The “Security Spotlight” blog series provides insight into emerging cyberthreats and shares tips for how you can leverage LogRhythm’s security tools, services, and out-of-the-box content to defend against attacks.
In this Security Spotlight, we’ll be talking about how adversaries may use native windows commands to assist in account discovery (MITRE ATT&CK® Technique T1087.001).
What Native Window Commands Are Used In Account Discovery?
Upon initially gaining control of a victim’s machine, the next step of an attacker’s plan often involves seeking ways to expand their control to other areas of the victim’s network with different privileges and levels of access. A common starting point for this type of activity is attempting to understand the local system account structure to aid in follow-on behavior.
By using various commands such as net user and net localgroup of the Net utility within Windows, and id and groups within macOS and Linux, adversaries can list local users and groups. Furthermore, local users can be enumerated through the use of the /etc/passwd file on Linux and the dscl.list/Users command on macOS.
Why You Need to Monitor for the Misuse of Native Window Commands
This is inherently challenging to legislate for with security practices as many of the commands used are relatively common in the day-to-day activities of internal system administrators. As a result, the solution of simply blocking these commands to prevent account discovery is not viable in these cases.
While detecting for this type of activity demands significant care and attention to be paid to the rules deployed, the value gained from intercepting attacks at such an early stage of the cyber kill chain cannot be emphasized enough. Typically, attackers are not fully entrenched when this type of activity is detected, meaning if swift action is taken, it is theoretically possible to prevent data breaches or even catch an attacker in the act.
As mentioned in previous spotlights, the concept of Living off the Land and hiding in plain sight has seen a growing prevalence as adversaries have become more intelligent about their attacks. As the money involved in cyber warfare has increased, the thought attackers put into evasion attackers has drastically increased as well.
In reality, keeping ahead of attackers, especially major Ransomware-as-a-Service providers that are reported to be sitting on war chests worth billions of dollars, is likely an impossible task. Even so, it is crucial to continuously develop security platforms to maintain pace.
How Can LogRhythm Help You?
Focusing on detecting this type of activity in isolation will lead you down a dark hole of false positives and alert fatigue. The fact is that the commands being used by attackers are for entirely legitimate purposes on a day-to-day basis. Hence, instead of implementing a simple log observed style rule block, we will leverage the Unique Values Observed rule block.
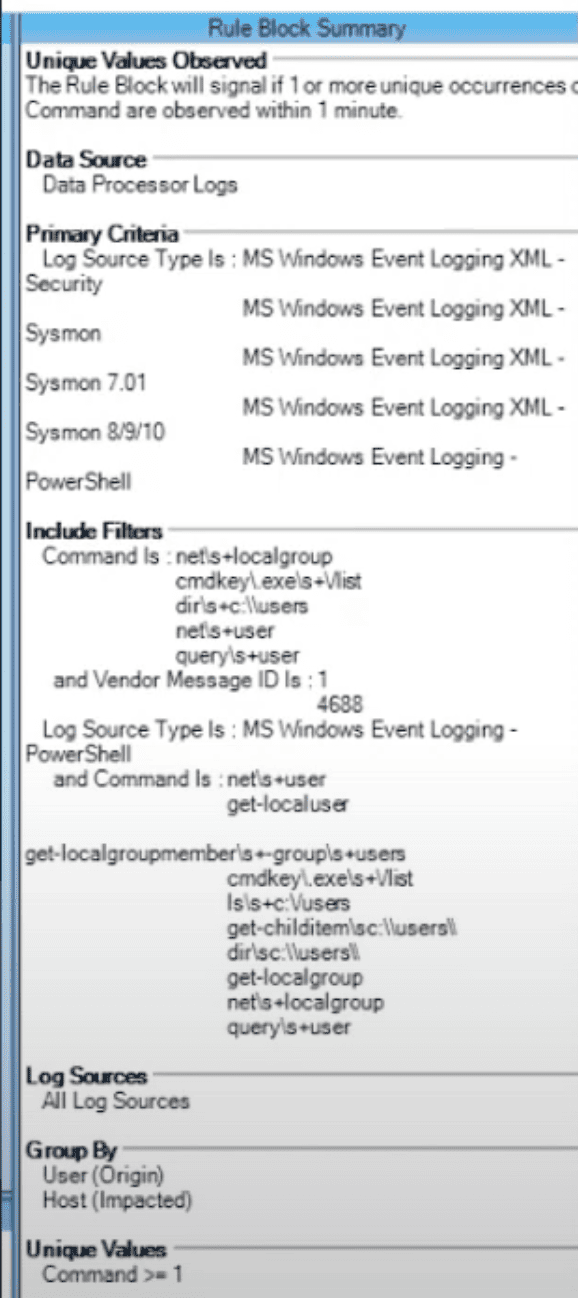
This rule is designed to identify specific situations where an attacker, not knowing which commands are and are not enabled on a victim’s machine, runs multiple innocuous commands. Individually, these commands being run do not raise concern, but when two, three, four, or more, run in rapid succession, it raises potentially suspicious behaviour.
Additionally, this rule can be narrowed down even further if you wish to monitor specific individuals instead of the entire user base. For example, it’s highly improbable that individuals in your C-level, HR or Finance teams will run this kind of command; therefore, in the case that they do, it will highlight something your team needs to investigate.
For more information on how to enable these rules within your LogRhythm deployment, check out our community page to read more, download, and then import the rule into your platform.
For other Security Spotlight episodes, you can access the full playlist here.
