New Security Information & Event Management (SIEM) module will be on display at Black Hat
Boulder, CO — July 31, 2019 — LogRhythm, the company powering the world’s most modern enterprise security operations centers (SOCs), announced today that it released a complimentary module that aligns the LogRhythm NextGen SIEM Platform with ATT&CK, “a curated knowledge base and model for cyber adversary behavior.” 1 The module’s content corresponds with tactics, techniques and procedures (TTPs) as categorized by ATT&CK and will be on display at Black Hat (booth #614).
With this, LogRhythm makes it easy and cost-effective to use the standard to develop a threat-informed security strategy. ATT&CK allows red and blue teams around the world to learn and communicate about a variety of threats in a consistent — yet granular — way.2 By using LogRhythm’s module, security teams can take this a step further to automatically detect pre-vetted anomalous behaviors and assess security effectiveness.
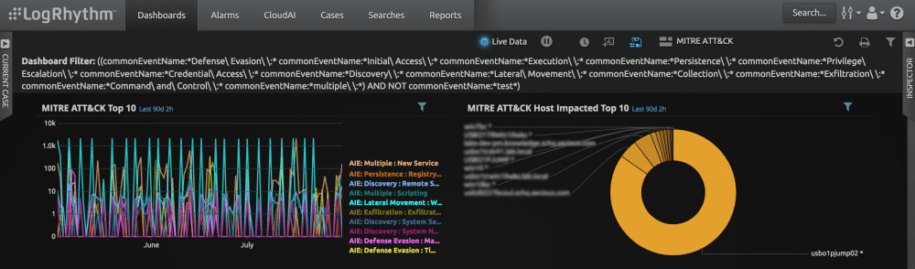
Figure 1: Pre-defined ATT&CK dashboard included with module
ATT&CK currently contains over 220 techniques derived from publicly reported incidents and offensive research.3 Version 1 of LogRhythm’s module includes predefined correlation rules and dashboard content that focuses on a subset of these techniques. LogRhythm Labs will make additions to the module until its out-of-the-box content addresses every technique available.
To provide an extra layer of security assuredness, the module can be used alongside third-party ATT&CK simulation tools to run automated penetration tests. These tools replicate situations and behaviors included in the matrix. With this content at their fingertips, LogRhythm customers can identify gaps in their environment — allowing ATT&CK-specific threats to break through and validate that their content is working as desired — before a real threat manages to wreak havoc.
“The ATT&CK matrix is the most comprehensive list of TTPs available to the industry today; not only does it aid in quick threat detection and response, but it also enables security analysts to attribute those threats to specific actors. It’s no surprise that modern SOCs have quickly embraced the matrix,” said James Carder, CISO, LogRhythm. “And because LogRhythm powers the most modern SOCs, it made perfect sense to align the power of platform with that of ATT&CK. We believe that this combination of cybersecurity intelligence, content and capabilities is the absolute best to ensure SOCs stay on top of the ever-evolving threat landscape.”
This release supports LogRhythm’s larger mission of helping organizations assess the current maturity level of their security operations and plan for improved maturity over time. To guide the process, earlier this year LogRhythm introduced its Security Operations Maturity Model (SOMM), which organizations can use to quantify the effectiveness of its security program — ranging from Level 0: Blind to Level 4: Resilient. Advanced analytics designed to detect TTP-based scenarios — like those featured in the ATT&CK module — are prerequisites for reaching the top maturity levels.
Black Hat attendees can demo the module by visiting LogRhythm’s booth (#614). Current LogRhythm customers can implement the ATT&CK module by ensuring their Knowledge Base is up to date, and LogRhythm customers attending RhythmWorld 2019 can register for a session led by LogRhythm Labs to learn additional tips and tricks for using the module.
More information on the module can be found here. For additional details on LogRhythm, please visit the website.
About LogRhythm
LogRhythm helps security teams stop breaches by turning disconnected data and signals into trustworthy insights. From connecting the dots across diverse log and threat intelligence sources to using sophisticated machine learning that spots suspicious anomalies in network traffic and user behavior, LogRhythm accurately pinpoints cyberthreats and empowers professionals to respond with speed and efficiency.
With cloud-native and self-hosted deployment flexibility, out-of-the-box integrations, and advisory services, LogRhythm makes it easy to realize value quickly and adapt to an ever-evolving threat landscape. Together, LogRhythm and our customers confidently monitor, detect, investigate, and respond to cyberattacks. Learn more at logrhythm.com.
1 MITRE, MITRE ATT&CK™: Design and Philosophy, July 2018, iii.
2 Zaid Shoorbajee, “Experts Advocate for ‘ATT&CK’ as Go-To Framework to Share Threat Intel,” CyberScoop. October 13, 2018.
3 MITRE, 15.