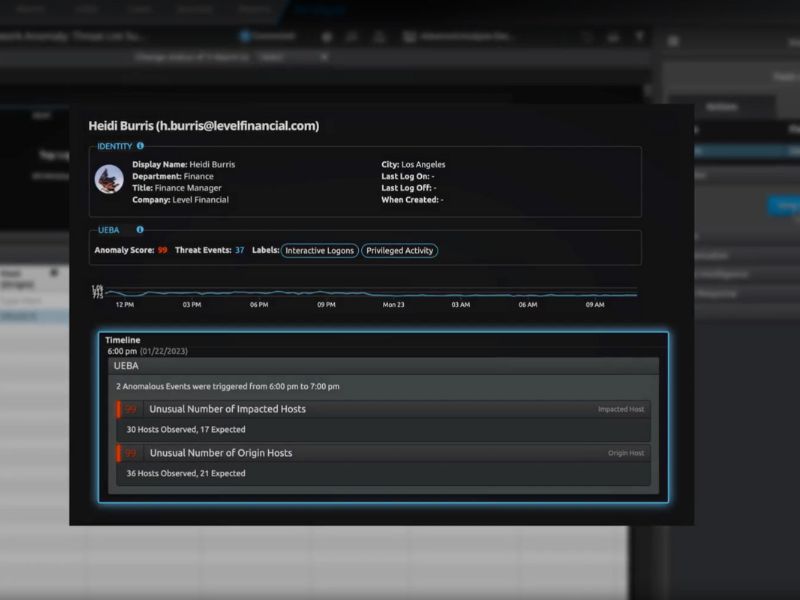
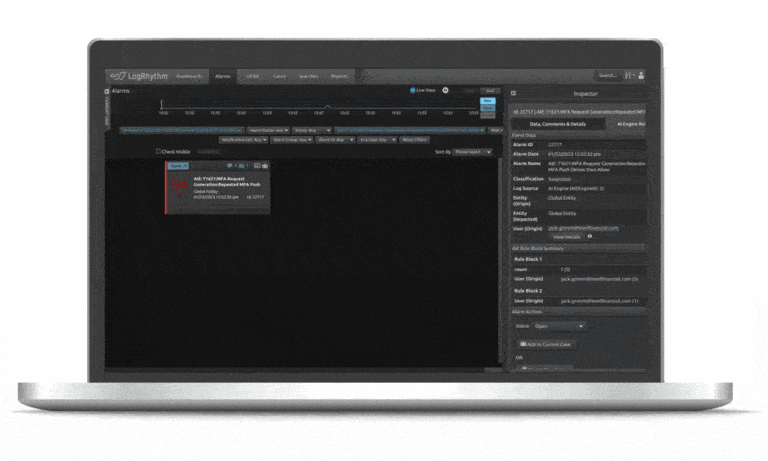
You are facing a constant barrage of threats — some of which you do not even know exist. The reality is that your users are behind many threats and breaches, whether they are malicious or accidental. As the typical point of entry for an attack, users are a difficult vector to monitor and secure.
To confront the tidal wave of attacks, an advanced user analytics solution can help you better detect and respond to user-based attacks. If you’re interested in learning how LogRhythm can help you reduce insider risk, watch our phishing attack demo!
Benefits of User Analytics Solutions
Monitor User Activity
Eliminate visibility gaps and see the full picture of what is happening across your users, data, and systems.
Enhance Security Monitoring
Know what activity is normal versus malicious by analyzing data through contextualization and enrichment.
Detect Attacks Earlier
Use machine learning to track user behavior and detect anomalies before potential threats escalate.
What to Look for in a UEBA Solution
To ensure you get the most out of a user analytics solution, here are capabilities to look for.
Data Normalization
Leverage a consistent and predictable dataset to perform accurate analytics.
Holistic Analytics
With deterministic analytics and anomaly analytics, you can detect complex user-based attacks across a variety of tactics.
Baseline User Behavior
Machine learning identifies user-based individual, group, and peer group anomalies that deviate from normal behavior.
Seamless Integration
Easily integrate with other security tools to further qualify, investigate, neutralize, and respond to a threat.
LogRhythm’s User and Entity Behavior Analytics Solution
Discover how LogRhythm can empower you to reduce risk against user-based cyberthreats.
LogRhythm UEBA
LogRhythm UEBA adds extra layers of security monitoring to organizations to help protect against potential threats and prioritize findings for investigation and response. LogRhythm UEBA detects known and unknown threats via scenario analytics and machine learning to quickly surface and prioritize critical events and accelerate detection. The cloud-native add-on solution seamlessly integrates with LogRhythm SIEM and self-evolves through machine learning.

Recommended User Analytics Resources
Get Started with User and Entity Behavior Analytics
To uncover threats to which you were previously blind, LogRhythm’s deterministic and anomaly detection analytics provide essential visibility into your users and their activity, giving you the tools to protect your organization and reduce risk.
Speak with one of our security experts to get a first-hand look at how LogRhythm can address your specific use cases.