The Problem: How Do You Monitor Vendors That are Monitoring Your SCADA Environment?
Utility companies have scores of sensors that detect leaks in pipelines and monitor the integrity of systems inside their Supervisory Control and Data Acquisition (SCADA) environment. Many times, these sensors are monitored by third-party vendors to provide reporting and alerts when things start to go south.
However, these third-party vendor access points can double as additional entry points for intruders. Your analysts in the security operations center (SOC) need to monitor the people doing the monitoring. The LogRhythm NextGen SIEM Platform provides visibility into how vendors are accessing your data and allows for effective investigation into the use of insecure protocols — helping you achieve a more comprehensive view of your threat landscape and drive better security policies in your environment.
Policy Verification for a SCADA-Centered SOC
Let’s walk through one of my favorite proof-of-concept (POC) exercises for a SCADA-centered SOC. This POC highlights a level of visibility into the prospective customer’s network that the customer hadn’t previously known was possible. Once the firewall data comes into the POC, one of the first layers of visibility we like to provide for those in the United States is showing “Direction=Outbound” “Classification=Allow” to reveal that “Country Impacted” is not the U.S.
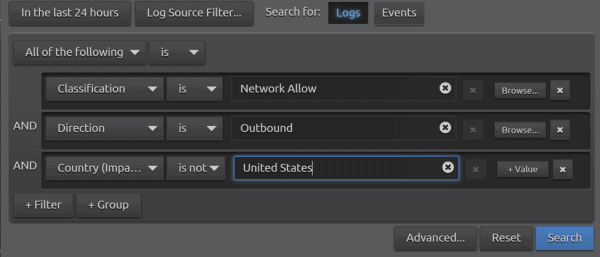 Figure 1: Country Impacted
Figure 1: Country Impacted
Typically, we often hear something along the lines of: “Oh we have a geo block, so none of that will be allowed anyway.” What we show them next is where the surprise comes in:
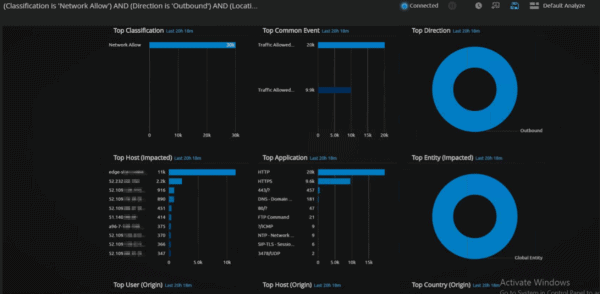
Figure 2: Dashboard Full of International Activity
Much of this activity is likely legitimate traffic and, even more likely, advertisements in web traffic. But when we start looking at Top Application in this dashboard, we see something interesting: File Transfer Protocol (FTP) Command.
Naturally, a logical question might be: “Do you expect FTP traffic to be coming or going into your environment from another country?” We’re not sure there has ever been a “yes” to this question. Perhaps a better question would be: “Are you still heavily reliant on FTP?”
Let’s put it this way, when FTP was first released, the price of gas in America was just 40 cents and the average new house cost $25,000. To say it’s an antiquated protocol is putting it lightly.
Now let’s take a look at that FTP traffic:
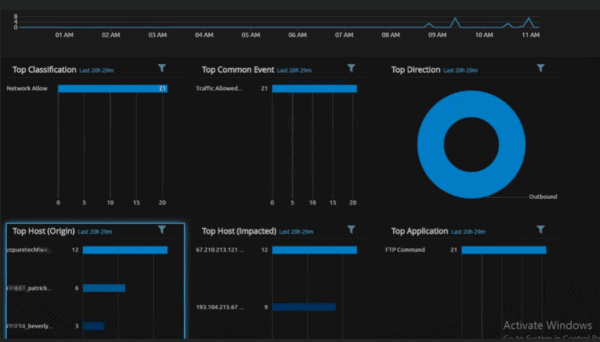 Figure 3: Drilldown of FTP Traffic
Figure 3: Drilldown of FTP Traffic
With a simple double click of FTP Command, we are now filtering in only FTP traffic, and we can quickly see where the traffic is coming from and going to.
Drilling down into the first Host Origin, we see it’s coming from the prospect’s pipeline operators. The operators of this monitoring services company checks the structural conditions of their assets in near real time. In speaking with the network admin, the prospect verified this is a firewall at one of the reservoirs where the organization is doing some seismic testing on the dams and pipelines. The location where the data is impacted is Calgary — where the monitoring services company is located.
After a chat with the key stakeholders on this monitoring solution project, all parties involved agreed that it was probably in their best interest to not have pivotal water infrastructure integrity data leaving the country via an insecure protocol where authentication is done in cleartext.
We quickly formed a case to organize the logs for reporting and follow-up purposes.
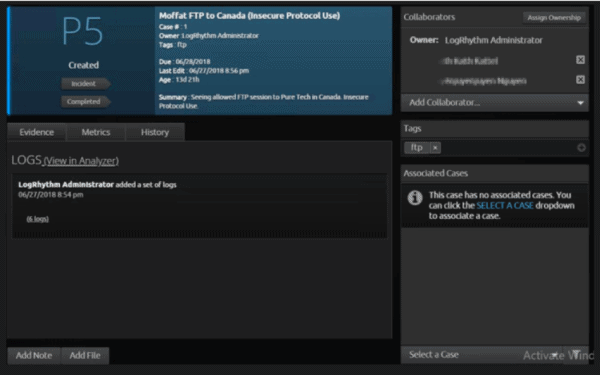 Figure 4: Case Buildout
Figure 4: Case Buildout
But wait, what about Patrick and Beverly up top in the “Top Host: Origin” tab? They’re also sending data out of the U.S.
Drilling down into the prospect’s results, we can see that they’re both headed to the same place: Ireland.
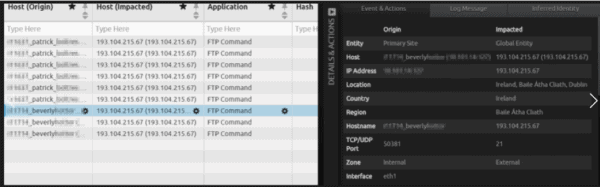 Figure 5: Origin Country Drilldown
Figure 5: Origin Country Drilldown
With a little digging, we were able to find that this IP is an Adobe FTP server that is used to update legacy versions of Acrobat. The Senior Windows Administrators prudently agreed that this wasn’t a good system to have in place.
The Value of Monitoring FTP Transfers within SCADA Environments
Within day one of introducing Check Point Firewall logs, we provided visibility into the prospect’s network that the company hadn’t had access to through years of owning another SIEM and paying recurring professional services costs. A simple query not only provided incredible insight into data leaving the company’s environment, but also provided the network administrators with data to help better understand its own firewall policies.
Is it time to switch your SIEM? Learn more about how our LogRhythm helps security operations teams transition to a smarter solution.
