Cybercriminals can compromise systems in just a matter of minutes. However, it could take weeks or even months to detect a possible threat. To reduce your mean time to detect (MTTD) and your mean time to respond (MTTR) to cyberthreats, you need to find a solution to automate your threat hunting capabilities.
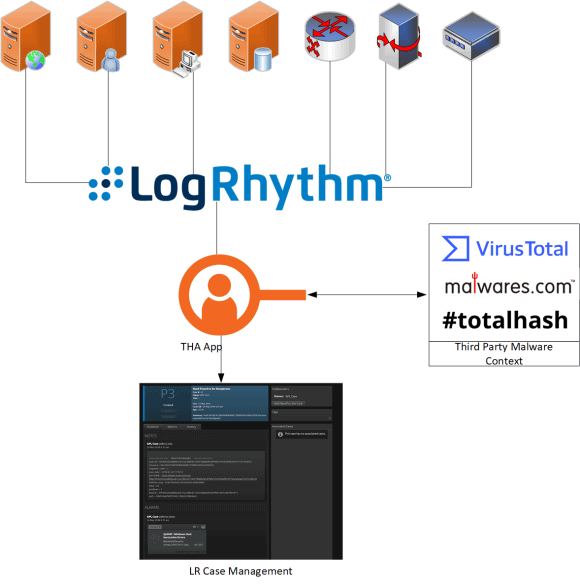
LogRhythm’s SmartResponse™ plug-in platform, combined with our Machine Data Intelligence (MDI) Fabric and Phishing Intelligence Engine (PIE), helps streamline and automate the threat hunting process. This is called the LogRhythm Threat Hunting Automation (THA) app. In addition to automation, LogRhythm’s THA solutions help you connect in real time with threat intelligence sources, validate hashes, IPs, domains, hostnames, and URLs, and help analysts with case automation and evidence collection.
Let’s take a closer look at the importance of threat hunting.
The Power of Threat Hunting
Threat hunting refers to manual and machine-assisted methods of proactively searching through networks and large datasets of information (e.g., threat intelligence lists) to find threats that evade existing defenses, such as antivirus systems, intrusion detection systems, intrusion prevention systems, firewalls, and more.
When it comes to threat hunting, you need dedicated analysts to stay focused on the task at hand. Threat hunting requires specific analytic skills, such as familiarity with your organization and its internal processes, as well as the ability to investigate possible incidents. To maximize your threat hunting experience, your analysts should use automation to accelerate these hunts to make them easier and more accurate.
LogRhythm’s THA App
Now, let’s review how LogRhythm handles threat automation.
The THA App is a series of functions and scripts that automates passing collected potential indicators (e.g. hashes, IPs, domains, hostnames, or URs) from a configured threat intelligence provider to available web-based API malware analysis databases such as VirusTotal and Open Threat Exchange.
The app also allows you to:
- Display the results on the screen
- Create a case and add the output of the provider to the case
- Add the alarm as evidence into the case
- Automate the investigation reading from Elasticsearch using and creating alarms, if needed
The Threat Hunting Automation App in Action
Figure 1: LogRhythm’s Threat Hunting Automation app streamlines and automates threat hunting
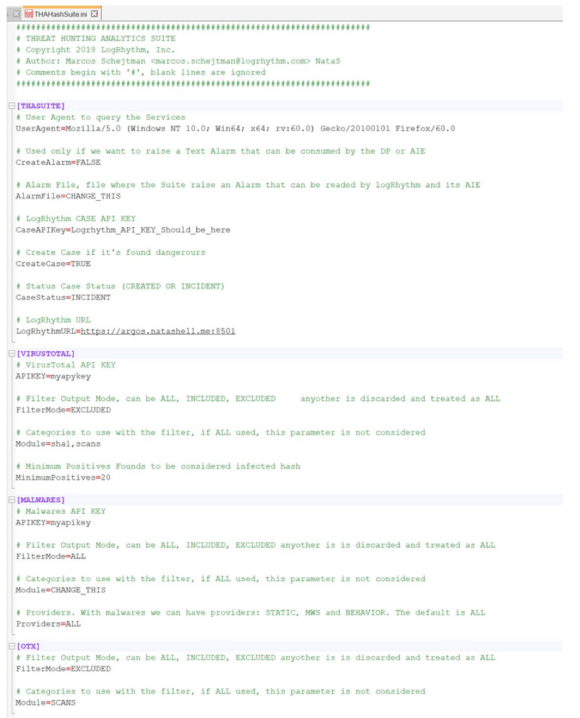
Figure 2: Manage plug-ins with LogRhythm’s THA app
The output of the providers can be extensive (e.g., more that 50 AV scans). By using excludes or includes filters for the output, you can specify what you need.
If the parameter “CreateCase” is true, a case will be raised if the provider specified has marked this as dangerous in the indicator status.
The parameter CreateAlarm will integrate with Kafka and it will raise an alarm whenever a malicious indicator surfaces. In this version, you must put in cleartext (or unencrypted data) in your API keys.
In the next step, the app will request the specified indicator of compromise (IOC) and print the output. You can run the plug-in from the command line, as well:
Figure 3: You can add specific details and run the app from the command line
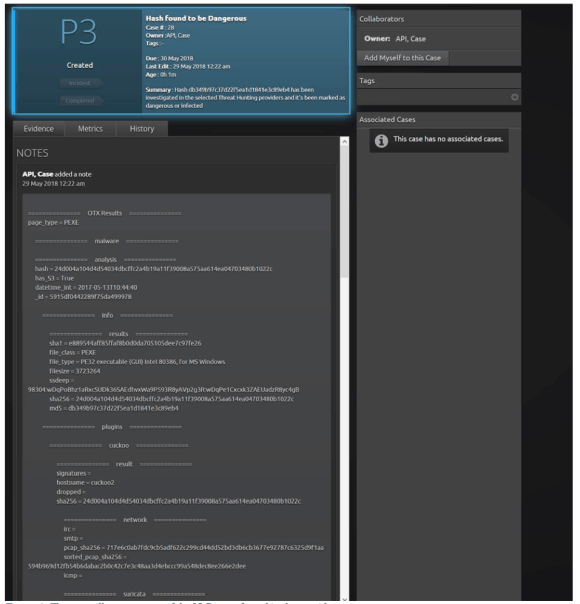
Figure 4: The app will create a case if the IOC is confirmed in the provider request

Figure 5: The app adds the evidence found as notes on the provider’s request
You can use the THA app as an SRP to accelerate your investigations as well:
Figure 6: The THA provides multiple Smart Response plug-ins to automate the hunting process
Figure 7: The dashboard shows how an alarm alerts an anomaly
c. You investigate the issue and detect you’re having communication with an IP marked as a threat in the attack list from the SysAdmin, Audit, Network, and Security (SANS):

Figure 8: Investigate the issue to determine if you have a true threat
d. Use the THA app to create a case if the investigation determines the need. For this case, you’ll search in the VirusTotal database.
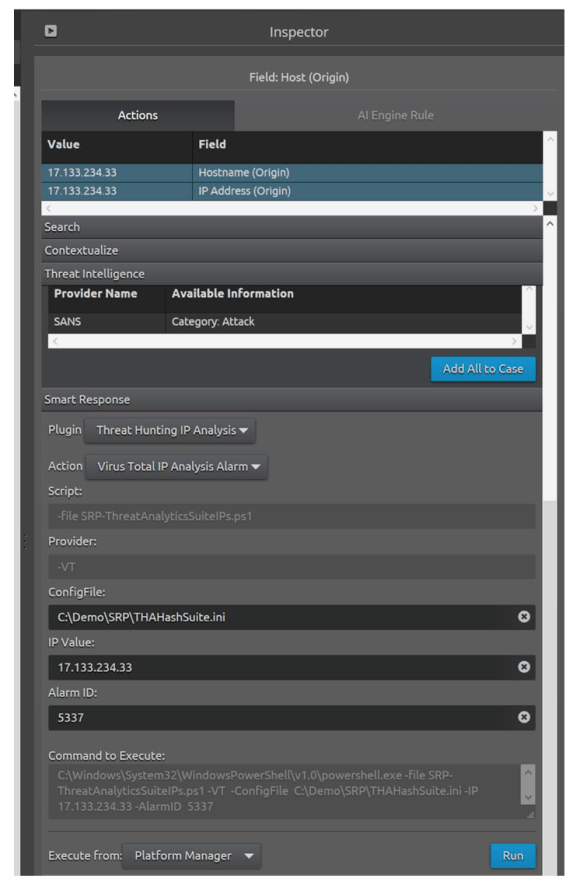
Figure 9: Investigate and create a case, if needed, with the THA app
e. You receive information that the threat is a false positive, so the app doesn’t create a case, and the alarm might be closed. You can also add it to an alarm to accelerate the investigation, automate the case creation, or close the alarm, if needed.

Figure 10: If your threat is a false positive, the app won’t create a case
As you can see from the above example, the THA app looks for real-time information. However, open-source lists can sometimes have outdated or noisy data that can utilize false positives or alarm fatigue. A THA app also automates case creation and collaboration, adding relevant evidence for your analysts.
What distinguishes the THA app from threat search or other browser plug-ins? The seamless integration with the LogRhythm ecosystem offers the ability to gather information and automate the case creation whenever necessary.
Automating Threat Hunting with LogRhythm
At LogRhythm, we make threat hunting automation possible and easy. LogRhythm not only incorporates threat lifecycle management into its platform, but its solution is also ready to integrate with anything you need for machine-assisted detection and investigation. LogRhythm MDI Fabric gathers the metadata needed for research and helps accelerate the results of your investigations, providing not only meaningful context, but also the ability to abstract the concepts for integration purposes.
Through powerful APIs, LogRhythm enables complete control of the automation lifecycle. You can benefit by integrating the LogRhythm solution seamlessly with your current process and improve your threat hunting capabilities. Automation spares your analysts from the tedious task of manually querying vast amounts of data to validate what’s useful or not. LogRhythm lets you take this concept and evolve it into a full threat hunting process.
The THA app described above is another example of how LogRhythm capabilities can improve the detection and remediation cycle.