The journey to Zero Trust
Digital transformation, cloud technologies, and the remote workforce have created new cybersecurity challenges for organizations across the globe. The need to defend and respond to security threats has never been more apparent before.
Today’s modern-day organizations require an adaptive and resilient Zero Trust security model to effectively protect people, devices, and data across the enterprise.
Wondering where to start with implementing Zero Trust? Get started with our free zero trust resources!
What is Zero Trust?
Coined by Forrester over 10 years ago, the phrase “Zero Trust” is based on the belief that trust is a vulnerability, and therefore, security must be defined by the strategy, “Never trust, always verify.”
With the rise of mobile technology and cloud migration, an organization’s network perimeter is much harder to define. Data is now continuously transferred between software as a service (SaaS) applications, infrastructure as a service (IaaS), remote users, IoT devices and more, providing multiple entry points for hackers to access sensitive information.
Instead of assuming everything behind the corporate firewall is safe, Zero Trust principles strengthen an organization’s security maturity by eliminating a perimeter-based defense and focusing on strict authentication at each access point. A Zero Trust security model ensures that no device, user, system, or workload is trusted by default, regardless of the location it is operating from.
Presume all networks are untrusted
Verify each request as though it originates from an open network.
Apply least privilege access
Restrict access based on the minimum permissions required to carry out a task.
Assume breach
Reduce risk by inspecting and monitoring everything.
Is Zero Trust right for you? The barriers and benefits
Interest in Zero Trust has increased during the COVID-19 pandemic as many organizations have acknowledged their perimeter-based security strategy produces vulnerabilities, especially with a remote workforce. Over the years, applications have been pushed into the cloud, but users unexpectedly being pushed outside the perimeter is a new challenge for many IT and security teams.
On top of these recent obstacles, threat actors are becoming more sophisticated than ever before with their tactics. Along with many others, your organization may be leaning towards a Zero Trust security model to help improve security posture and reduce risk to your business. Depending on your business goals, resources, and legacy systems, you may run into different barriers and benefits while implementing a Zero Trust security model.
Barriers:
Implementing a Zero Trust architecture requires you to unwind legacy infrastructure, workflows, and processes that create new challenges. Depending on the size and complexity of your organization, you may run into barriers such as:
Benefits:
While organizations may face many barriers when implementing a Zero Trust security model, the outcome can lead to many benefits, including:
- Budget and funding
- Team buy-in
- Board-level support
- Change with vendors
- Complete and cohesive execution
- Time investment
- Resource constraints
- Improve network traffic visibility
- Increase control in the cloud environment
- Prevent threats and mitigate breaches
- Enhanced compliance reporting
- Enable adaptability with digital transformation
- Reduce overall capital expenditure (CAPEX)
- Streamline operating expenses (OPEX)
Building a Zero Trust security model
Implementing a Zero Trust architecture is a complex journey that is a continual process. Every organization’s path to Zero Trust can look different and it’s important to be patient and prioritize your projects and initiatives one step at a time. From small to large companies, expect the process to be a marathon, not a sprint.
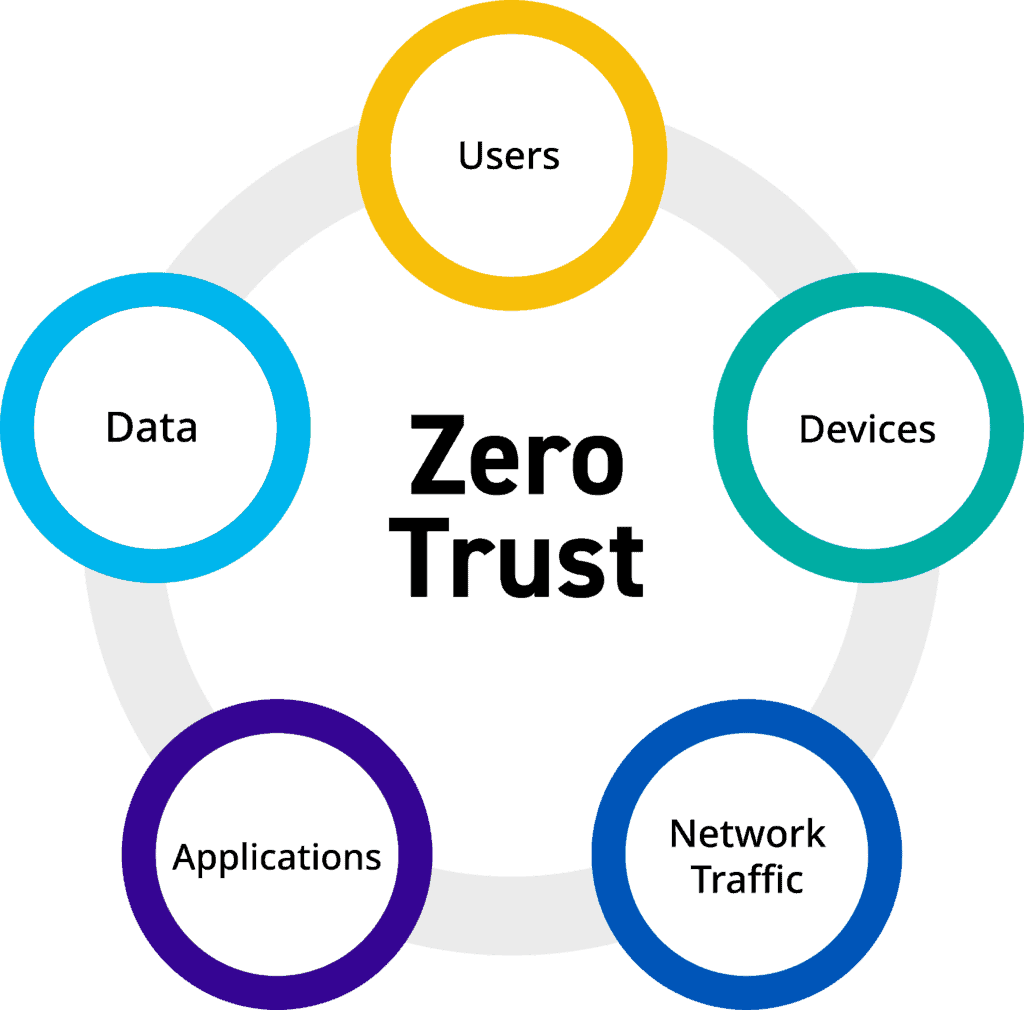
Forrester recommends building a security model that requires an end-to-end strategy based on seven elements in the Zero Trust eXtended ecosystem (ZTX):
Data
Classify sensitive information in your data to guide policies and controls on what needs to be protected.

People
Consistently monitor user access and apply least privileged concepts at every level.
Devices
Apply network segmentation principles to create microperimeters that isolate IoT devices.
Visibility and analytics
Invest in the ability to correlate events across disparate domains.
Workloads
Establish a cloud governance process and management solution, conduct inventory, and monitor workload configurations.
Networks
Reduce attack surface and lateral movement by segmenting boundaries around network assets.
Automation and orchestration
Implement response protocols and technologies that can prioritize threats, improve workflow, and reduce mean time to respond (MTTR).
Get free resources to begin your Zero Trust implementation
Implementing a Zero Trust model takes substantial planning and persuading stakeholders before execution can begin.
To help you get started on your Zero Trust journey, LogRhythm put together a collection of free templates, including:
- Business Case Template
- Project Charter Template
- Budget Template
- Project Plan Template
- Status Report Template
- Technology Architecture Template
Save time by downloading this starter package to manage your Zero Trust initiatives and deliverables!
Explore more Zero Trust resources
Webinar: Learn Why Zero Trust Security Matters Now
Join LogRhythm CISO Andrew Hollister as he dives into the importance of Zero Trust and reveals best practices to adopt this security architecture to ensure success.
Watch this webinar to learn:
- The advantages and disadvantages of implementing Zero Trust
- Organizational changes needed to implement a Zero Trust strategy
- Key obstacles to avoid when exploring Zero Trust
LogRhythm Can Help You Achieve Zero Trust
If you are hoping to implement Zero Trust to improve your security posture, there are many processes and technologies to help secure your data, people, devices, and networks.
As you invest in your Zero Trust journey, LogRhythm can play a special part in leading you on a path to Zero Trust by assisting with visibility and analytics, as well as automation, orchestration, and security content.
LogRhythm SIEM has built-in Zero Trust capabilities to help you gain deep visibility across your network. Combined with the power of security, automation, orchestration, and response (SOAR) and entity, user, and behavior analytics (UEBA), LogRhythm has the tools to enable your security operations center (SOC) to detect and respond to threats measurably faster.
LogRhythm also has resources that keep your organization well informed of the latest incidents and breaches that could pose a threat. LogRhythm Labs can help with a dedicated team that delivers use case content encompassing the latest information on emerging threats, changing compliance mandates, and Zero Trust best practices.
Secure your way to Zero Trust
Every Zero Trust journey is unique. Start by evaluating your current environment, available resources, and priorities. If you have identified gaps in your security posture, schedule a custom demo to discover how LogRhythm’s SIEM, UEBA, and SOAR capabilities can reduce risk to your business and mature your security operations.