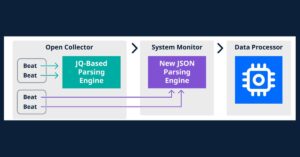
Ingest Cloud-Native Log Sources Faster Than Ever with LogRhythm SIEM
Posted by: Tony Massé
We’ve heard you — onboarding log sources isn’t an easy task. You may have a lot of data to aggregate. Also, the data may be in various states and come from multiple users. Finally, it takes time to process logs,…
Read More
June 29, 2023
Improve Log Source Administration, Management with LogRhythm 7.13
Posted by: Ryan Gamboa
Every quarter, LogRhythm improves customers’ experiences with new innovations that save users time and ease their workflow. With our fifth consecutive quarterly product release, LogRhythm is continuing the momentum with LogRhythm SIEM version 7.13, which features improvements to log source…
Read More
June 29, 2023
Automatically Catch Sight of Critical Threats with LogRhythm Axon
Posted by: Vaughn Adams
With the amount of data continuously feeding into a security operations platform, it is more important than ever to be able to identify the most critical threats and know immediately when those threats are triggered. With the latest LogRhythm Axon…
Read More
June 29, 2023
Q2 2023 Analytic Co-Pilot Use Cases
Posted by: Daniel Chambers
As part of the Subscription Services team, our Analytic Co-Pilot Service consultants worked on a variety of security use cases in Q2 2023 within our own internal environments, as well as our customers. These collaborative efforts continue to grow the…
Read More
June 28, 2023
Top Cybersecurity Threats to Look For
Posted by: Sally Vincent
It’s critical to stay ahead of top cybersecurity threats, but this can be challenging for security leaders, since both sides of the playing field change continuously. The external threat landscape is always evolving, as attackers develop and refine new tools…
Read More
June 22, 2023
Reflections from RSA Conference 2023
Posted by: Matt McGovern
The 2023 RSA Conference was an exhilarating event that brought together cybersecurity professionals from around the world. As we reflect on our experience at the conference, it is clear that the industry is buzzing with excitement, new ideas, and emerging…
Read More
June 8, 2023