Windows account lockout policies are an effective and recommended best practise for securing against brute force attacks. When these activities occurs within the perimeter of an Enterprise’s network, LogRhythm’s SIEM makes it a simple task to quickly work out the source of account lockouts; however, one of the many challenges Enterprises encounter today is tracing the source of repeated account lockouts which, while often are not malicious in nature, can be tricky to track down if the offending device is outside the internal network perimeter, such as BYOD.
One variant on this use case customers’ have is identifying the source device, or devices, that are causing account lockout when using Microsoft Exchange’s Outlook Anywhere for remote workers’ devices, such as their iPhones, Android, Blackberry, Windows Mobile (I know, I know, but some people do use Windows Mobile!) etc….
There are times though when a single log message on its own can give no more, it draws a blank. So, there you are, a user’s account has been locked out for the umpteenth time and you’re manually trawling through Windows Security Event Logs, or even using the Microsoft Account Lockout Status tool, but if the source device causing account lockouts is external, all you’ll see in the logs is the reverse proxy device the connection is coming through. Let’s look at an example, specifically here we can see one of our contractor’s accounts has locked out, again. Galactically annoying as he can’t carry out his mission until we can work out what’s causing the lock out. Now the key bit of meta data from this Log is the source device—a Microsoft TMG proxy device—if this account was sourced by an internal workstation we’d see the internal workstation or laptop name; however, in this case we’ve established this user must be connecting in via BYOD devices from an external source, via our TMG proxy. And this is the challenge—we’ve hit a dead end as to which source device is causing the account lockout. Or have we?
Chris_Martin_1
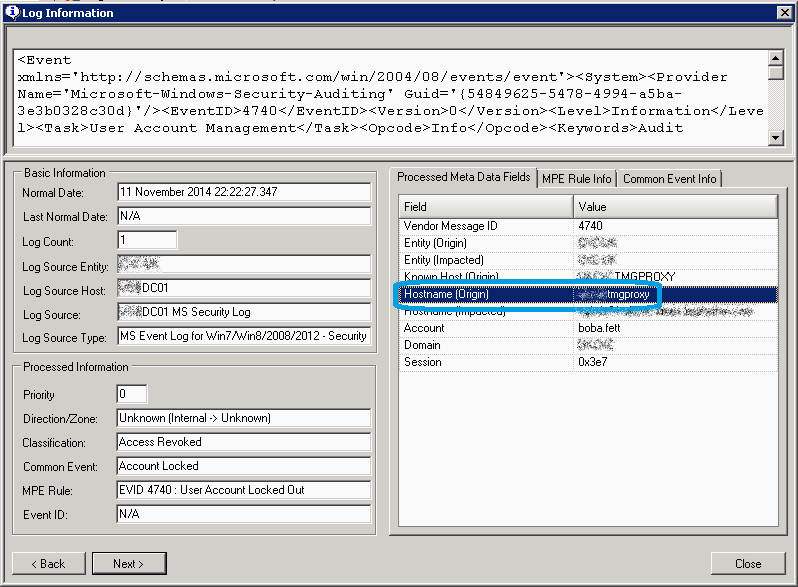
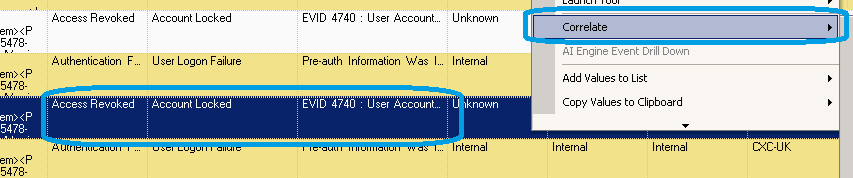
Fortunately that’s where the advantage of structured data, and collecting from one of the several hundred devices we support out of the box, comes in. Using the LogRhythm SIEM we can quickly find all the Account lock out Events and perform a correlate drill down on the User account in question, this’ll return all activity for the immediate time range across all log sources for that user.
Chris_Martin_2
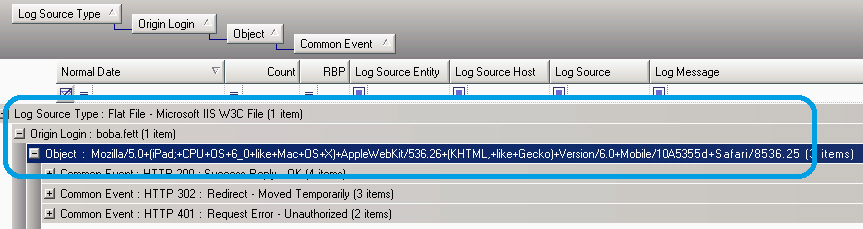
Now, if you’re happening to be collecting your Exchange Server OWA logs (the IIS logs to be exact), this will provide us an immediate answer to the question of what that hidden BYOD was. This is possible as Exchange logs include the User Agent string in its log message as well as the source username. The User Agent is a unique identifier that can be used to differentiate when users have multiple devices such as their phone, their tablet, their laptop, their home PC, and so on, authenticating into your enterprise.
Looking at these results, we can quickly pivot the results to concisely see Boba Fett is using an iPad—the bounty hunters tablet of choice! (Not sure how he works it through those gloves though.)
So what was often a challenge for companies can be solved in seconds by using the LogRhythm SIEM. Our inbuilt role-based access control makes it simple to save these investigations or dashboards and provide delegated access to support roles in order to reduce the time in finding the source of repeated account lockouts and reduce the downtime to internal users when such issues occur.
May the SIEM be with you!