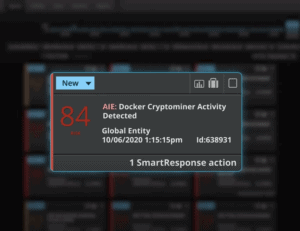
Docker containers are critical to your DevOps Engineers. However, when containers aren’t properly monitored, they can open the door for attackers who are looking to mine for cryptocurrency on an organization’s hardware.
Don’t fall victim to this kind of attack! Watch how LogRhythm can help you stop a cryptojacking attack via automated response in this demo.
Discover how the LogRhythm SIEM can:
- Identify cryptomining malware hiding among the many legitimate containers in your DevOps environment
- Alert you of malicious keywords within your environment to help you quickly locate unapproved containers
- Use playbooks and automated SmartResponse™ automation to stop the malicious container and prevent cryptojacking
- Discover where the attack initiated so your team can prepare for future attacks
Access our Docker Containers: Cryptojacking Goldmines demo to see how the LogRhythm SIEM platform can stop cryptojacking in its tracks.