How do you stop a threat when you aren’t sure it even exists? You hunt for it.
To be a successful threat hunter, you need to form a hypothesis about the existence of a threat, theorize how to detect it, and stop it. And, to stay one step ahead of your adversaries, you need to see things from the attacker’s perspective.
The MITRE ATT&CK framework is a great starting point for understanding attackers by providing a knowledge base of real-world adversary tactics and techniques.
LogRhythm’s MITRE ATT&CK Module helps you streamline your threat hunting framework through:
- An end-to-end threat hunting workflow that enables you to rapidly spot leading and active indicators of attack
- Custom and prebuilt dashboards that visualize data to unveil known adversarial techniques and tactics
- Out-of-the-box content that saves you precious time and keeps you working in a single user interface
With LogRhythm and the MITRE ATT&CK framework, you’ll be armed with all the tools and information you need to conduct a fruitful threat hunting exercise.
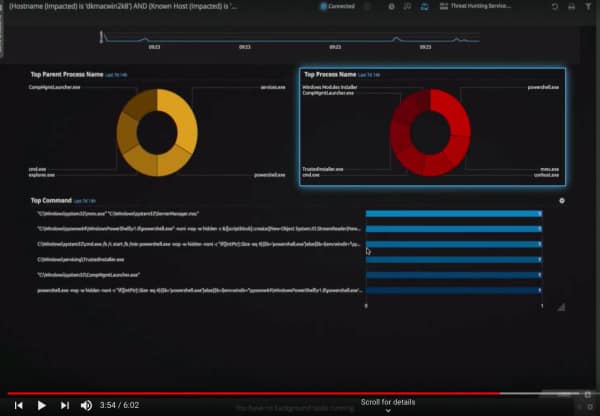
See how it works. Watch the demo today to find out how you can get more out of threat hunting.