The Challenge: Protecting Customers’ Personally Identifiable Information (PII)
Businesses today have to ensure that they not only meet their regulatory compliance requirements, but also take reasonable and appropriate measures to protect their customers’ data (including their personally identifiable information).
The consequences of a cyber breach include reputation damage and financial penalties. The recently passed European Union (EU) General Data Protection Regulation (GDPR), which levies potential fines as high as four percent of the worldwide total revenue of the business for the preceding year, is a high-profile example.
U.S.-based companies that collect EU citizens’ PII and operate within the EU also need to carefully review this regulation. Commentary on how this could affect U.S. organizations can be found here.
Often, the key indicators of compromised PII aren’t available in traditional log or audit data. So just how can organizations actively monitor for potentially exposed or leaked PII?
In this example, I’ll cover how the Deep Packet Analytics feature in LogRhythm’s NetMon can do just this—detecting and alerting on exposed or leaked PII by looking at network traffic.
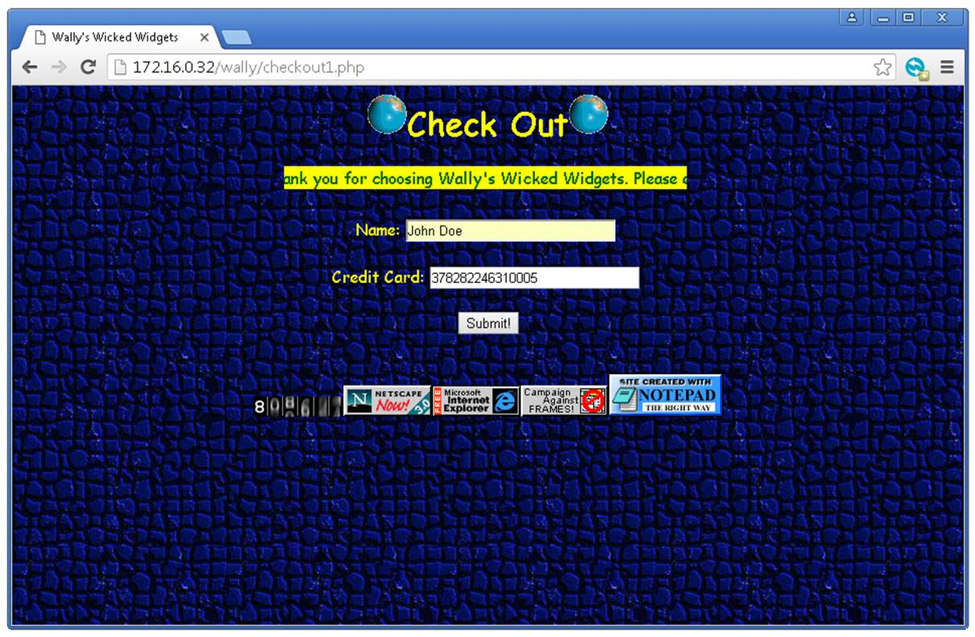
Imagine Chuck, an outsourced developer, has been hired to update Wally’s Wicked Widgets’ checkout payment gateway. Chuck is a seasoned developer, starting his blossoming career in the ‘90s as one of the pioneering developers of Geocities. Here’s the proposed updates he has made to Wally’s Wicked Widgets for review. Wally, the CEO, loves the new updates, and the site has been made publicly available.
Click images to enlarge
Unfortunately, Chuck hasn’t really kept up with security best practices. While the new payment gateway page looks great (it’s even got one of those new page counters on it), there are several gaping security holes.
One such security issue is that the site has been published using HTTP instead of HTTPS, so all of Wally’s customers’ data will be transmitted over the internet in clear text. This is something like sending your credit card details on the back of a postcard—anyone can read them.
If this security issue isn’t detected and fixed, some embarrassing PR (and potentially fines) could be the result.
The Solution: Detecting Transmitted PII with NetMon
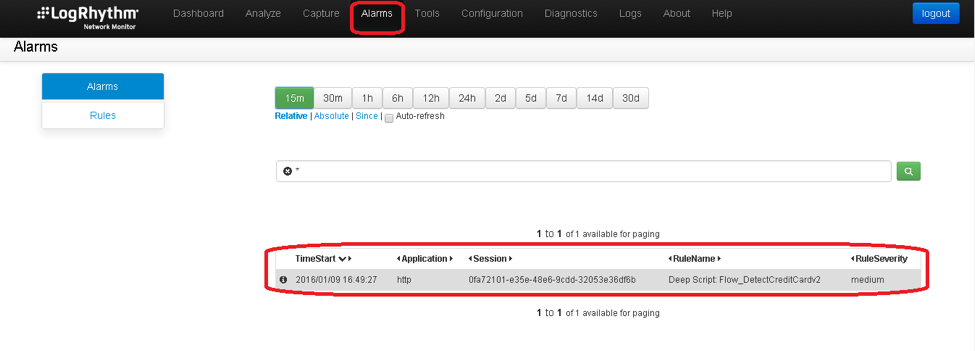
In scenarios like this one, collecting log and audit data from servers and endpoints may not leave a trace of exposed PII. Exposed PII can only be found by examining network traffic in transit. Fortunately, LogRhythm’s NetMon includes default rules that will detect and alert PII being transmitted in clear text over the network.
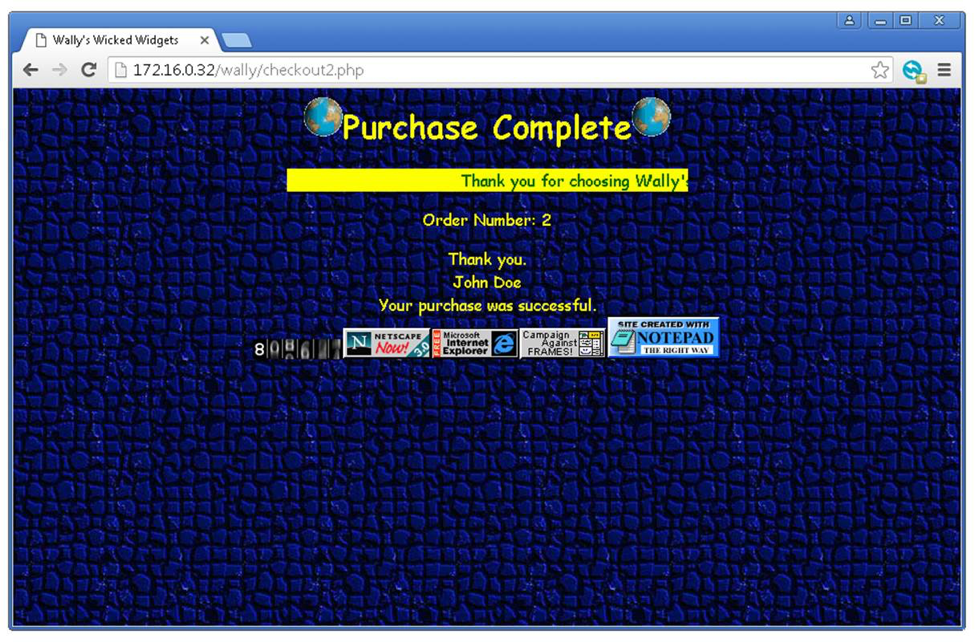
In the above image, you can see that an alarm was raised as John Doe’s credit card details were seen transmitting the network in clear text (his Amex card to be exact).
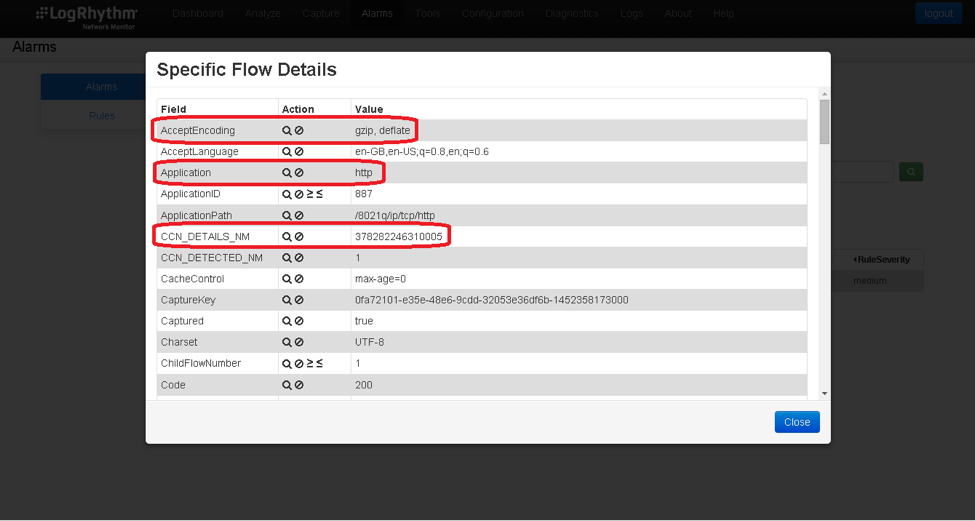
However, there is more going on under the bonnet within NetMon. The credit card details were actually compressed and not in clear text. Rather, they were GZIP’d. This is a common mechanism used by web servers all over the internet to save on bandwidth and make web browsing quicker. Fortunately, NetMon’s Deep Packet Analytics (DPA) can inspect GZIP’d data, so this exposure of PII was still picked up.
But NetMon’s DPA doesn’t just pick up AMEX cards. There’s a variety of major credit cards such as Visa, Master Card, Diners Club, Discover, JCB, and so forth.
The Value: Detecting PII Exposure That Would Be Otherwise Missed
By monitoring network traffic, PII exposures that could be otherwise missed can be picked up immediately by LogRhythm’s DPA. However, It’s not only credit card data. Following are some example rules in which DPA can pick up other forms of PII, such as social security numbers or clear text passwords.
With regulations and governance stipulating, business must take reasonable measures to ensure customer data is protected. A blind spot to detecting PII is something no organization can risk (or afford!) ignoring.
To get started, try NetMon Freemium today.
Sample Deep Packet Analytics Rules
More rules are being released all the time, but below are some example rules:
| Rule Name | Description |
|---|---|
| flow_proto_mismatch_53 | Detects protocols using port 53 that are not DNS. This might be a protocol violation. |
| flow_smtp_sender_domain_mismatch | Detects SMTP traffic where sender email domain does not match actual domain. |
| Flow_DetectClearTextPasswords | Detects clear text passwords over http |
| Flow_DetectCreditCard | Detects Credit Card information that is sent as plain text over HTTP. |
| Flow_DetectLargePost | Flow_DetectLargePost detects potential data exfiltration. Should be run with Packet_DetectLargePost. |
| Flow_DetectSSN | Detects potential Social Security numbers being sent as plain text over http. |
| Flow_PrivateKeyExtensions | Detects files that contain private-key file extensions. |
| Flow_ProtocolMismatchFTP | Detects FTP traffic occurring on ports other than 20 and 21. |
| Flow_ProtocolMismatchPort20Port21 | Detects traffic on ports 20 or 21 that is not FTP. |
| Flow_ProtocolMismatchPort22 | Traffic on port 22 that is not SSH. |
| Flow_ProtocolMismatchPort53 | Detects traffic on port 53 that is not DNS (or KRB5). |
| Flow_ProtocolMismatchPort80 | Detects http traffic not on port 80. |
| Flow_ProtocolMismatchSSH | Detects ssh traffic not on port 22. |
| Flow_SMTPDomainMismatch | Detects SMTP traffic where sender email domain does not match actual domain. |
| Packet_DetectLargePost | Packet_DetectLargePost detects potential data exfiltration. Should be run with Flow_DetectLargePost. |