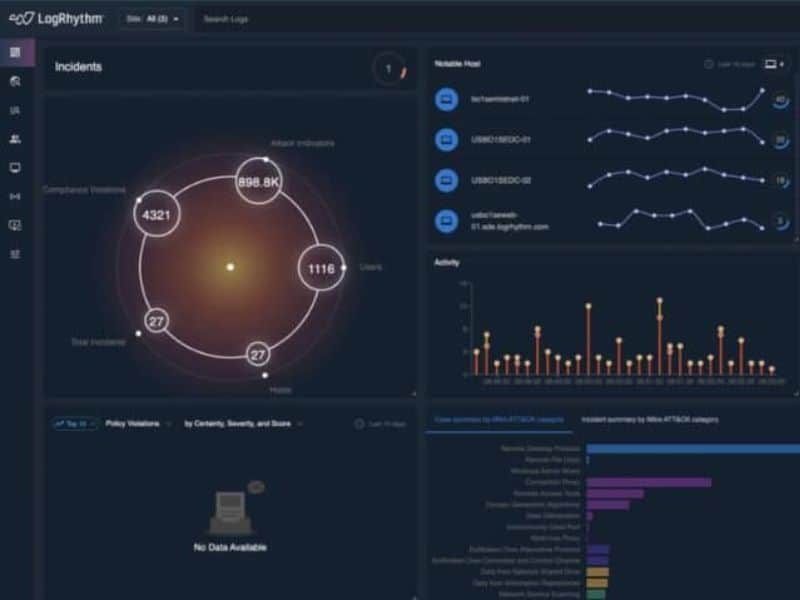
Network traffic tells a detailed story about what’s happening in your infrastructure every day. But information overload and visibility gaps often make it difficult for security teams to spot malicious activity before it’s too late.
LogRhythm provides comprehensive on-premises and cloud network traffic visibility and uses advanced analytical techniques to detect threats quickly and provide the high-fidelity insights your team needs to respond effectively.
How Effective Network Analytics Helps Your Business
Eliminate Visibility Gaps
Enhance your visibility by analyzing all activity, even when agents or logs are not present.
Detect Sophisticated Attacks
Cut through all of the noise and zero in on the security threats that matter the most.
Optimize Incident Response
Engage responders quickly and empower them with detailed and actionable insights.
Why LogRhythm Is Your Ideal Network Analytics Partner
LogRhythm’s network detection and response (NDR) solution brings a highly differentiated set of capabilities together to enhance your security monitoring and threat hunting efforts.
Comprehensive Visibility
Collect detailed traffic information from both on-premises networks and cloud providers, overcome complexities like traffic encryption, and ensure monitoring coverage for both north-south and east-west traffic.
Multiple Analysis Techniques
Combine deterministic detection methods with machine learning to achieve immediate results, detect novel threats, and spot indicators of compromise like malware activity, lateral movement, and data exfiltration attempts.
Efficient and Scalable Architecture
Minimize data movement costs, improve resilience and scalability, and simplify data privacy compliance by co-locating analytic processing alongside local data collection points through a distributed mesh architecture.
High-Fidelity Visualizations
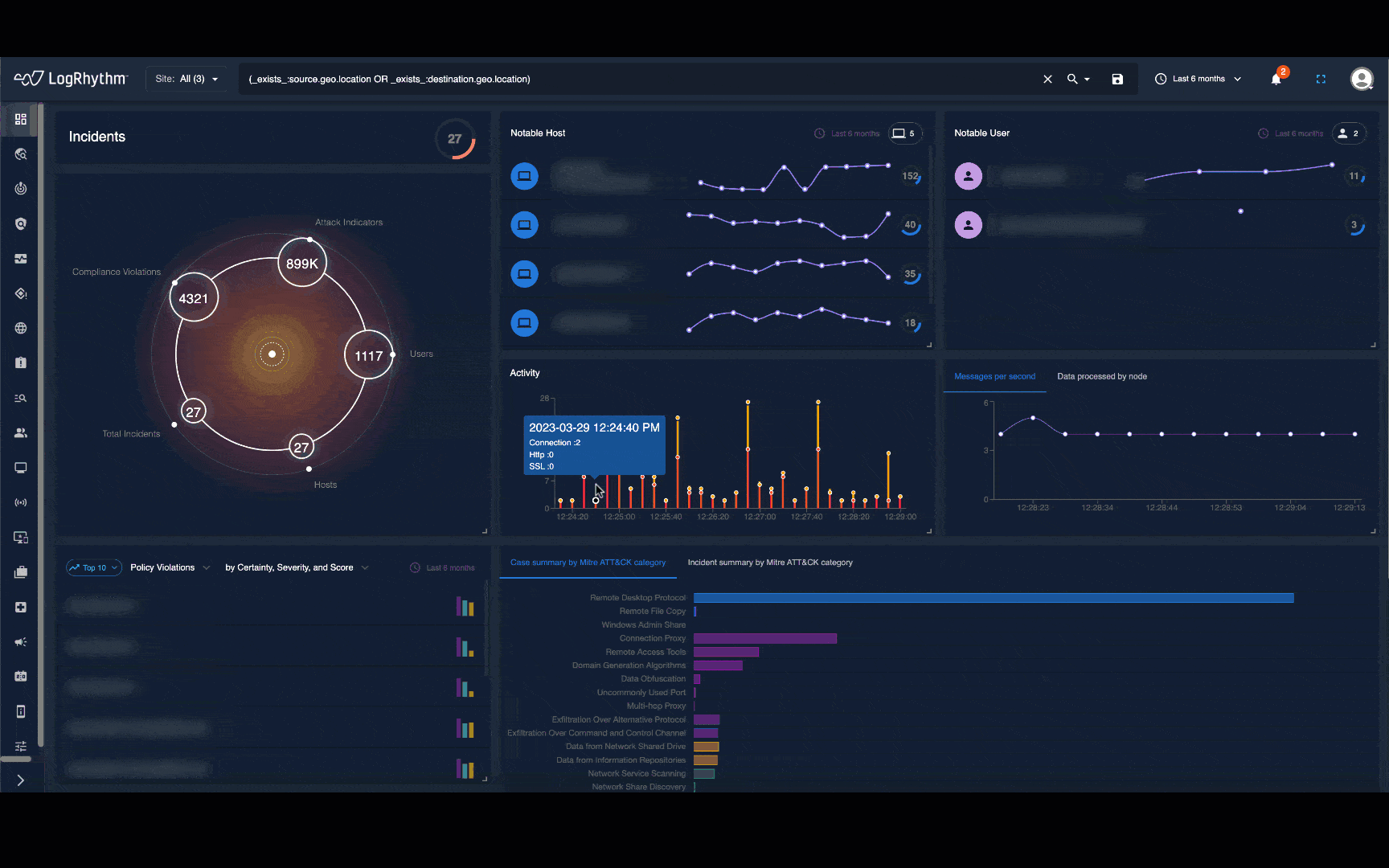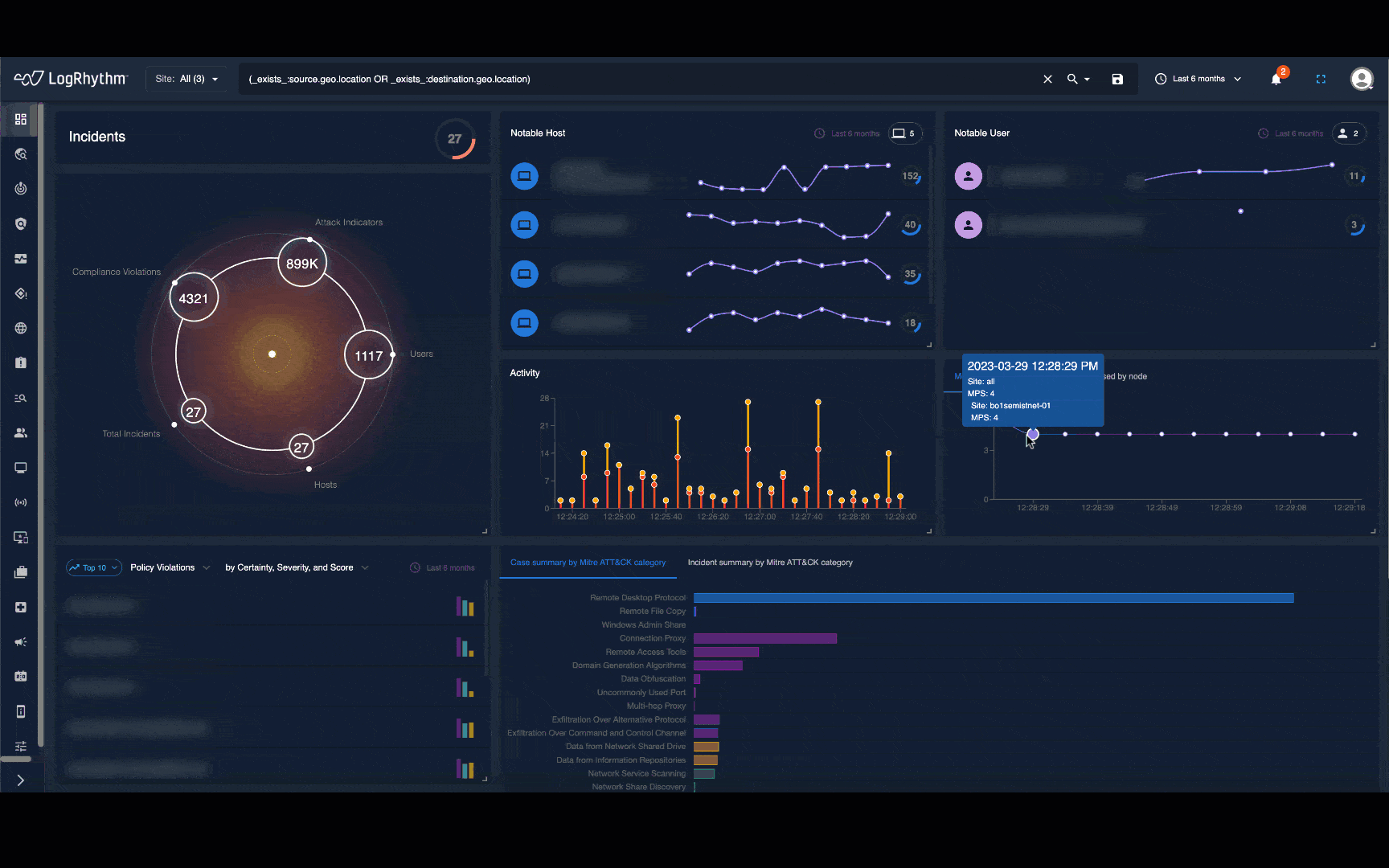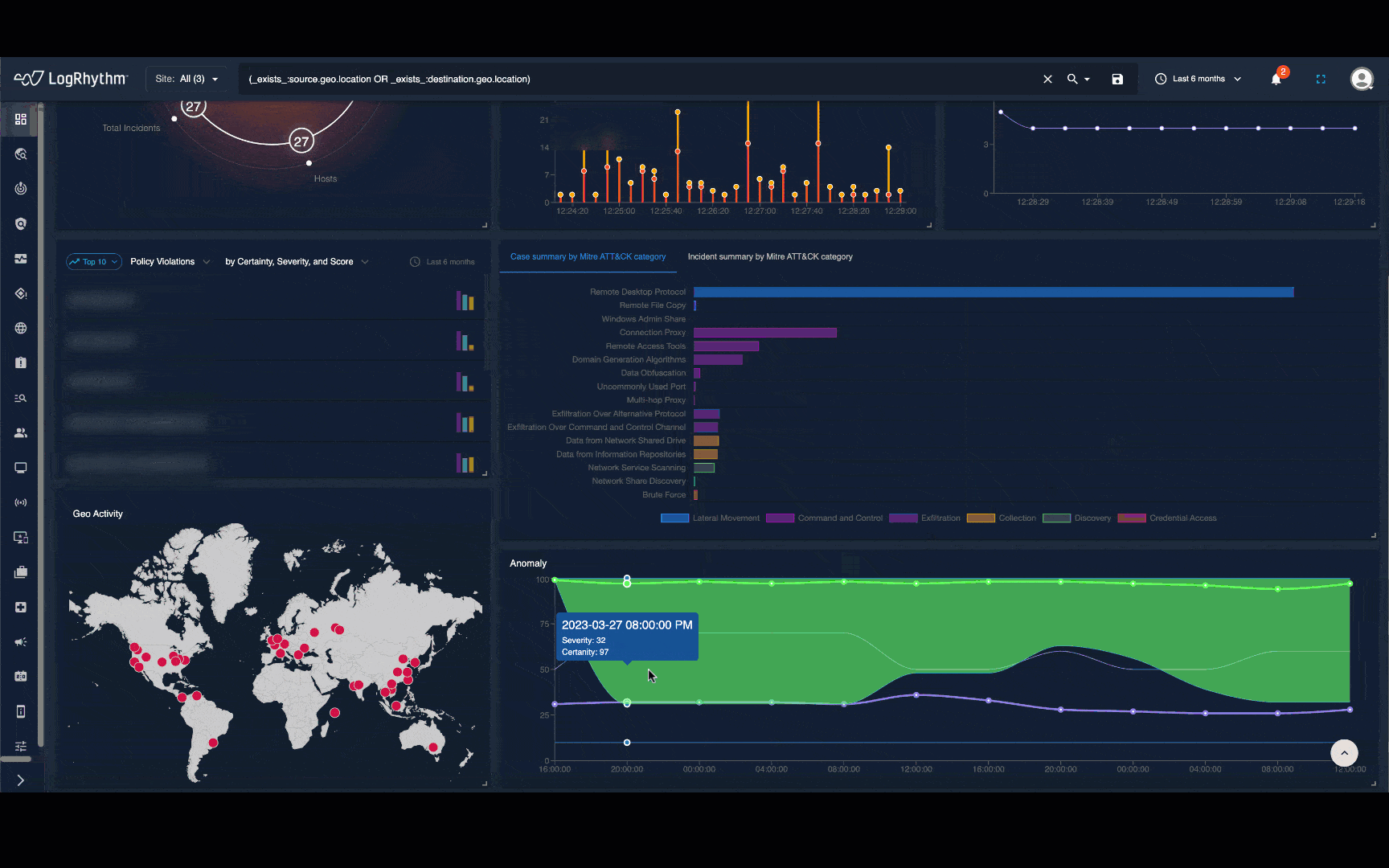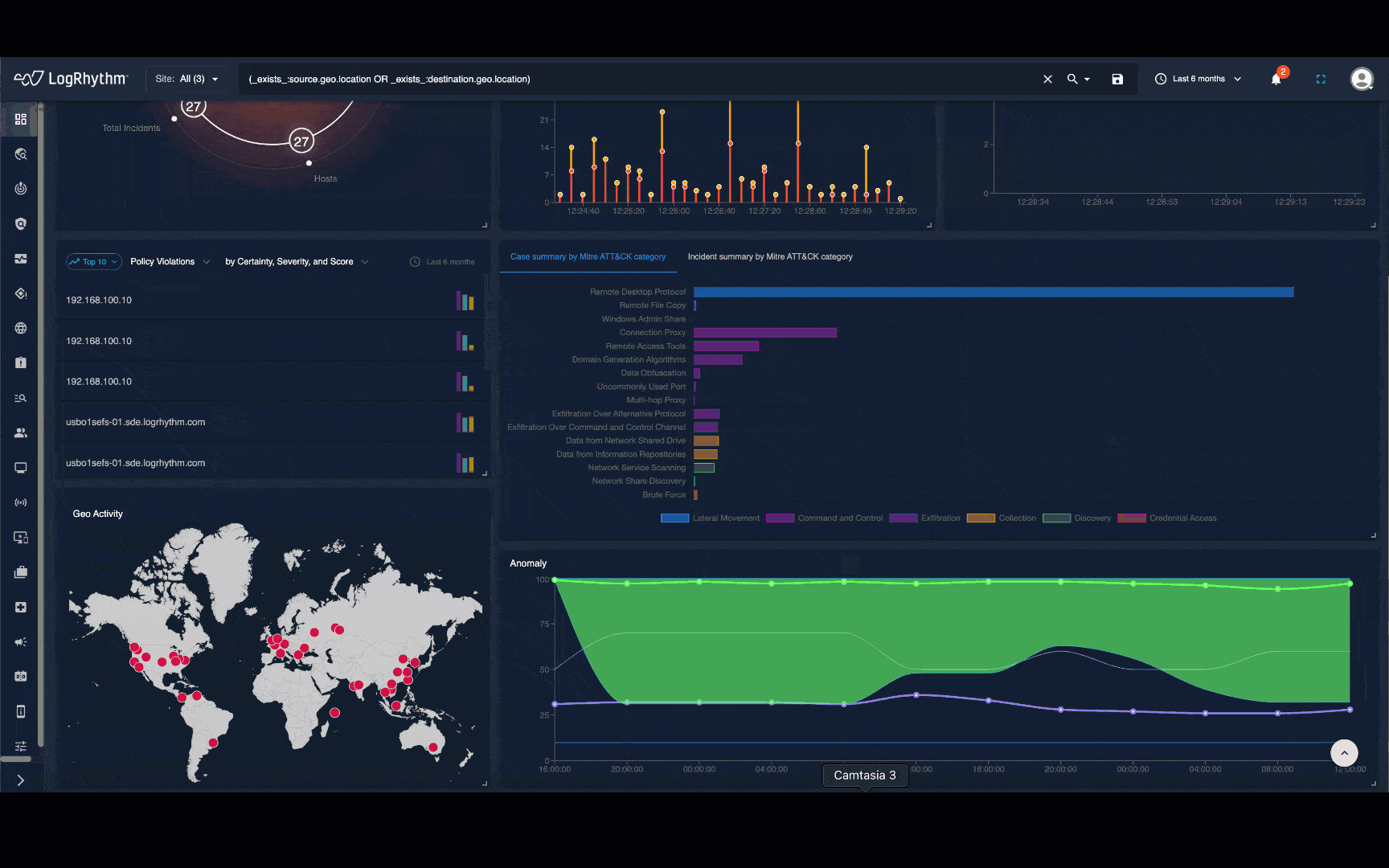
Arm security analysts and threat hunters with real-time and historical visualizations that present activity as a human-readable narrative, map to proven frameworks like MITRE ATT&CK®, and overlay detailed recommendations.
Single Pane of Glass
Leverage plug and play integrations with SIEM, EDR, firewalls, and other security solutions that simplifies deployment, delivers broader threat detection, and provides one viewpoint across your entire environment.
Embedded Expertise
Get over 20,000 out-of-the box detection rules for immediate protection against known threats and rule customization and meet specific industry or security compliance needs.
LogRhythm's Network Analytics Product
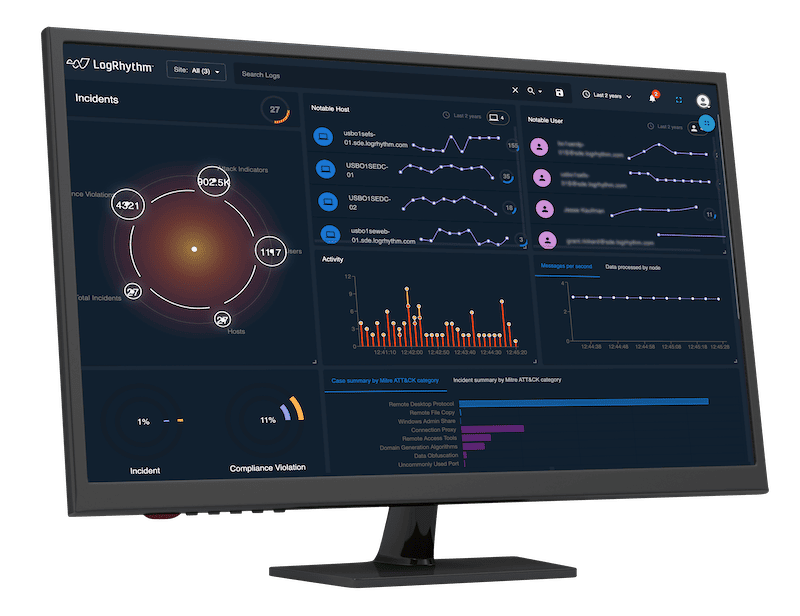
LogRhythm NDR: 360-Degree Visibility that Protects Your Network
LogRhythm NDR helps security teams detect and respond to sophisticated cybersecurity attacks by applying advanced analytics to your on-premises and cloud network traffic. Through a powerful combination of machine learning and deterministic techniques, LogRhythm NDR detects security threats that would otherwise be missed and gives responders and threat hunters high-fidelity visualizations and step-by-step recommendations.
Recommended Network Analytics Resources
Get Started with Network Analytics
Network analytics play a critical role in an effective security strategy. Schedule a personalized demo to see how LogRhythm can help your team use network traffic insights to strengthen your security posture.