The ‘Security Spotlight’ series of blogs is written in accompaniment with the YouTube series of the same name, which is aimed at providing quick visibility and understanding into how you can leverage the LogRhythm platform against a variety of threats.
In this Security Spotlight, we’ll be talking about the Credential Dumping technique used to steal information within the Local Security Authority Subsystem Service (LSASS).
What is Local Security Authority Subsystem Service (LSASS)?
The LSASS is a process in Windows operating systems that enforces the system’s security policy. It verifies users logging in to a Windows computer or server, handles password changes, and creates access tokens.
When you log in to a Windows account or server, the lsass.exe process verifies the login name and password and keeps this information in its memory. This is why when you terminate the process, you find that you’ve been logged out of Windows. Furthermore, LSASS writes logs to the Windows Security Log for authentication attempts, along with other security policy information.
Why should you to protect your LSASS process?
Knowing this, it isn’t difficult to see why it is essential to protect the process execution and the information stored within LSASS. Adversaries who manage to attain this stored information can use it to progress on the attack chain in numerous ways, such as:
- Assessing confidential information and critical assets
- Moving laterally in a target network to access other systems
- Creating and removing accounts to hide malicious actions
Adversaries can obtain the credential information stored within LSASS using various methods. One such method involves utilizing the comsvcs.dll Windows library, which employs a function called MiniDumpW which is designed specifically to be used with rundll32. Once a dump file is created, it becomes relatively straightforward for adversaries to access the Administrator or System Authority account details.
As LSASS is a fundamental component in every Windows Operating System, throughout the years, we have observed numerous instances of malware employing credential dumping as part of a larger attack chain. Consequently, strong user credential policies that are supported by multi-factor authentication (MFA) or one-time password (OTP) mechanisms are imperative for all organizations. Monitoring the execution of lsass.exe, along with rundll32 execution in conjunction with comsvsc.dll, will go far in enhancing visibility and our ability to respond promptly.
How can LogRhythm help you?
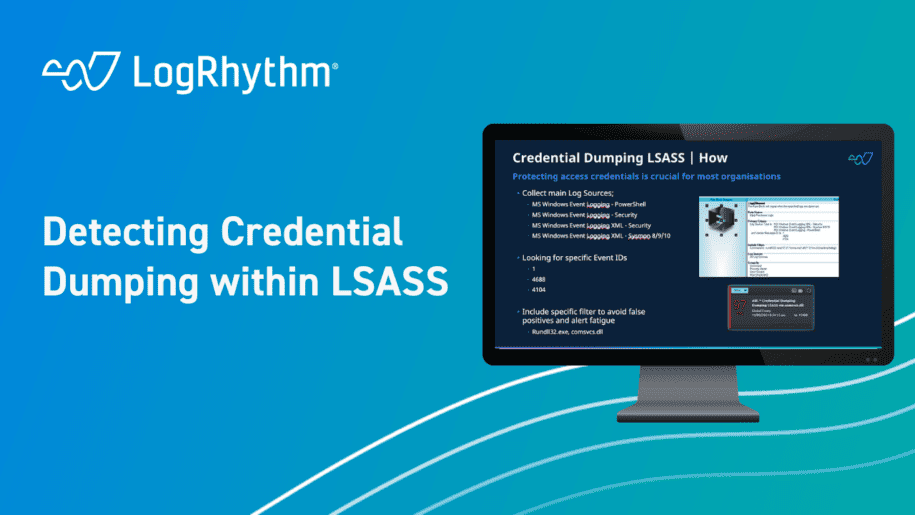
The LogRhythm Co-Pilot team has devised a rule that uses advanced Windows logging, specifically PowerShell and Sysmon logging, to detect when certain event IDs are triggered. By actively monitoring for these and creating a regex designed to detect the hallmarks of credential dumping, we can establish an early warning system that maps against future attacks the malicious actors are likely to undertake.
In addition, for teams with advanced capabilities, it is possible to utilize LogRhythm SIEM’s embedded SOAR capabilities to automatically terminate suspicious processes when this alert is triggered.
For more information on how to enable these rules within your LogRhythm deployment, check out our community page to read more, download, and then import the rule into your platform.
For other Security Spotlight episodes, you can access the full playlist here.