Recently, Chris Petersen (LogRhythm’s CTO and Co-Founder) recently published the Security Operations Maturity Model (SOMM). The SOMM provides a systematic guide for an organization to assess and actively achieve a heightened security posture. In the SOMM, Chris stresses that the cyber-threat landscape is changing dramatically, and you must change your focus to stay sharp on this journey to be resilient to attacks and breaches.
The Current Cyber-Threat Landscape
Traditionally the industry has focused on detecting threats based off signatures and file types. But breaches in the past year seem to be more focused on the vulnerabilities of our end points and users. With the Internet of Things (IoT) growing wildly, you need to focus on the security activities of the malicious folks and the not just the known tools.
Big data analytics are crucial in helping you to hear the signal through the noise. Taking in your traditional log sources (e.g., domain controllers, AV, IDS/IPS, firewalls, etc.) will certainly give you a good understanding of the user, host and in/egress activity. But all of this information is not enough if you want to
achieve resiliency.
A recent report by Trustwave indicated that the ROI on an exploit kit was an estimated 1,425%. If you do the numbers, that’s $84,100 net revenue for every $5,900 spent.
In addition, Net-Security conveys another concerning statistic: The average (mean) days intrusion to detection period appears to be approaching 200 days.
What You Don’t Know Won’t Hurt You. Right?
In your fight against malware, exploit kits, spear phishing and so forth, you need to really look at the local forensics to fill in the shadows of your holistic view. There are many solutions out in the market that will help you wrangle in your endpoints and user behavior. But at what cost? How many consoles and what different skill sets are required?
In looking back at some of the major recent breaches, many of these instances were discovered by outsiders, took weeks to come to light and had several indicators that something was amiss.
“If collecting data from existing security systems, correlating that data in a single repository and raising frequent alerts to trained security professionals is insufficient to detect and prevent (or at least stop) breaches, then exactly what is necessary to do the job? This is the question being raised by every organization with a mandate to protect its customer data, intellectual property, trade secrets and business strategies and, ultimately, its market value.”
–The Cyber Threat Risk—Oversight and Guidance for CEOs and Boards
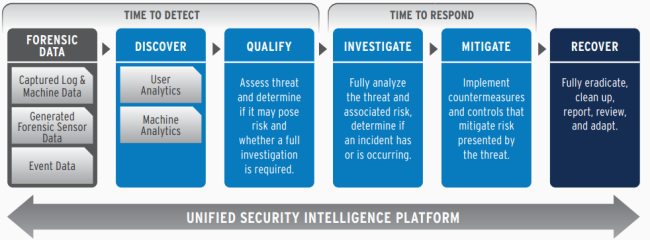
To be effective, you must rely on skilled people, well-defined policies and processes and a range of integrated technologies. If you want to maintain a strong security posture, you must invest on heavily automated, end-to-end threat detection and response capabilities. This can be described as a progression of stages:
Steven Russo stated, “The clear definition of the insanity in cyber today is that we continue to protect sensitive data the same way over and over again and expect a different result. I do not think there should be any doubt in that current methods are simply not good enough and something needs to change. The ever present threat of cyber-attack underscored by the recent array of mass-data breaches in most sectors of the economy are forcing business of all sizes to take action. The current need is for new ways to secure data at rest and data in motion from cyber-attack, mass data loss, and internal as well as external criminal exploitations.”
