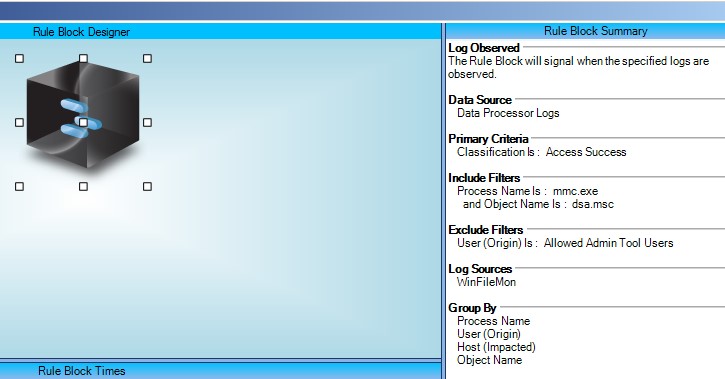
Now, you can create the AI Engine rule. In this example, I am simply looking for unauthorized use of dsa.msc—the plug-in for Active Directory Users and Computers. The process name is “mmc.exe,” and the classification is Access Success.
In this example, I have created a list of users in my environment that are allowed to run the Admin Tools that I have added as an exclude filter in this case. This is handy, because you wouldn’t want to be alerted when previously validated users are accessing the tool.
This particular list should not be dynamic, because in this scenario, you don’t want all of your admins to be administering the AD—you just want to have a small subset of admins whose role is to administer the Active Directory contents.
When the alarm is triggered, you get a nice summary with all of the relevant information on the inspector tab.
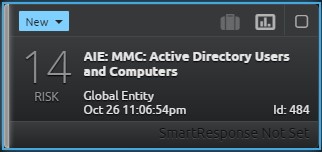
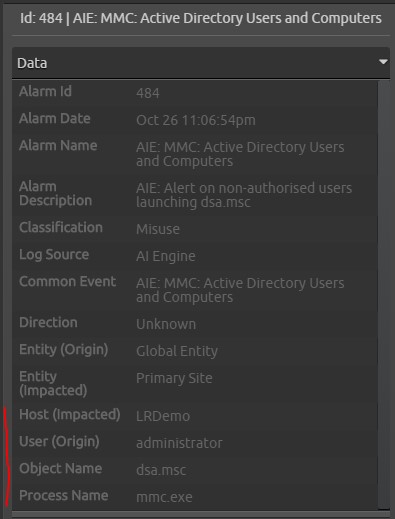
In this case, I was only interested in Active Directory Users and Computers (dsa.msc). However, this rule could easily be cloned to monitor each type of MMC plug-in individually just by changing the “Object Name” field.
You could also edit it to include a list of all the plug-ins where the admins are allowed to perform all functions. Alternatively, the plug-ins could be placed into logical groupings for each Administrator role in a larger organization. Other Microsoft tools also have MMC plug-ins available (e.g., Microsoft Exchange), so this might typically be another Administrator role.
This AI Engine rule could also be used purely for reporting purposes, rather than alerting in real time. This might be an option if you are more interested in auditing after an event.
The Result
LogRhythm’s File Integrity Monitor and AI Engine work well together to give you an extra level of insight into what is really happening in your environment.
Here is a full list of standard Windows plug-ins shipped with 2008R2 AD with the plug-in file names for your reference:
| Plug-In Name | Full Name |
|---|---|
| dsa | Active Directory Users and Computers |
| services | Service Manager |
| Eventvwr | Event Viewer |
| Servermanager | Server Manager or Right Click Manage Computer |
| Domain | Active Directory Domains and Trust |
| Dssite | Active Directory Sites and Services |
| Adsiedit | ADSI Edit |
| Comexp | Component Services |
| Compmgmt | Computer Management |
| Dnsmgmt | DNS |
| Gpmc | Group Policy Management |
| Secpol | Local Security Policy |
| Perfmon | Performance Monitor |
| Storagemgmt | Share and Storage Management |
| StorExpl | Storage Explorer |
| Taskschd | Task Scheduler |
| WF | Windows Firewall with Advanced Security |
| Wbadmin | Windows Server Backup |