Speed and accuracy of threat detection can mean the difference between a timely and effective security response and a business-impacting incident. But too often, security teams’ detection capabilities are undermined by information overload, visibility gaps, and untrustworthy threat signals.
LogRhythm offers a sophisticated set of out-of-the-box detection techniques that are mapped to proven frameworks like MITRE ATT&CK®, flexible and intuitive customization options, and alerting and automated response capabilities that align with your unique risk factors and compliance needs.
How Effective Threat Detection Helps Your Business
Reduce Time to Detection
Identify and respond to threats before they negatively impact your business.
Focus on What Matters
Harness AI and risk-based prioritization to eliminate noise and prioritize work.
Simplify Your Response
Use best practice and compliance mappings to guide response efforts.
Why LogRhythm Is Your Ideal Threat Detection Partner
LogRhythm helps security teams tune out the noise and focus their efforts where they can have the greatest impact.
Broad Data Analysis Coverage
Our platform combines log, network, and machine data analysis into a unified approach, significantly reducing the risk of visibility gaps and improving detection accuracy.
Sophisticated AI Engine
Our detection approach includes over 900 out-of-the-box correlation rule sets, a drag-and-drop custom rules wizard, and behavioral and statistical anomaly detection.
Threat Intelligence Integrations
An extensive set of open source and commercial threat intelligence feeds can be used to add critical context to activity detected across your environment.
Risk-Based Alert Prioritization
We minimize alert fatigue and enable better resource prioritization by using a diverse set of data inputs to calculate a risk-based priority for detected threats.
Mapping to Best Practice Frameworks
We include pre-built detection content mapped to proven frameworks like MITRE ATT&CK®, making it easier to perform analysis and conduct threat hunting effectively.
Compliance Automation
Our Consolidated Compliance Framework maps detections to dozens of regulations, simplifying compliance and avoiding duplicate alarms for common controls shared across regulations.
LogRhythm’s Threat Detection Products
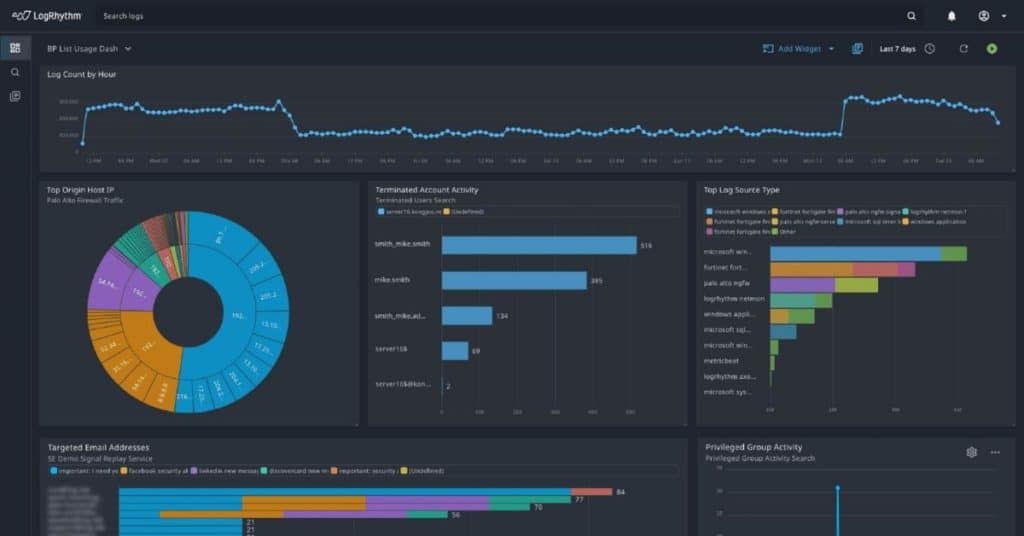
LogRhythm Axon: Cloud-Native SIEM that Puts Analyst Experience First
LogRhythm Axon brings simplicity and an outstanding analyst experience to security teams overwhelmed by complexity and information overload. Powerful security analytics, intuitive workflows, and integrated incident response capabilities give analysts contextual insight into cybersecurity threats so they can reduce noise and act quickly when security incidents occur.
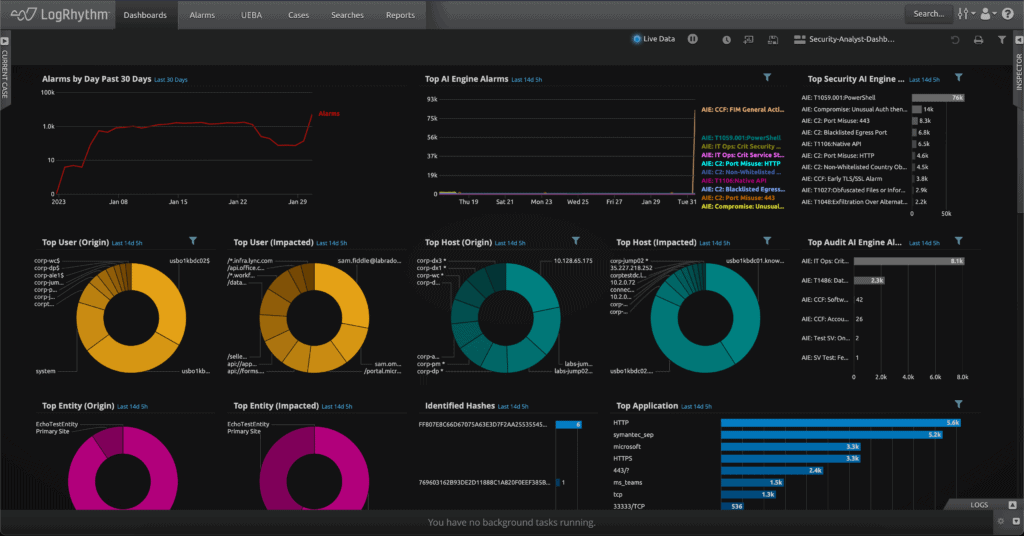
LogRhythm SIEM: Self-Hosted SIEM with Unmatched Customization Flexibility
LogRhythm SIEM helps security teams that require the broadest possible feature set and customization flexibility. Extensive log collection from across all your environments ensures complete threat visibility, and powerful analytics, search capabilities, and integrated security orchestration and response workflows empower your team to respond to, contain, and recover from incidents faster.

LogRhythm Labs Eases The Burden On Your Team
With cyberthreats coming from both outside and within your organization, it’s critical to have a focused team of security experts capable of investigating and researching the latest threats and malicious behavioral patterns to keep your data safe. However, you probably don’t have the luxury of time or resources to staff experts in every area of security intelligence. That’s where LogRhythm Labs helps.
Our LogRhythm Labs team develops and supports threat detection modules, providing your team with an additional resource for threat research, rule creation, and dashboard configuration. Our preconfigured modules deliver a myriad of content for your LogRhythm deployment, including AI Engine content, reports and saved searches, dashboards, and automation actions. LogRhythm Labs’ ongoing in-field and lab-based research ensures your SIEM analytics evolve as fast as current threats.
Recommended Threat Detection Resources
Get Started with Threat Detection
Optimizing your threat detection capabilities will help your security team respond to emerging threats faster and more efficiently, significantly reducing the risk of significant business impact. Schedule a personalized demo to see how LogRhythm can help your team transform your team’s threat detection approach.


