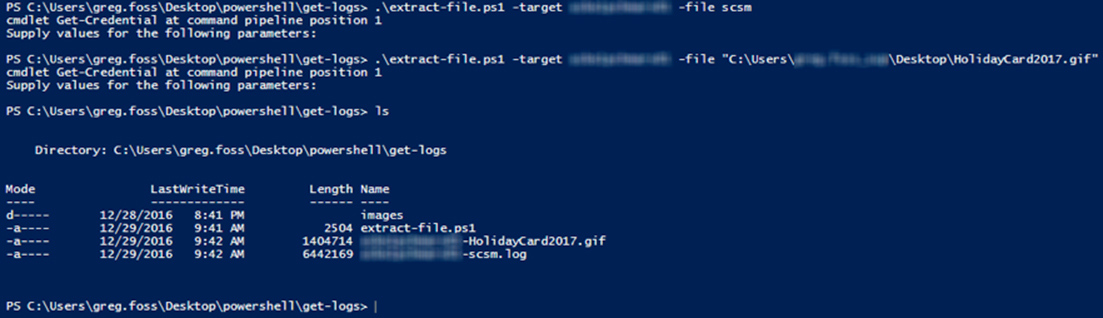
Recently, a question was posed on the LogRhythm Community around how to extract the SCSM log from a remote Windows host. I put together a quick PowerShell script to extract not only the System Center Service Manager (SCSM) log file, but also any of the other LogRhythm System Monitor Agent log files. I also provided the option of pulling any remote file to the local host by way of PowerShell remoting. This script is available at the GitHub link below:
Click on images to view larger
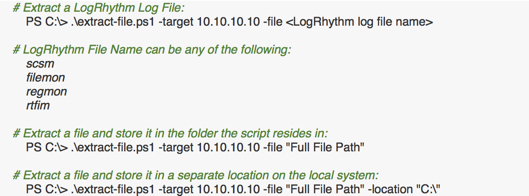
You can either supply the full path to any file or remote host, or you can enter a general term for the LogRhythm log file you would like to collect. The tricky part is that if you want to pull a file that is in use by the System Monitor agent, that is not possible until the agent has been disabled. So, when pulling SCSM log files, the service is temporarily stopped until the file is retrieved. Then it is started again. For any other files, the SCSM service is not touched.
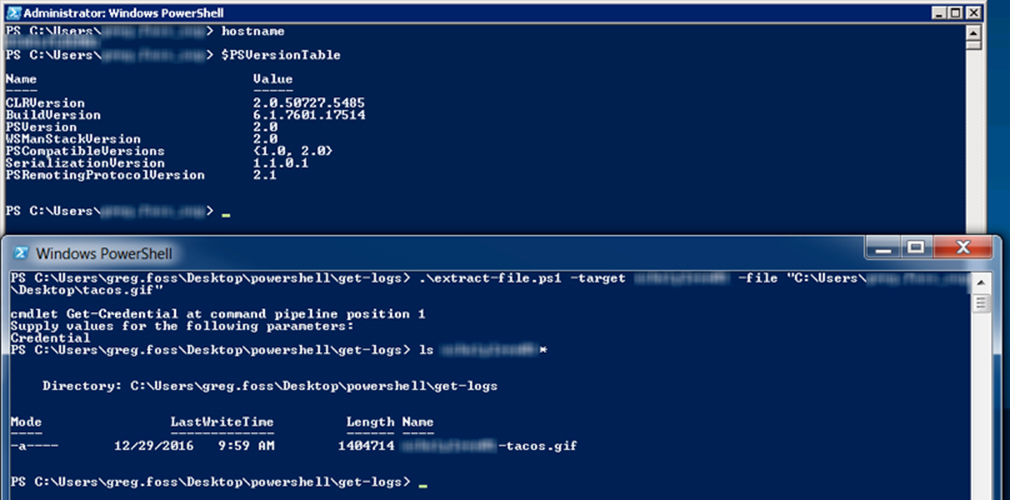
It’s pretty simple and effective. The only caveat is that you need to execute this from a system with Windows Management Framework, version 5 installed. However, you can run this against systems running PowerShell versions as low as version 2.
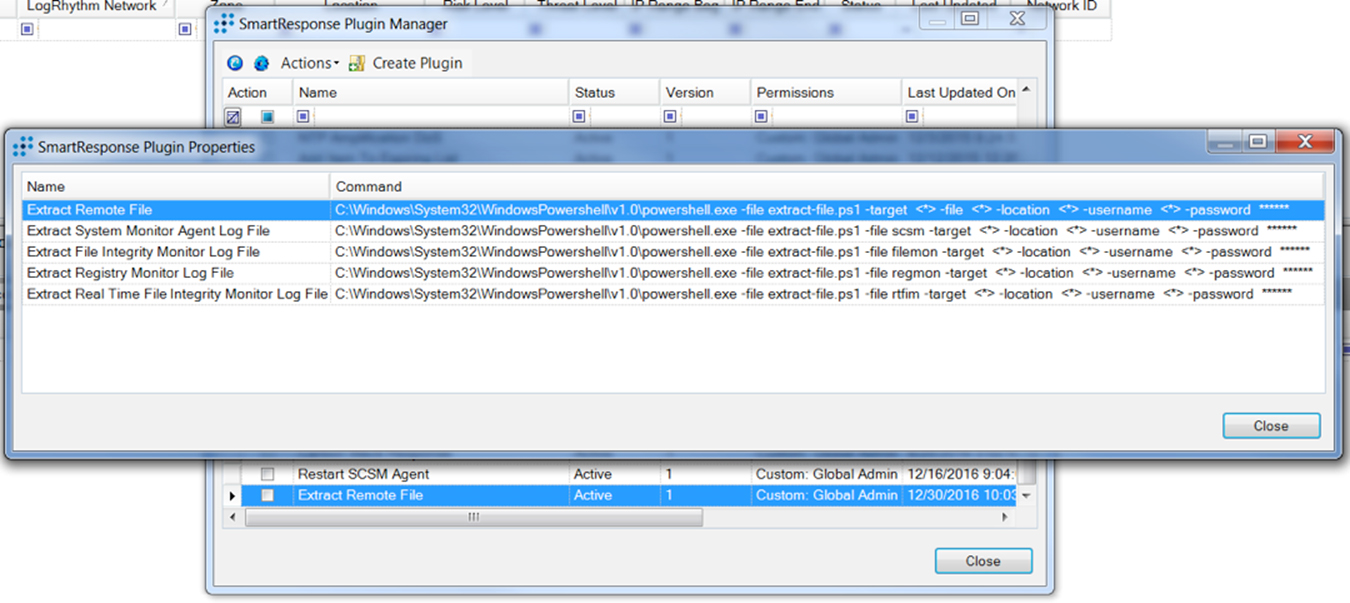
Tying this into the SIEM, we can turn this into a SmartResponse automated playbook action and pull these files automatically, based off of specific alarms.
You can use this SmartResponse and standalone script for everything from troubleshooting remote SCSM agents to pulling any files from remote hosts, which can be invaluable during security investigations.
To read more, view the Community post.
To download the script and SmartResponse automated playbook actions, click the button below.