Get to know LogRhythm UEBA
As cyberattacks continue to grow in volume and sophistication, it’s more important than ever to have greater detection capabilities with advanced analytics.
LogRhythm UEBA uses machine learning to detect user-based anomalies and helps analysts prioritize the findings for investigation and response.
A Guide to User and Entity Behavior Analytics (UEBA)
Insider threats remain a constant concern for organizations. In this white paper, learn all about UEBA and how you can reduce risk to user-based threats.
Defend your organization with advanced user behavior analytics
With the shortage of qualified analysts, inefficient manual processes, and complexity of attacks, it’s crucial to have a user and entity behavior analytics solution that provides extra layers of detection to protect the organization against potential threats.
LogRhythm enhances your threat detection coverage in addition to existing out-of-the-box AI Engine UEBA rules. LogRhythm UEBA helps detect outliers and automatically sets scores without the need of explicit defined logic.
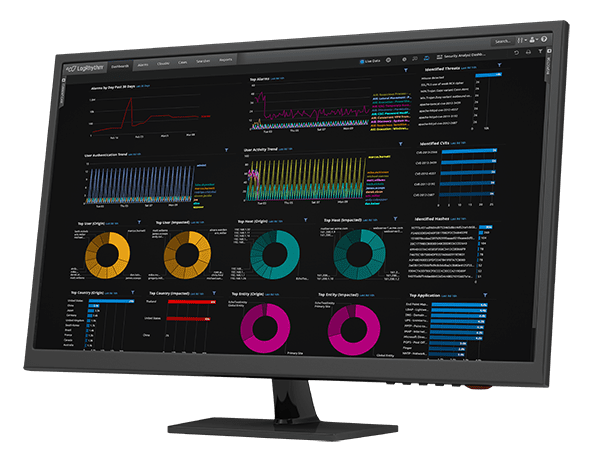
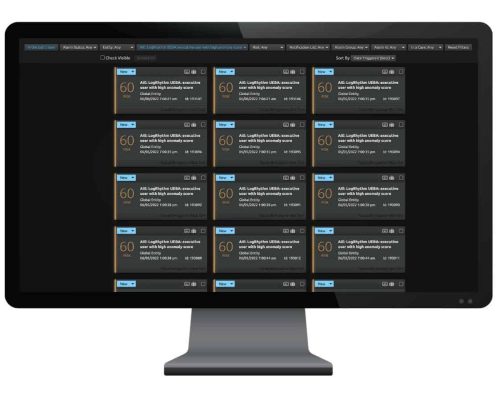
As a cloud-native add on, LogRhythm UEBA functions as an advanced UEBA log source in the LogRhythm SIEM platform. You can build customizable dashboards, run and save searches, and leverage AI Engine rules setting alarms and SmartResponse™ automated actions.
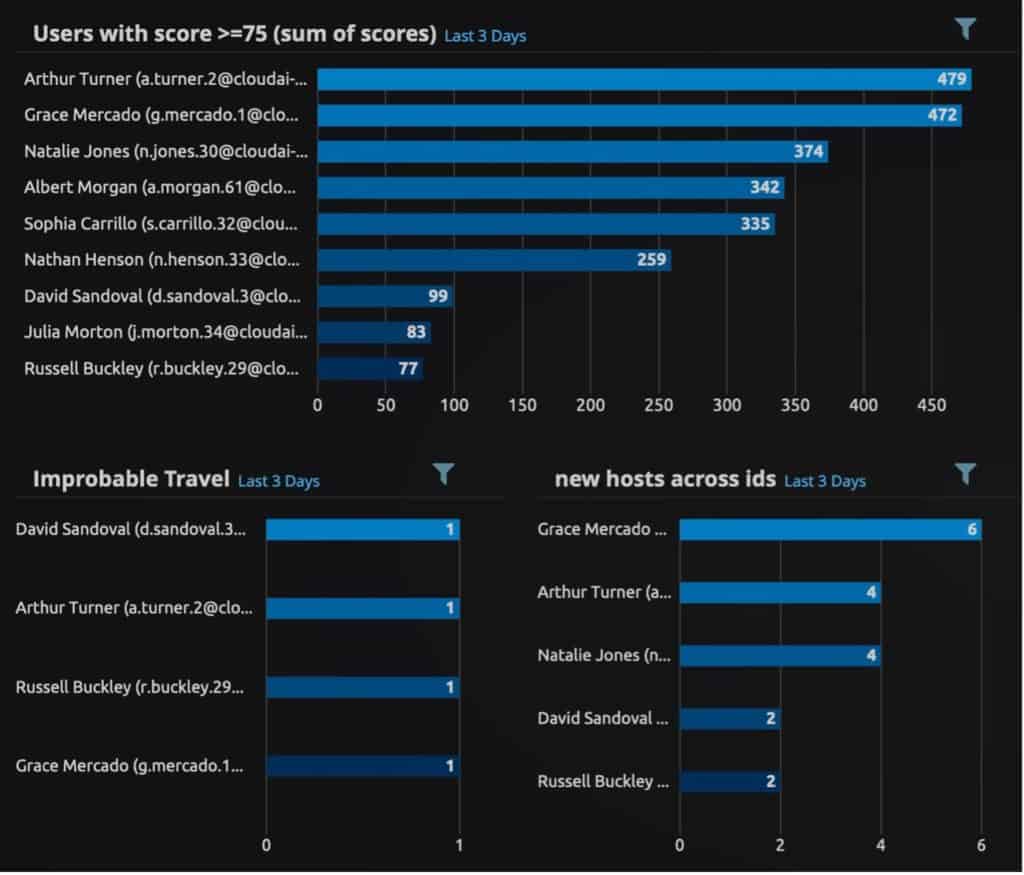
Analysts can use the individual anomaly scores and a summary user score to prioritize anomalies for investigation and response.
Self-evolving ML for faster threat detection and analysis
With LogRhythm UEBA, your team’s threat detection improves by applying self-evolving ML algorithms for security across enormous, cloud-based centralized datasets.
LogRhythm UEBA can help you detect:
- Insider threats
- Account compromise
- Privileged account abuse and misuse
Watch the LogRhythm UEBA webinar
LogRhythm UEBA applies self-evolving analytics against long periods of user data to detect anomalies that indicate a potential threat. Join Senior Technical Product Manager and Data Scientist, Melissa Ruzzi, for a breakdown of our user behavior analytics capability.
Get ready to defend with LogRhythm UEBA
Solve today’s threats — and tomorrow’s too
With a cloud-native architecture, enhancements are introduced immediately. Your team will be prepared to solve for not just today’s threats — but also the inevitable advanced threats that will come your way.
Achieve rapid time to value
Start benefiting immediately with cloud delivery. Plug-and-play implementation lets your team focus on their mission instead of spending valuable time implementing and maintaining a new tool.
Get smarter, faster
Accelerate threat detection
As a fully integrated add-on for the LogRhythm SIEM platform, LogRhythm UEBA gives your team unparalleled detection by using machine learning to detect hard-to-find anomalies.
Leave data preparation to LogRhythm
LogRhythm helps customers prepare and analyze metadata using LogRhythm’s Machine Data Intelligence (MDI) Fabric. The MDI framework provides data enrichment and normalization with unique, rich metadata, and contextual information that feeds into the LogRhythm SIEM platform into LogRhythm UEBA.
A solution for every environment
With LogRhythm UEBA, you can quickly detect and respond to user-based threats. Whether delivered as an integrated component of LogRhythm SIEM or as a standalone UEBA product, there is a powerful and efficient solution available to empower your organization to address user-based threats.
Learn more about LogRhythm UEBA
LogRhythm UEBA is SOC-2 compliant and will help you reduce risk with additional layers of detection. To learn more about how our advanced UEBA solution can address your specific use cases, schedule time with one of our product experts.
Schedule a Live Online Demonstration with an Expert
Let’s find a time that is convenient for your team.
Complete the form below to schedule your demo.