In the physical world, “living off the land” simply means to survive only by the resources that you can harvest from the natural land. There may be multiple reasons for doing this — perhaps you want to get “off the grid,” or maybe you have something or someone to hide from. Or maybe you just like the challenge of being self-sufficient.
In the technology world, “living off the land” (LotL) refers to attacker behavior that uses tools or features that already exist in the target environment. In this multi-part blog series, we’ll explore why attackers use LotL, review a selection of the tools and features they use, and discuss examples of actual LotL attacks. We’ll also provide some guidance for detecting and preventing some of the commonly used approaches.
Why Attackers Live off the Land
Let’s start with why attackers use tools that already exist in the environment to execute plan an attack. Attackers may be motivated by one or many of the following reasons:
Fly Under the Radar/Avoid Detection
Attackers may choose to fly under the radar of either prevention or detection technologies. Typically, prevention technologies will use a signature-based approach to detect and quarantine malicious processes. They may also use hash values or other indicators of comprise (IOCs) to detect a process.
While attackers can change (indicators of compromise) IOCs relatively easily (see The Pyramid of Pain), using pre-existing software avoids the process being flagged as suspicious. It also saves the attacker cycles in developing the binary to deliver an attack.
The Pyramid of Pain
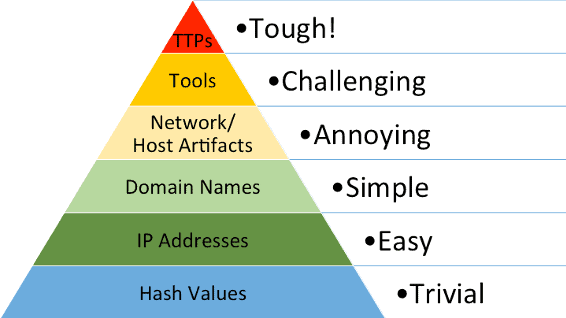
Figure 1: The pyramid of pain represents the difficulty level for attackers to change indicators that a defender might use to detect their activity.
Use Power Tools Already Embedded in Operating Systems
Operating systems typically carry tooling for automation and scripting administrative activities. Windows PowerShell is a good example. Every Windows OS since November 2006 includes PowerShell. This makes it a pervasive tool in a typical enterprise environment. These tools will typically provide easy access to both local and domain-based configuration. For example, with PowerShell, you can configure anything from Active Directory objects to local raw disks.
Tooling Can be Difficult to Develop and Distribute
Typically, an attacker will scope out a target, but he or she may not know the entire environment the tools operate in. This creates some hurdles for building, compiling, and testing program. These tools should allow for a variety of operating systems and environments, and it may be difficult, if not impossible, to test for every possible scenario.
Why Attackers Use Existing Tools to Execute Attacks
Attackers that use already existing tooling avoid the need to build, test, and QA tools. They don’t have to worry about compatibility, dependencies, and so forth. It’s also challenging to build programs that are stealthy enough to avoid detection, particularly if something runs at kernel level. Ultimately, it’s probably cheaper and quicker to use existing tooling.
From an attacker’s perspective, using already existing tools and features makes the defender’s job inherently more difficult. Picking out the malicious use of built-in tools versus the authorized use of tools by the system administrator can be somewhat like looking for a needle in a haystack.
Interested in learning more about how to combat LotL attacks? Look for upcoming blogs that will surface some techniques that you can use to reduce the size of the haystack and help find those needles. One of the interesting things with combating LotL attacks is that you can begin to see the tactics techniques, and procedures (TTPs) that a particular attacker uses. Once you can detect TTPs, it becomes a bigger challenge for the attacker to change, rather than just changing a hash value to avoid detection.
In our next blog post, we’ll take a look at Windows Scheduled Tasks through the lens of living off the land. It’s a pervasive tool in Windows Operating systems, and a favorite among threat actors.