Malicious actors have begun using Microsoft’s Dynamic Data Exchange (DDE) mechanism to deliver payloads via Microsoft Office documents instead of the traditional embedded macros or VBA code. Specially crafted Microsoft Office documents sent via email can be used to carry out an attack, exploiting end users. Using LogRhythm’s integration with Carbon Black, security operations center (SOC) analysts can efficiently detect, mitigate, and remediate a Microsoft DDE-based attack.
DDE Explained
Microsoft Office (MS Office) contains a mechanism called Dynamic Data Exchange (DDE). Microsoft defines DDE as follows:
“Windows provides several methods for transferring data between applications. One method is to use the Dynamic Data Exchange (DDE) protocol. The DDE protocol is a set of messages and guidelines. It sends messages between applications that share data and uses shared memory to exchange data between applications. Applications can use the DDE protocol for one-time data transfers and for continuous exchanges in which applications send updates to one another as new data becomes available.”
DDE acts as an inter-process protocol and is traditionally used to transfer data between MS Office applications. For example, DDE often appears as a table in a Microsoft Word document that is automatically updated with the data from a Microsoft Excel spreadsheet.
Recently, attackers began utilizing DDE to compromise victim machines by embedding commands within MS Office documents. Compared to normal attack methods whereby a macro or VBA code is embedded into an MS Office document, DDE documents are much simpler to weaponize. This is because DDE documents only require a single custom field as opposed to the more voluminous VBA code. The custom field, which is a user option available in most MS Office applications, can be specially modified to contain malicious code.
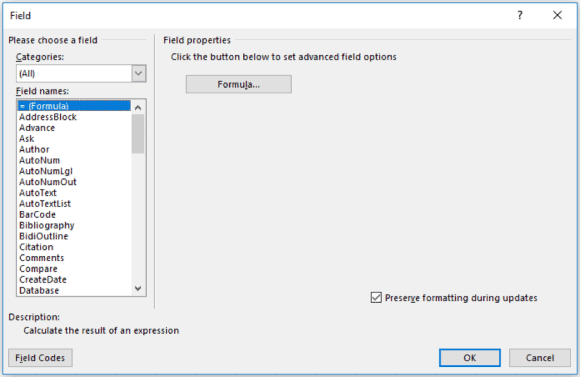 Figure 1: The Custom Field Can be Specially Modified to Contain Malicious Code (Click Image to Enlarge)
Figure 1: The Custom Field Can be Specially Modified to Contain Malicious Code (Click Image to Enlarge)
A macro or VBA-enabled document is only effective when macros are enabled within the MS Office application. It is fairly common to disable macros via group policy or similar methods. A DDE document attack requires social engineering to entice the end user into accepting two warning prompts. These techniques have brought attention to what DDE is and how these attacks can be pre-empted. Microsoft Word, Excel, and PowerPoint are all affected. In addition, recent discoveries by Sophos found that Microsoft Outlook can also be exploited.
A DDE Attack
The original DDE proof of concept takes advantage of a mechanism in Microsoft Office products that has existed for many years. At its root, the attack is a social engineering attack, which relies on the end users blindly accepting pop-up messages—allowing embedded code to execute. This embedded code typically includes spawning a command prompt, PowerShell, a reverse shell, or an additional download and execution of malware. There are also obfuscation techniques to further hide the infected document’s true intentions. Recent reports show Hancitor malspam and the Necurs Botnet pushing Locky via DDE-enabled documents. (Note: Malware-Traffic-Analysis.net provides further details.)
Below you can see how a DDE attack might appear in some of the affected Microsoft Office applications. In all cases, simply clicking “No” on both prompts will avoid execution of the malicious content.
DDE Attack in Microsoft Word
When opening a DDE-enabled Word document, the user is first presented with the following prompt.
 Figure 2: DDE-Enabled Word Document Prompt (Click Image to Enlarge)
Figure 2: DDE-Enabled Word Document Prompt (Click Image to Enlarge)
Assuming the user clicks “Yes,” a second prompt appears.
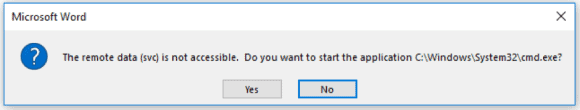 Figure 3: Second Prompt from a DDE-Enabled Word Document that Could Spawn Malicious Activity (Click Image to Enlarge)
Figure 3: Second Prompt from a DDE-Enabled Word Document that Could Spawn Malicious Activity (Click Image to Enlarge)
If “Yes” is clicked a second time, a command will run to either spawn a command prompt, PowerShell, or other malicious code.
DDE Attack in Microsoft Excel
In Excel, a slightly different prompt appears, which again relies on the end user blindly clicking the prompts.
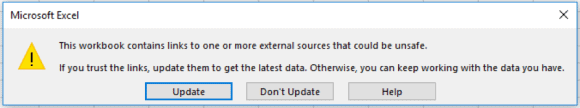 Figure 4: DDE-Enabled Microsoft Excel Spreadsheet Prompt (Click Image to Enlarge)
Figure 4: DDE-Enabled Microsoft Excel Spreadsheet Prompt (Click Image to Enlarge)
By clicking “Update” the same result as seen above is achieved. A second prompt is displayed, again relying on the user to respond “Yes.”
 Figure 5: Second Prompt from a DDE-Enabled Word Document that Could Spawn Malicious Activity (Click Image to Enlarge)
Figure 5: Second Prompt from a DDE-Enabled Word Document that Could Spawn Malicious Activity (Click Image to Enlarge)
DDE Attack in Microsoft PowerPoint and OneNote
PowerPoint and OneNote documents can be weaponized by embedding an Excel spreadsheet within the encapsulating document. The image below depicts an embedded Excel document within a OneNote page. Once the Excel document is opened, behavior similar to that of the above example is observed.
 Figure 6: A DDE-Enabled Excel Document is Embedded within a OneNote Page
Figure 6: A DDE-Enabled Excel Document is Embedded within a OneNote Page
DDE Attack in Microsoft Outlook
Recently, other researchers, including @GossiTheDog and Sophos, have discovered that DDE can also be abused in Outlook.
An attacker could weaponize the email message by simply using “Rich Text Format” (RTF), adding the same code used in the Word example above, and adding an extra object (such as a picture) to the email.
 Figure 7: A Microsoft Outlook Email is Weaponized via the DDE Protocol
Figure 7: A Microsoft Outlook Email is Weaponized via the DDE Protocol
Mitigation
Microsoft has released software updates available for various versions of Word, Excel, and Office 2007 through 2016 which disables the DDE protocol. These are discussed in security advisory ADV170021. If, however, you are unable to install the relevant update, or if you need to disable the DDE protocol for other Office applications, refer to Microsoft security advisory 4053440 for additional mitigations. These mitigations include disabling DDE via the Office UI and via the Windows Registry.
In Part 2 of this blog post, I’ll show how you can detect and remediate DDE attacks as they happen using LogRhythm and Carbon Black.