Reduce risk in your organization
Manufacturing cybersecurity solutions are critical as companies are seeing an increase in cyberattacks associated with control systems used to manage industrial operations.
But despite the importance of securing industrial manufacturing, many security professionals working in operational technology (OT) have limited resources and a lack of visibility, making it difficult to correlate log data across disparate systems.
To reduce cyber risk in manufacturing, you need a solution that extends across IT and OT to effectively combat cyberattacks. Watch how the LogRhythm SIEM platform matures your operations and streamlines visibility to scale your threat detection and response.

Manufacturing cybersecurity challenges
Digital transformation
Initiatives like Smart Manufacturing and Industry 4.0 drive digital transformation in OT. But as connectivity in the Industrial Internet of Things (IIoT) continues to accelerate and legacy technology remains in place, securing industrial control systems (ICS) becomes a larger challenge.
Vulnerable assets
Manufacturers are a high target for cybercriminals. Hackers seek to infiltrate intellectual property, customer financial information, and propriety information, as well as attack control systems that disrupt production processes.
Compliance and regulations
Manufacturers can face regulatory and compliance challenges with increasing and evolving environmental and safety standards.
Manufacturing cybersecurity use cases
Legacy industry-specific systems combined with new IoT-related technologies are susceptible to attacks. Here are some manufacturing cybersecurity use cases to consider:
Ransomware
Manufacturers have an extremely low tolerance for downtime with the production process. Attackers use malware to hack operational technology, such as ICS for financial gain.
Data exfiltration
Disgruntled employees have direct access to various systems and can act maliciously by carrying out unauthorized data transfers.
Third-party tactics
Adversaries leverage third parties to conduct espionage, steal proprietary information, or initiate a potentially disruptive OT attack.
Phishing attacks
Cybercriminals often reach out to other factory employees or executives from a victim’s corporate email address to solicit personal information, gain access to accounts, or for financial schemes.
Insider threats
Hackers can gain a foothold when employees are connecting to business networks from several devices, including mobile, instead of company-issued and vetted machines.
Build manufacturing cybersecurity resilience
LogRhythm’s Security Operations Maturity Model (SOMM) provides a framework that will help evaluate your organization’s maturity level. Learn how to measure your team’s effectiveness and how to improve your overall security posture with SOMM.
Cybersecurity solutions for manufacturing operations
LogRhythm NDR
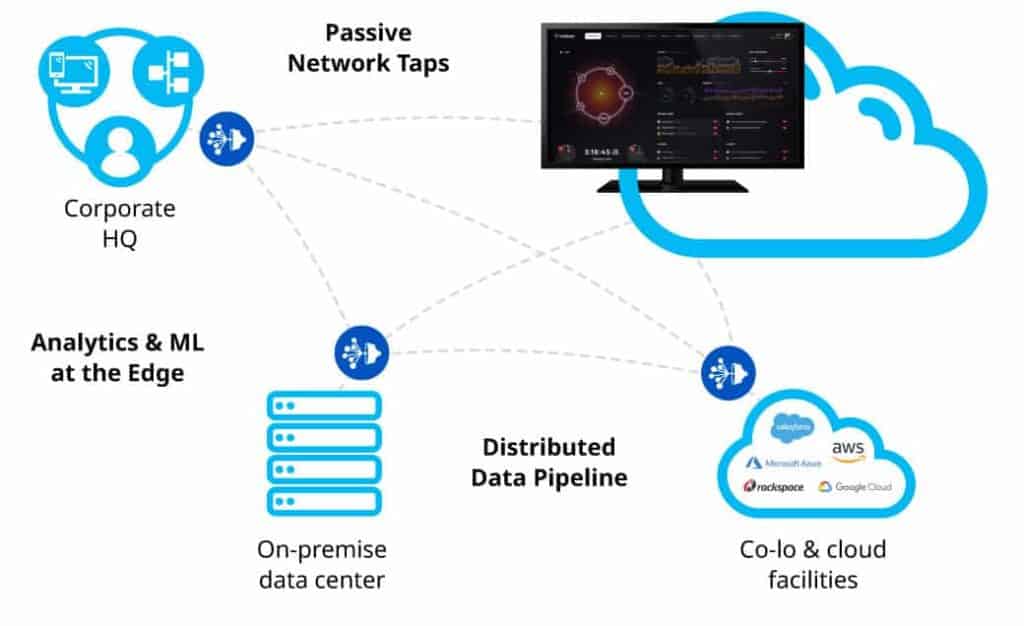
To defend against cyberthreats in the evolving OT landscape, your organizations must capture, correlate, visualize, and analyze forensic data to drive actionable insight — in real time.
Maximize your network detection and response (NDR) with our cloud-based, machine-learning solution that uses distributed computing to scale data collection and analytics with lower operating costs. Learn more about how you can eliminate your blind spots with LogRhythm NDR.
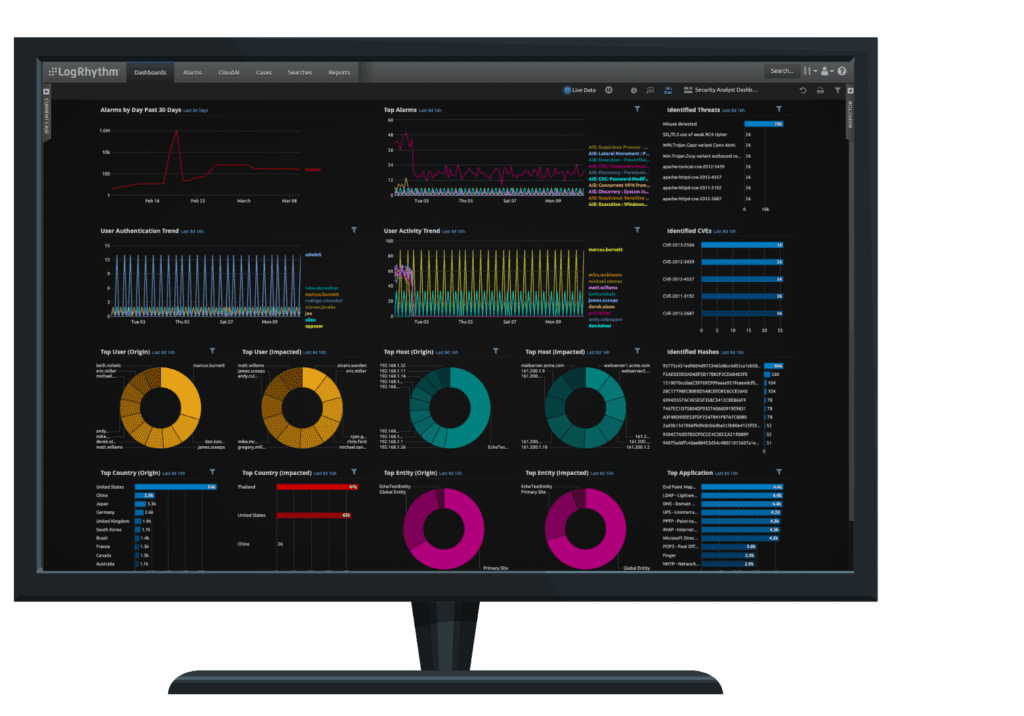
LogRhythm SIEM
- Endpoint monitoring
- Network detection and response
- Log management
- Security analytics
- User entity and behavior analytics (UEBA)
- Security automation and orchestration (SOAR)
We support your future growth and scalability needs
When it comes to manufacturing cybersecurity, your organization has unique requirements and that’s why our pricing and licensing models are the most flexible in the industry. Find out what best fits your custom needs!
