Visualizations of User/Host Relationships, Live Data Updates, and Quick Onboarding of Cloud Data Sources Make for a Powerful Security Analyst Experience
Boulder, Colo. – July 22, 2020 – LogRhythm, the company powering today’s security operations centers (SOCs), today announced the launch of version 7.5 of the LogRhythm NextGen SIEM Platform, as well as the inaugural release of its Open Collector technology. LogRhythm 7.5 provides enhanced analyst workflow experiences and visibility, while Open Collector simplifies the process of onboarding cloud data sources for more holistic monitoring.
“Organizations produce more data today than ever before, so security teams need comprehensive visibility across their environment,” said Sue Buck, chief technology officer of LogRhythm. “But we also don’t want the amount of data needed for full visibility to ultimately overwhelm analysts. With LogRhythm 7.5, we’re making it even simpler and faster for analysts to get the precise information they need to remediate suspicious or threatening activity.”
LogRhythm 7.5 and Open Collector Benefits
LogRhythm 7.5 and Open Collector make it faster and easier for security analysts to detect and mitigate threats — no matter their level of experience. This is made possible through the following features:
- Faster search speed: Tail search feature automatically and continuously re-runs searches without the need to resubmit a query. This means analysts are guaranteed to see all incoming log data — in real time — related to their investigation.
- Eliminate errors: Security analysts can now reduce the chance of error when creating filters with new, built-in Lucene helper assistance. This results in faster investigations so analysts can spend less time identifying a threat and more time resolving it.
- Visualize data correlation: New Node Link graph feature enables the visualization of the connections between users and hosts in the environment. LogRhythm’s Machine Data Intelligence (MDI) Fabric supplements the graph with contextual data to clearly explain the relationship and type of activity occurring between connections. Instead of being overwhelmed by data from many disparate sources, analysts can use the Node Link Graph to filter data and quickly identify activity and relationships of interest.
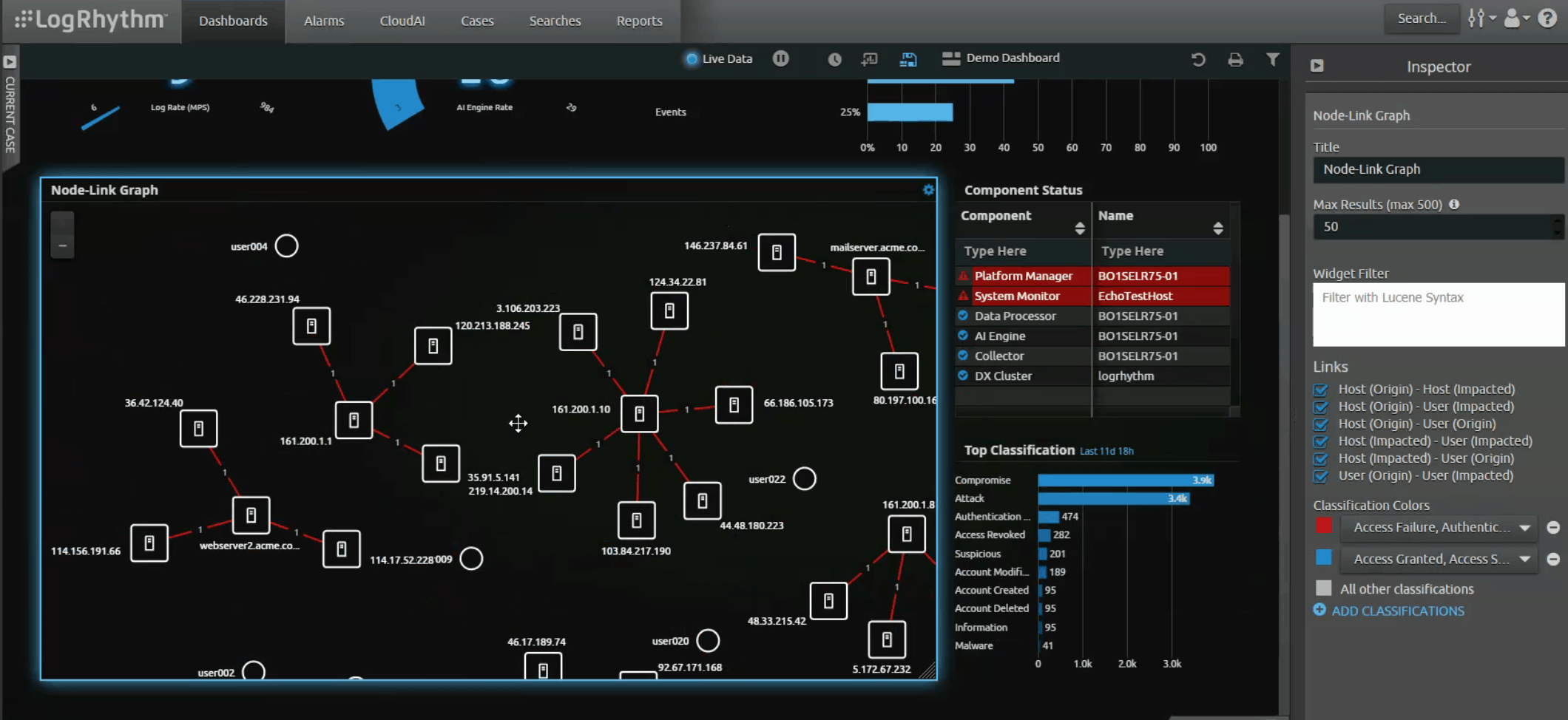
Figure 1: LogRhythm dashboard featuring new Node Link graph.
- Quickly onboard Cloud services: While customers can choose to manually create and customize collection interfaces if desired, Open Collector also provides several premade Beats. This allows analysts to onboard many popular cloud services with minimal administration work. Out-of-the-box Beats include those for Google G Suite, AWS S3, Event Hub and Sophos.
- Reduce administration time: With user-friendly REST APIs, power users can easily use their SIEM data outside of LogRhythm’s consoles. In addition, the APIs make it easier to more deeply integrate LogRhythm into workflows, reducing administrative work within large environments or across multiple deployments for enterprise customers, technical partners and MSSPs.
“Businesses continue to accelerate their digital transformations and adoption of cloud services; with that comes an ever-increasing urgency to maintain visibility across hybrid and cloud-native environments,” said Rusty Carter, chief product officer of LogRhythm. “Our advancements with Open Collector exemplify our continued focus on delivering analytics and orchestration that simplify management of the organization’s security posture — especially as they tackle these challenges.”
Immediate, Global Availability
LogRhythm 7.5 and Open Collector are available today for immediate use. To implement all the capabilities of LogRhythm 7.5, existing customers simply need to follow supported upgrade paths. Customers can download all necessary files to enable Open Collector here.
To see a demo of LogRhythm 7.5, please visit https://logrhythm.com/schedule-online-demo/or email [email protected].
About LogRhythm
LogRhythm helps security teams stop breaches by turning disconnected data and signals into trustworthy insights. From connecting the dots across diverse log and threat intelligence sources to using sophisticated machine learning that spots suspicious anomalies in network traffic and user behavior, LogRhythm accurately pinpoints cyberthreats and empowers professionals to respond with speed and efficiency.
With cloud-native and self-hosted deployment flexibility, out-of-the-box integrations, and advisory services, LogRhythm makes it easy to realize value quickly and adapt to an ever-evolving threat landscape. Together, LogRhythm and our customers confidently monitor, detect, investigate, and respond to cyberattacks. Learn more at logrhythm.com.
