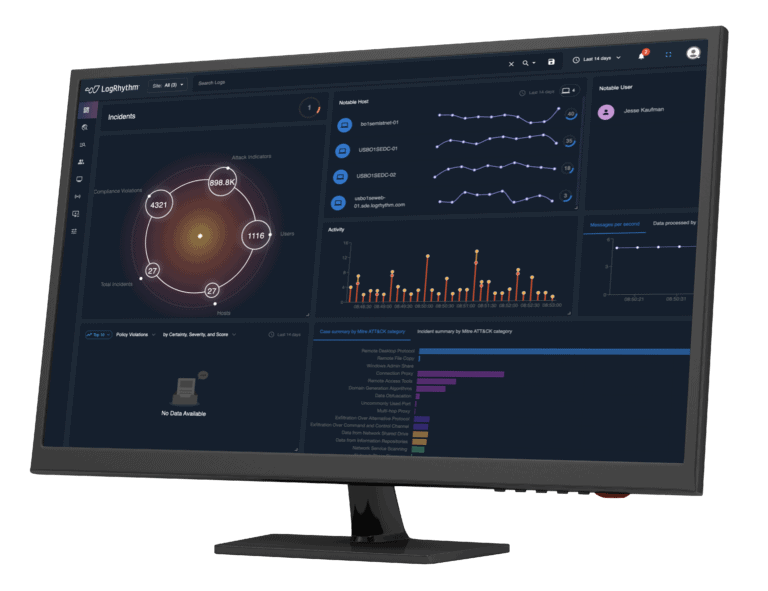
What's New @ LogRhythm
Learn about new product innovations we deliver every 90 days. Register for our April release webinars!
LogRhythm is proud to announce our eighth consecutive quartlery release!
From compliance content, new and enhanced log sources, integrations, and more, explore what’s new this quarter.
LogRhythm is proud to announce our seventh consecutive quarterly release. This quarter, there are many notable improvements to the tech stack. From enhancing log collection, search functionality, and analyst workflows, discover the latest updates below and register for our quarterly release webinars.
This quarter, our product innovations help bridge skill gaps, cut log source onboarding time, enhance contextualization into threats, and much more!
Explore our latest product updates in the dropdown and resources below, plus watch our quarterly release webinar for more information.
This quarter, our product enhancements improve operational efficiency for analysts and visibility into potential risks. Learn more about our product updates by watching our July quarterly launch webinar or find details in the drop down below!
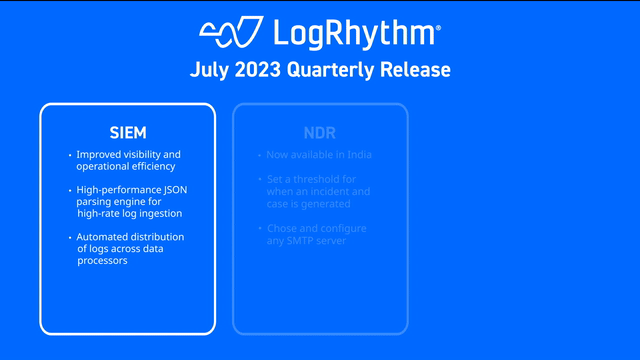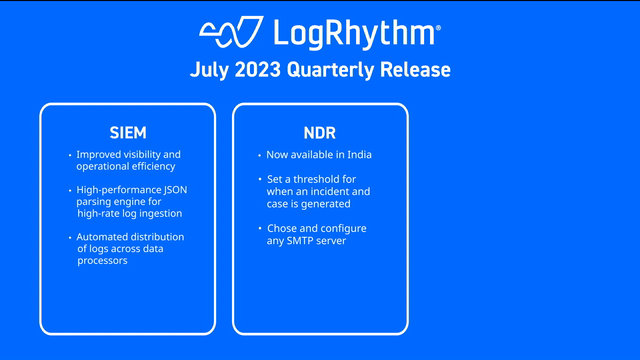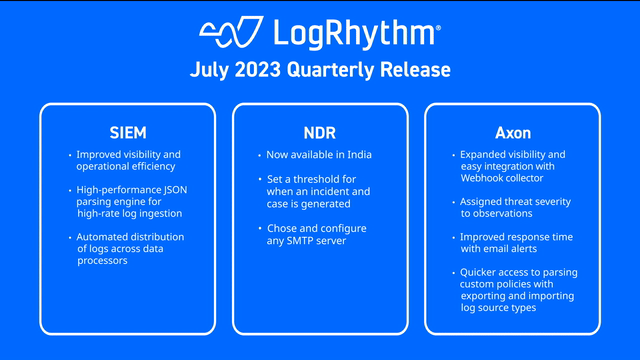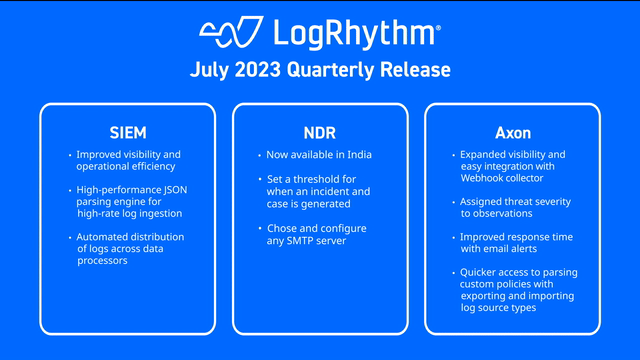
This quarter, we introduced new automation, extended threat detection capabilities, and improved log source management to simplify the analyst experience.
Expanded detection coverage with new out-of-the-box UEBA uses cases:

This quarter’s enhancements span LogRhythm’s product portfolio to enable SOC teams to detect and resolve threats easily and improve analysts’ effectiveness.
“Axon has already given our team the tools to effectively analyze our environment and improve our security posture.” – Eric L., Network Engineer, global manufacturing company
In October, we introduced our brand new, cloud-native security operations platform — LogRhythm Axon! In addition, we launched valuable enhancements to LogRhythm SIEM 7.10, UEBA, and NDR solutions.
To ensure that LogRhythm’s product deliverables are tailored to our customers’ needs, we created the Innovation Portal! This section of the Community contains quick showcases of what’s in development. You’ll find a mix of videos, surveys, and other spotlights — all of which come with an open invitation for feedback.
Let us know your thoughts through the surveys and comments section and signal your general support with a Kudos. We’ll keep a close eye on this section and will steadily supply it with new content.
Let one of our security experts review your uses cases and demonstrate how the LogRhythm can help you reduce noise, prioritize work that matters, and quickly secure your environment.