In the wake of recent cyber attacks targeting governmental agencies, the need for robust cybersecurity measures has never been more pressing. Most recently, the hacking group R00tK1T has been in the spotlight for its sophisticated campaigns against the cybersecurity infrastructure of Malaysia. In the face of these evolving threats, governmental agencies must prioritise defending against data exfiltration—a critical aspect of cybersecurity.
Lessons from Recent Attacks
One of the most notable attacks by R00TK1T on Malaysian entities was the access and exfiltration of 27TB worth of data from the National Population and Family Development Board of Malaysia (LPPKN). The group has since publicised their results via social media, showing screenshots of the files and folders as evidence of their successful attack. For governmental agencies, protecting classified data is paramount, and the consequences of data breaches can be severe, ranging from compromised national security to the exposure of citizens’ personal information.
Dealing with Data Exfiltration
One of the primary objectives of cybercriminals, like R00TK1T, is data exfiltration—the unauthorised extraction of sensitive information from targeted systems. Aside from the recommendations by the Malaysian National Cyber Coordination and Command Centre (NC4), here are some key strategies to defend against data exfiltration:
-
Advanced Threat Detection:
- Implement cutting-edge threat detection solutions such as Network Traffic Analysis, capable of identifying and mitigating advanced persistent threats (APTs).
- Leverage machine learning and behavioural analytics to detect anomalous patterns indicative of data exfiltration attempts.
-
Continuous Monitoring of Files and Users:
- Monitor file views, modifications and deletions, as well as permissions changes. Organisations can use file integrity monitoring solutions to know if a file has been compromised or altered.
- Implement a User Entity Behaviour Analytics (UEBA) solution to help understand and identify anomalous user behaviour.
- Utilise a Security Information and Event Management (SIEM) solution to centralise log data and facilitate timely threat detection.
-
Strengthen Endpoint Security:
- Strengthen endpoint security to prevent unauthorised access to government networks by employing robust encryption protocols and ensure that all devices connecting to government systems adhere to stringent security standards.
-
Implementing Zero Trust:
- Implement a Zero Trust security model, eliminating perimeter-based defence and focusing on strict authentication at each access point. This model ensures no device, user, system, or workload is trusted by default, regardless of the location it is operating from.
- Ensure that critical systems are isolated and have limited access points.
-
Data-Centric Protection
- Understand which data is considered “confidential,” and implement strict data protection and control surrounding those data.
-
Incident Response Planning:
- Develop and regularly update incident response plans to swiftly address and mitigate the impact of data exfiltration attempts.
- Conduct simulated exercises to test the efficacy of response protocols.
-
User Awareness and Training:
- Educate government employees on cybersecurity best practices to minimize the risk of falling victim to phishing attacks or other social engineering tactics.
- Foster a culture of cybersecurity awareness within governmental agencies.
Using LogRhythm to Prevent Data Exfiltration and Theft
Out of the box, LogRhythm has more than 2000+ rules that can be used for different use cases. In this example, let’s go through how LogRhythm can monitor, detect, and protect against data theft and exfiltration:
-
Sensitive Data Exfiltration Use Case
In the use case, sensitive and confidential files are defined along with the approved handling process. Should it deviate, LogRhythm will be able to alert the SOC team on who’s trying to exfiltrate what kind of data.
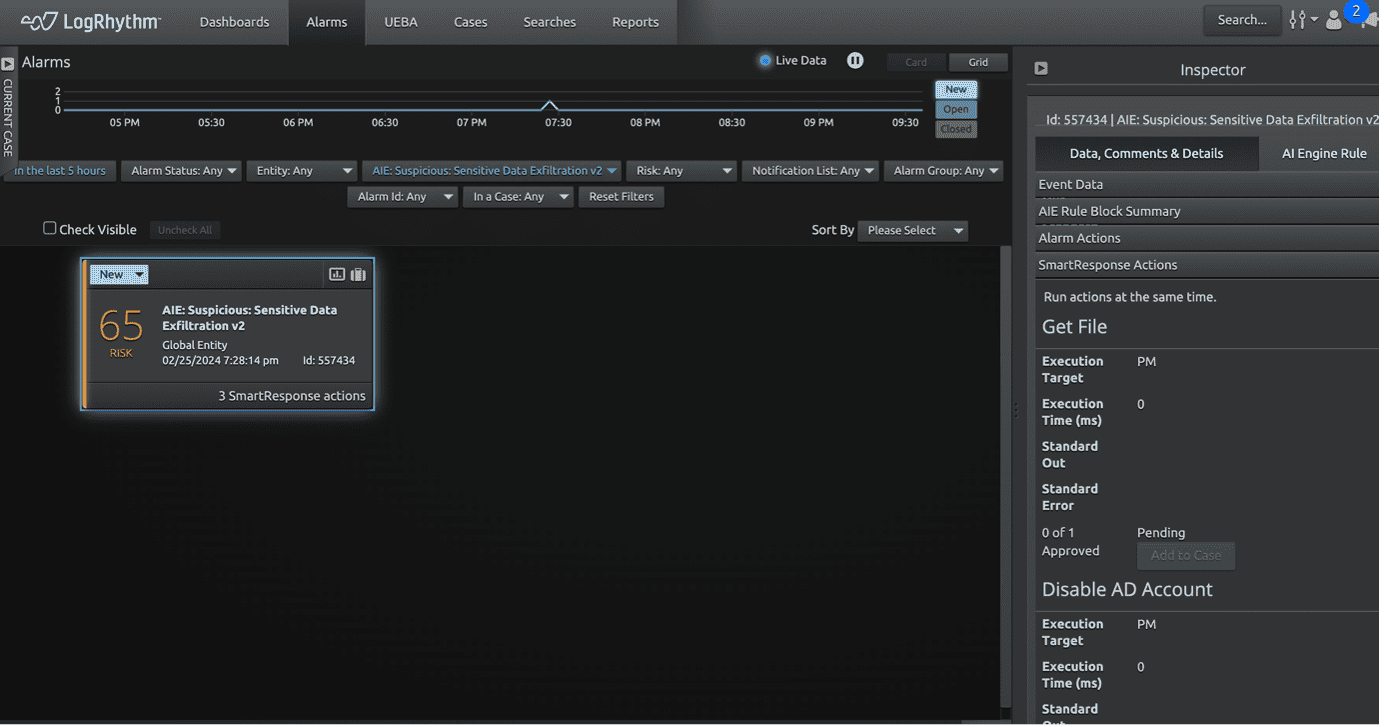
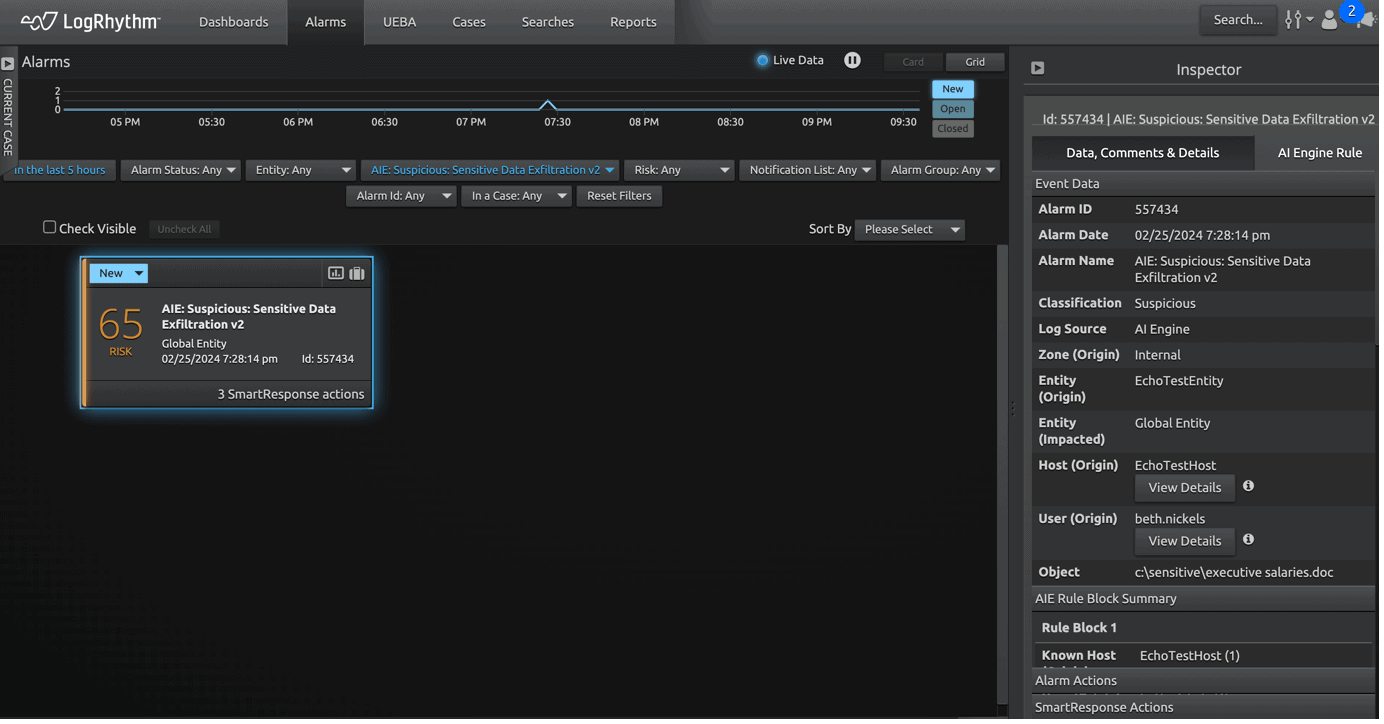 In the screenshot below, LogRhythm not only detected a potential exfiltration attempt, but also tried to stop the activity and disable the user that’s trying to make the attempt.
In the screenshot below, LogRhythm not only detected a potential exfiltration attempt, but also tried to stop the activity and disable the user that’s trying to make the attempt.
-
Monitor Abnormal Confidential/Sensitive Files Activity
Similar to the above, sensitive and confidential files are defined along with the approved process or application. In this case, LogRhythm will give indication of abnormal activity if there are new processes trying to access these files, and if there are attempted deletions of the files.
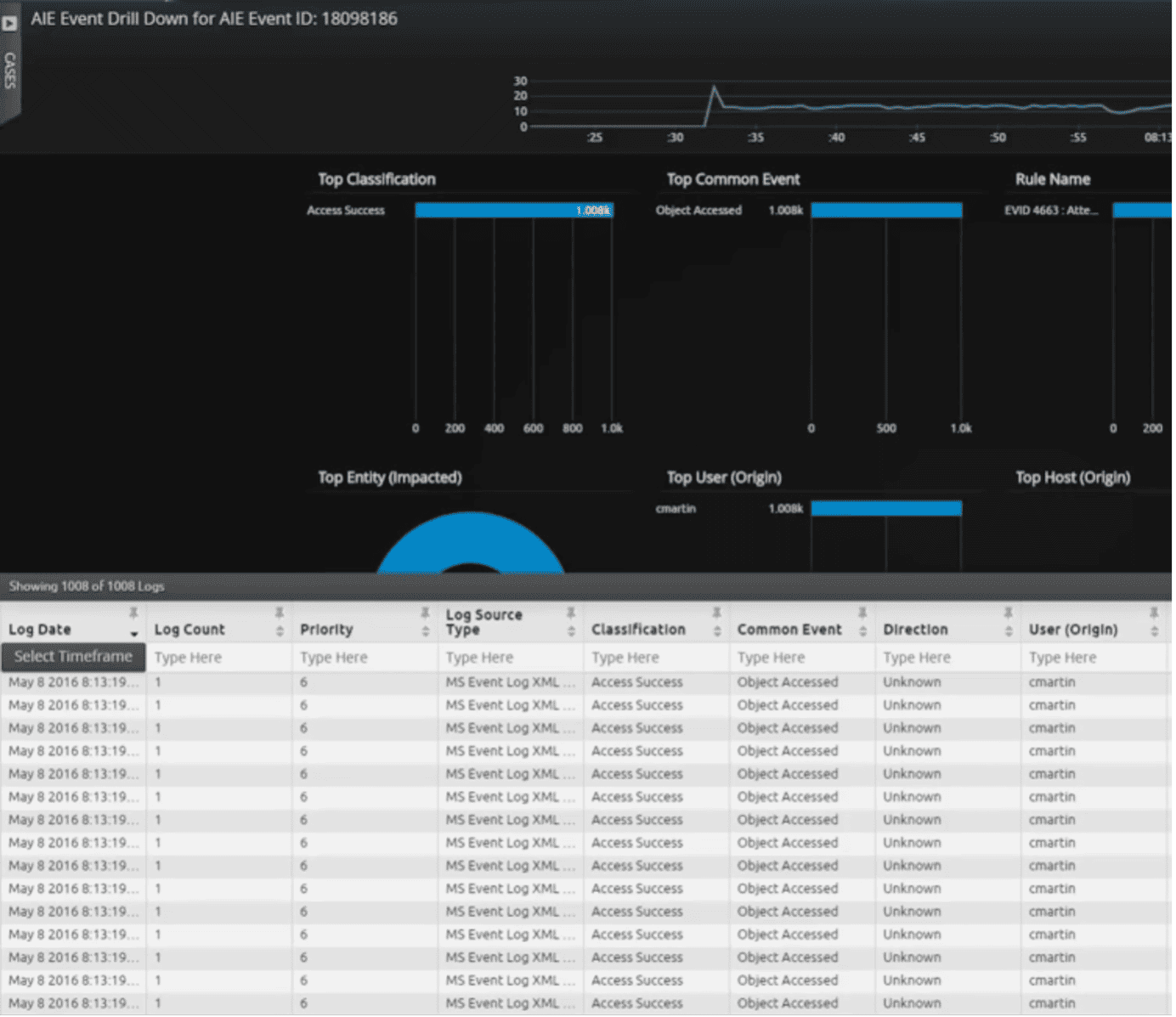
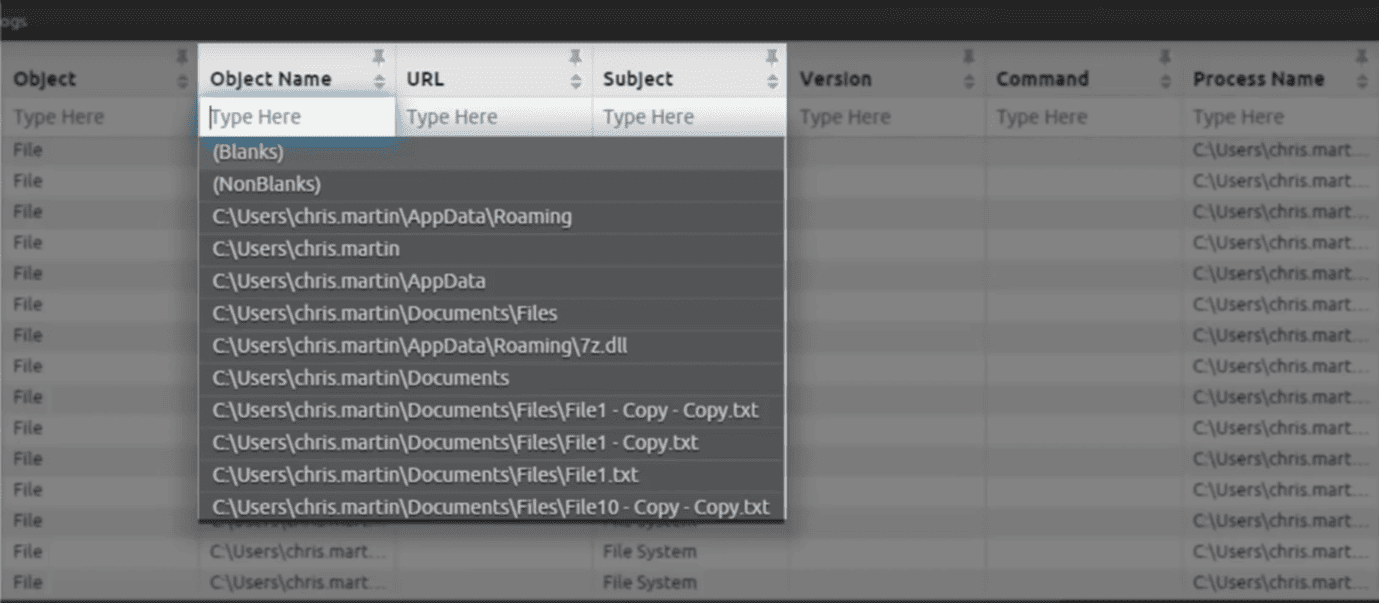 You can also drill down into abnormal file activities to uncover the new process that triggered the alert. In the screenshot below, we see a possible indication of a malware/ransomware activity.
You can also drill down into abnormal file activities to uncover the new process that triggered the alert. In the screenshot below, we see a possible indication of a malware/ransomware activity.
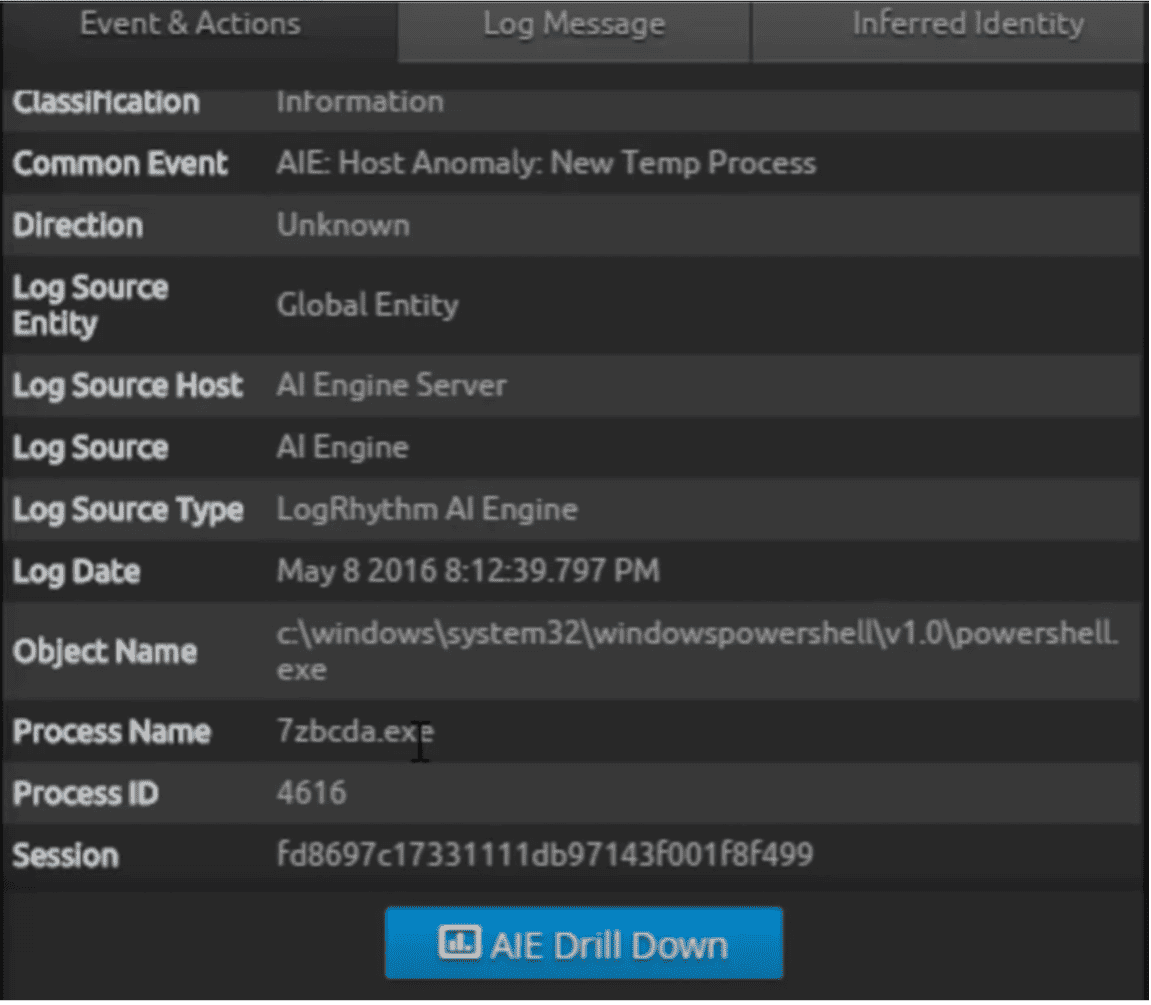
-
Monitor Anomalous Network Traffic
LogRhythm Network Traffic Analysis is able to monitor network protocols typically associated with malicious intents such as tunnelling applications, as they can be used by attackers to bypass security control to transfer confidential/sensitive information.
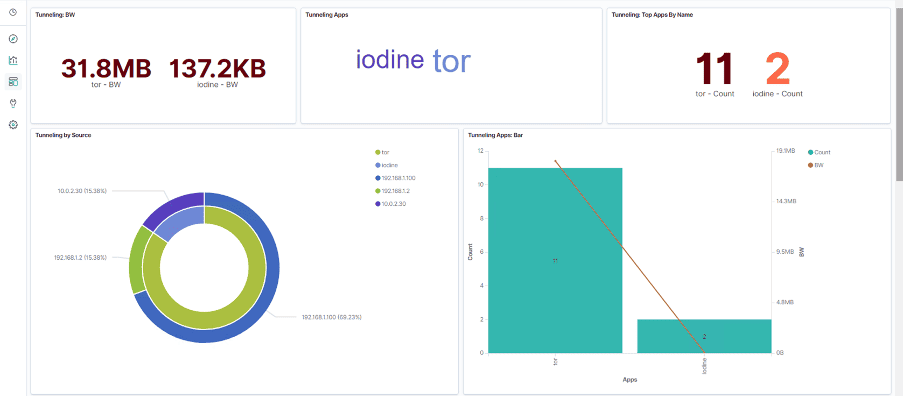
We can also monitor suspicious Top Level Domain traffic that resembles beacons from the attacker.
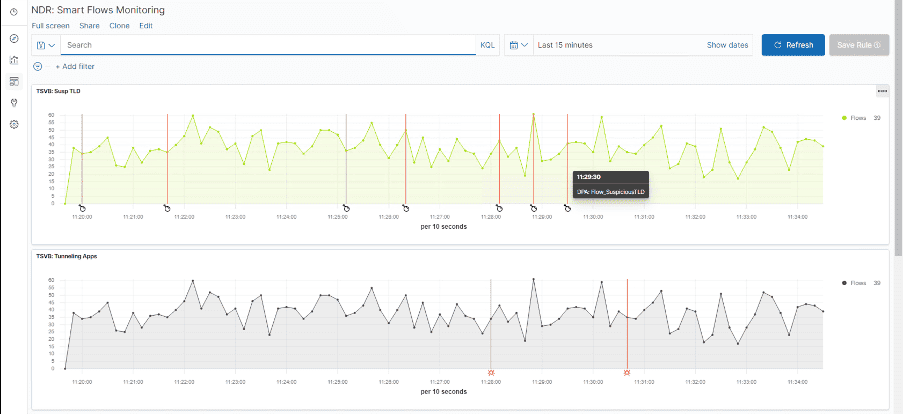
Another use case relevant is monitoring for known attacks such as ransomware traffic. Here, we are monitoring for Eternal Blue/WannaCry.
-
Monitor Movement of Confidential Information
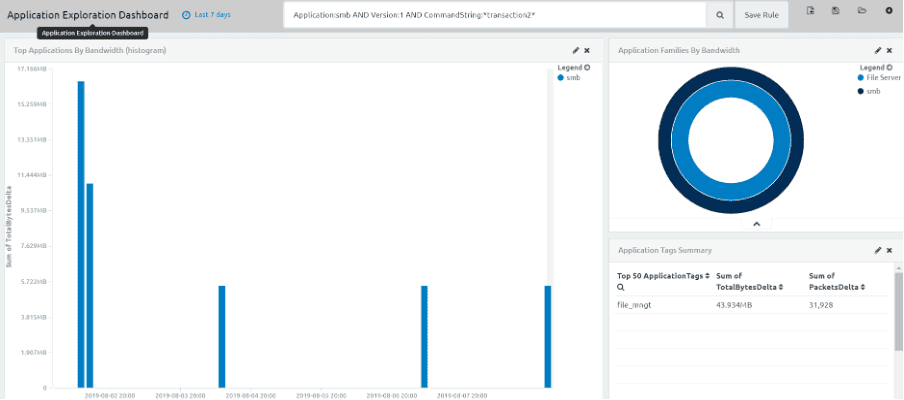
LogRhythm comes with the Deep Packet Inspection (DPI) engine, giving you a deep understanding of your network activity in an easy-to-access format. It identifies and categorises more than 3500 applications at wire speed and populates thousands of metadata fields. With Deep Packet Inspection (DPI) rules and analytics, LogRhythm able to monitor if confidential/sensitive information is being transferred over network traffic.
For example, in this screenshot we can see LogRhythm revealing that credit card information is being transferred through the network.
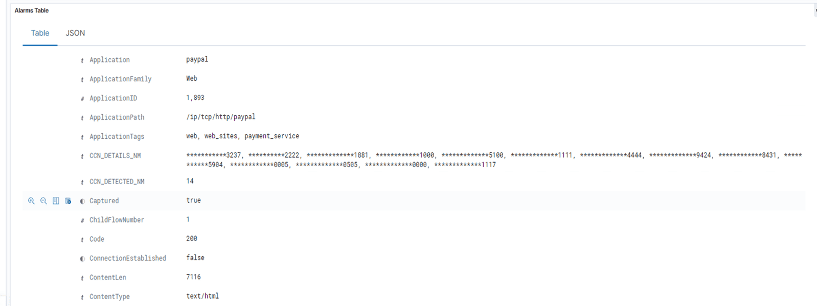
-
Monitor User Behaviour
LogRhythm provides the capability to monitor user behaviour without additional hardware. Here, the LogRhythm UEBA monitored and highlighted accounts that could have been maliciously taken over.
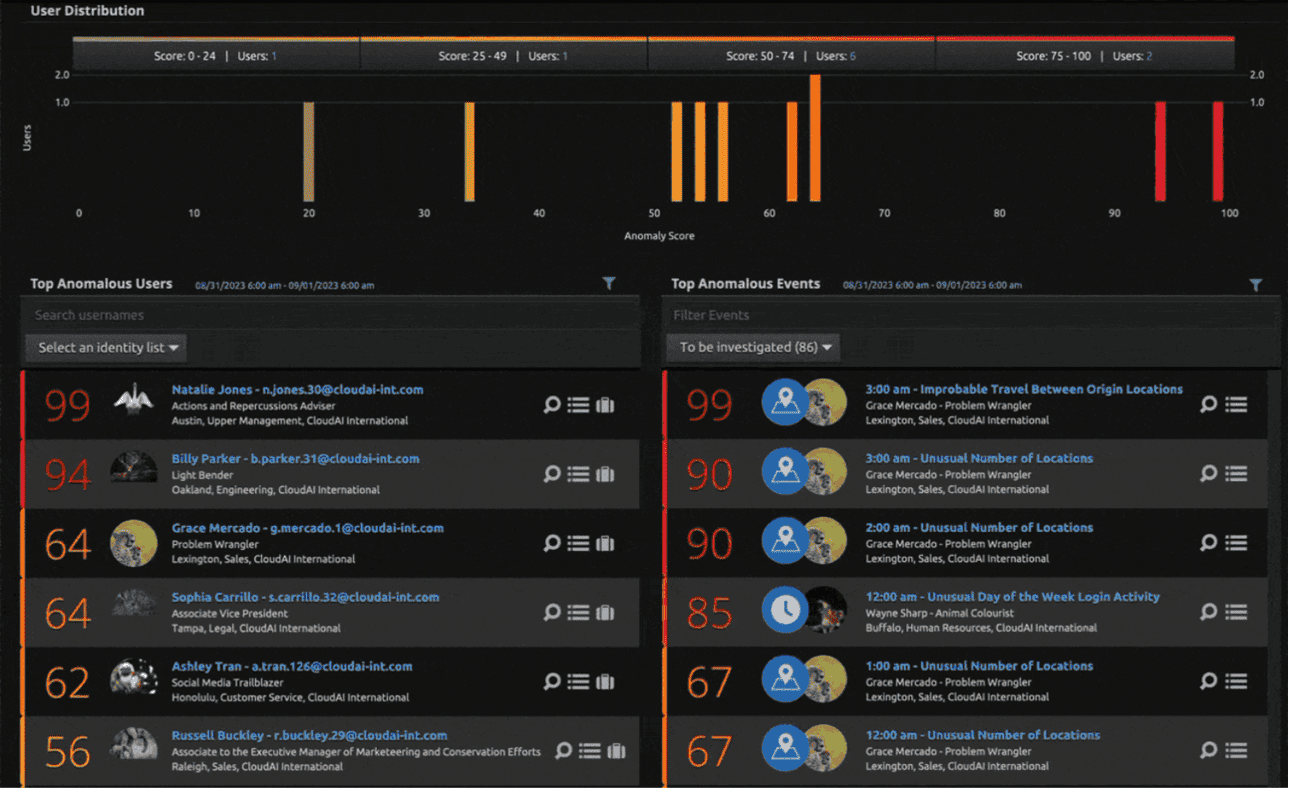
You can then drill down to show detailed views on the user, giving you more information on when it has shown signs of abnormalities and malicious intent.
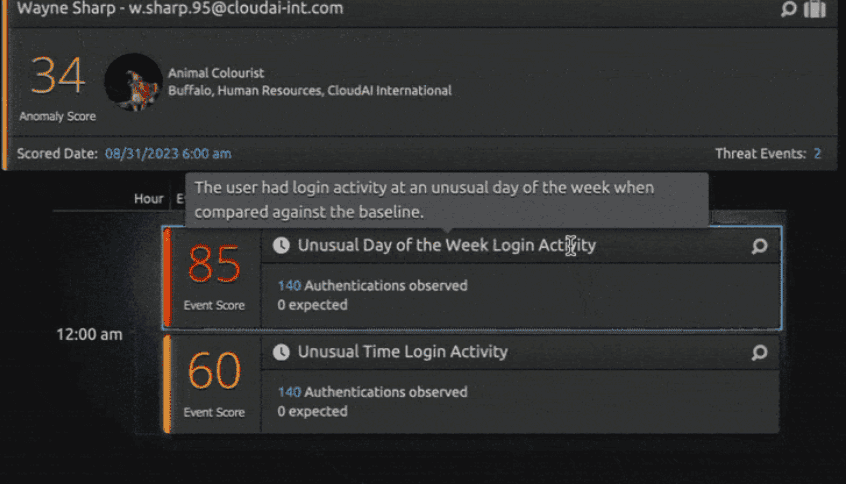
In conclusion, attacks against governmental agencies will not lessen with time, demanding a proactive and multifaceted approach to cybersecurity. Governmental agencies must leverage advanced technologies to prevent data exfiltration attempts. LogRhythm is a ready to be a partner in making security easy for you. To learn more on how we can help equip your agency with deep visibility and rapid threat detection and response capabilities, arrange a consultation with us today.
