Network Detection and Response Defined
Network detection and response (NDR) solutions are advanced security products that use artificial intelligence (AI) such as machine learning to detect and alert potential cyberthreats within an organization’s network. NDR tools help security operations and network security teams obtain full visibility and enhance network detection against a variety of threats such as sophisticated evasion methods (“known unknown” cyberthreats) and brand new zero-day threats (“unknown unknown” cyberthreats).
According to Gartner®, NDR solutions deliver incident response workflow interfaces that inform end users with:
-
- The high-level scope, severity, and probability of an unusual event being malicious.
- Events that are composed of alerts, details, and forensics to validate the maliciousness of the event.
- Recommendations on a course of action to remediate the incident.1
How Network Detection and Response Solutions Works
NDR solutions detect abnormal system behaviors by applying multiple detection models, including machine learning, to network traffic data by tapping into the network, sitting passively, and continuously analyzing raw network packets or traffic metadata in internal networks (east-west) and public networks (north-south) to identify signs of suspicious activity.
NDR solutions provide visibility where logs are not being collected — including critical early-stage attack activities on the network — as well as added contextualization and higher confidence that an attack is occurring. It develops a baseline of normal behavior, and then uses models to identify suspicious patterns.
NDR can help security operations (SecOps) and IT network security teams:
- Protect critical data stores in data centers and the cloud in real time.
- Minimize mean time to respond (MTTR) when addressing attacks. The best NDR solutions enable organizations to decrease the dwell time of threats.
- Eliminate blind spots with rules-based network threat detection and response.
- Integrate with market-leading firewalls, security information and event management (SIEM) and endpoint detection and response (EDR) solutions for comprehensive visibility.
With the vast amount of network traffic that needs to be analyzed, using a combination of both rules-based detection and machine learning is imperative to ensuring higher fidelity alarms across the network. NDR solutions should use analytics and surface the most pertinent threats to your organization; enabling security and network teams to focus on the threats that are the most important for investigation.
Why Do You Need an NDR Solution?
Digital transformation has upended the cybersecurity landscape. With the market shifting due to the Internet of Things (IoT), artificial intelligence (AI), a hybrid workforce, remote working, and cloud adoption, the demands placed on security and network teams is greater than ever.
Gaps in visibility across the landscape are expanding and the amount of network traffic that must be analyzed to prevent attacks is growing exponentially every day. Relying solely on perimeter tools enables attackers to infiltrate your network as they are always learning and adapting.
Limitations of Signature-Based Security Solutions
Security teams cannot solely rely on legacy security tools like intrusion detection and prevention systems (IDS/IPS) or only SIEM/EDR solutions for a network security strategy. Primarily preventive security, signature-based tools cannot detect new attacks unless signature rules have been previously written to recognize the attacks on the network.
By tapping into the network and examining all traffic packets, NDR products focus on the status of all entities (users and hosts) and correlates related attack indicators and provides a more complete view of an event. NDR solutions provide teams with real-time awareness of relevant network activities to detect network-borne threats as quickly as possible.
Use Cases that NDR Solutions Solve
Detecting Ransomware Attacks
Ransomware typically bypasses malware protection. NDR offers a proactive way for companies to detect ransomware attacks in real time before they receive the ransom note. Unauthorized access is recognized by monitoring behavioral patterns from the database. When anomalous behavior is recognized, NDR surfaces an incident that notifies an analyst the need to investigate.
Identifying Command-and-Control Activity
A command-and-control (C&C or C2) server is defined as a cybercriminal’s server, which can be a single machine or a botnet of machines. These servers mimic trusted or unmonitored traffic to avoid detection for as long as possible. Usually, network security defenses are less reliable so while the first infected device may not be the primary target, it is a way into the system. NDR products will recognize the abnormal behavior and raise an incident in order to reduce the dwell time of the attack.
Stopping Data Exfiltration
The act of moving sensitive data out of an environment and into control of an attacker, data exfiltration enables adversaries to gain access to proprietary information from companies. By monitoring sensitive data movement, NDR can catch the cyberattack before an adversary is able to exfiltrate the data.
Detecting Lateral Movement Across the Network
When an attack can move laterally from the initial infected device to move closer to target data. It is hard to detect as lateral movement mimics normal network traffic. Beyond the typical signature-based solutions, NDR enables visibility into a wider range of traffic. With anomalous detection capabilities, NDR surfaces these threats for immediate investigation.
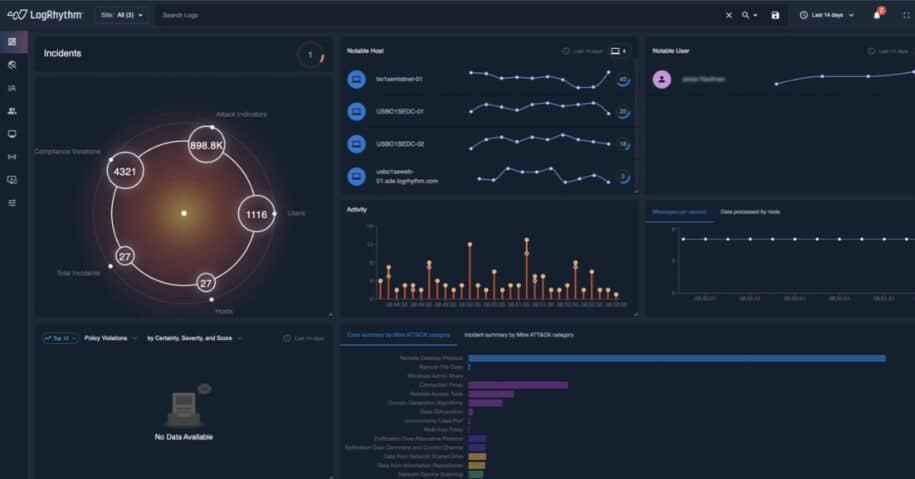
How LogRhythm NDR Can Help with Your Network Security
LogRhythm NDR enables you to understand what is happening in your environment through a holistic analytical approach and a patented mesh architecture. LogRhythm NDR provides higher fidelity alarms as it utilizes both signature-based and machine learning (ML)-driven network threat detection techniques and a built-in MITRE ATT&CK™ Engine to eliminate blind spots and monitor your organization’s network in real time. Learn more about LogRhythm NDR, by visiting our product page here.