Cryptocurrency is a hot topic right now, and even though its price is drastically falling across the board, this incredible technology will have lasting impacts on the world for years to come. Though a majority of the focus on cryptocurrencies has been on their negative uses, such as ransomware, the trade of illicit goods, or an easier way of laundering money, there are many positive applications of cryptocurrencies that should be considered. In fact, cryptocurrencies are currently paving the way for a new era of global commerce and trade outside of a central regulation authority.
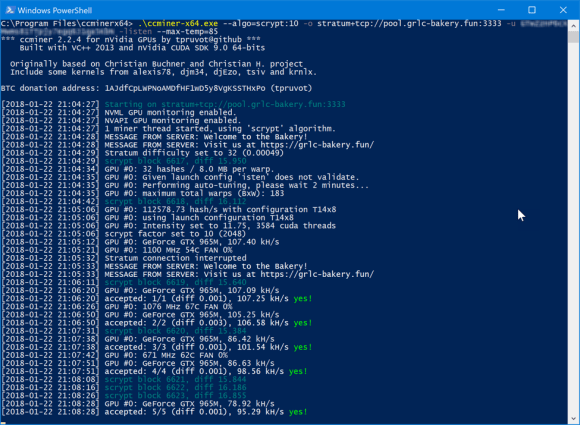
With the recent public spotlight on cryptocurrency, many people are exploring ways to mine the technology using their existing hardware. Normally, this method isn’t that profitable and comes with the risk of damaging your hardware if left unchecked. There are tons of new tools and methods to help you get started with mining. Below is an example of ccminer on a Windows system.
Figure 1: A ccminer on a Windows System
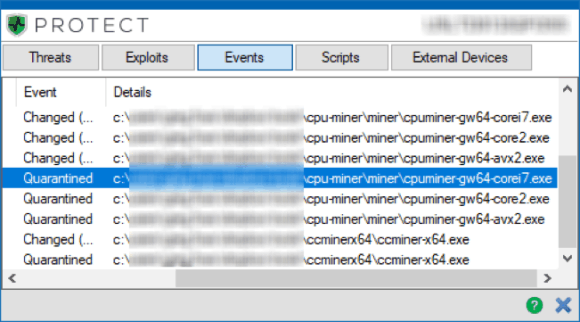
It’s perfectly acceptable for someone to use their own hardware to mine cryptocurrencies. However, many people attempt to utilize corporate resources to expand their mining empire, which can be a dangerous practice. Fortunately, this activity is easy to detect and block. In fact, a majority of mining applications are already flagged as malicious by corporate antivirus solutions. For example, Cylance detected ccminer and cpuminer as seen below.
Figure 2: Cyclance Detects ccminer and cpuminer
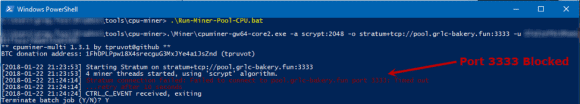
Even if the mining application is not blocked, miners need to connect to mining pools, which usually run on non-traditional ports, such as 3333. Luckily, most organizations already block these ports.
Figure 3: Port 3333 is Blocked
Passively Running Crypto-Mining Applications
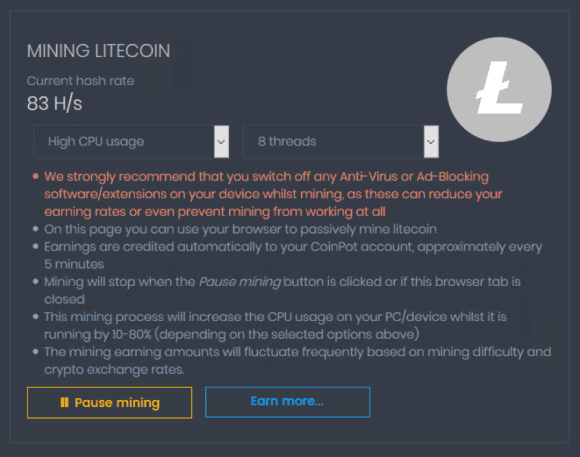
Seems pretty easy to detect and block on a corporate network, right? Unfortunately, it’s not quite that simple. There are ways to run crypto-mining applications and go undetected. Various websites, such as Coinhive, CoinImp, Coinpot, and others allow you to mine by simply visiting a webpage.
Figure 4: Web Page Enables Mining
These applications don’t have a high return on investment (ROI), and a portion of the mining goes to the overarching script owner. However, they offer a quick and easy way to mine cryptocurrency without the need to install anything on the target system. This works particularly well if you can get a large number of systems to visit a website and mine on your behalf.
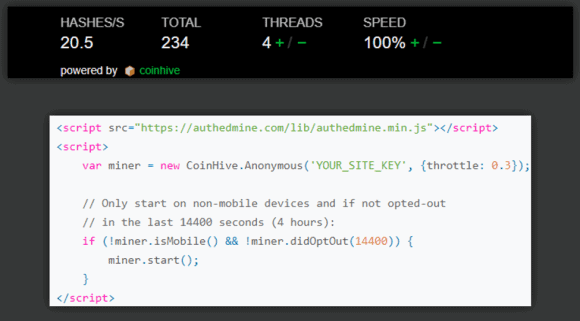
Coinhive is the most commonly observed web application crypto-mining provider. It delivers quick and easy JavaScript that can be injected into existing websites and advertisements, allowing the miner to profit from small amounts of CPU utilization over time. While it is possible to notify website visitors that this is happening, often attackers will run this application passively in the background. This occurs by copying and modifying the Coinhive JavaScript code. This method of passively running crypto-mining applications is referred to as cryptojacking.
Figure 5: When Copied and Modified, Coinhive JavaScript Allows for Passively Mining Cryptocurrency
Passively mining cryptocurrency in the background is a far less significant risk than other possible attack scenarios. It is even less risky than a user collecting from cryptocurrency faucets—that is, until passively mining cryptocurrency becomes more widespread and impacts energy costs or even destroys hardware.
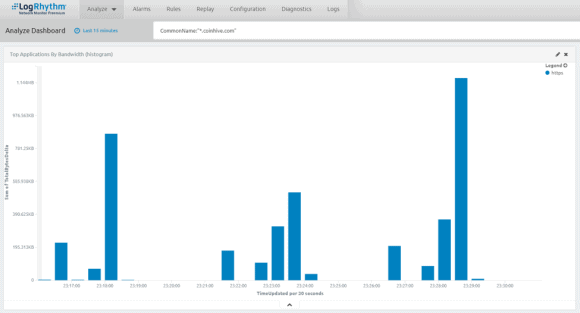
Fortunately, detecting this activity is really straightforward. In fact, browser add-ons such as uBlock Origin, will block a majority of cryptominers by default. And if you’re on a website or are otherwise affected by a cryptominer, you’ll see your web browser processes spiking. With LogRhythm NetMon, you can use a simple domain rule to see who is hitting known cryptomining websites, making this activity easy to track and monitor.
Figure 6: LogRhythm NetMon Gives You Visibility Into Who is Frequenting Known Cryptomining Websites
Use Case: Detecting Cryptojacking at LogRhythm
At LogRhythm, we typically support developers who choose to run cryptominers on their websites as opposed to advertisements. After all, ads have a tendency to deliver malware. Previously, LogRhythm did not block known mining sites until they became a problem.
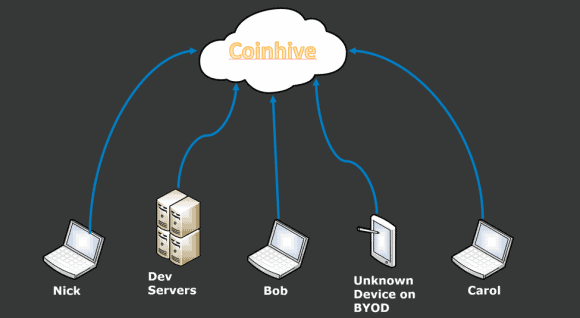
For example, over the course of a week, we noticed a few systems were consistently sending traffic to Coinhive. Normally we wouldn’t be concerned, but this was consistent, around-the-clock mining activity from a few end-user systems, a development server, and a personal system registered on our guest network.
Figure 7: Devices Consistently Send Traffic to Coinhive
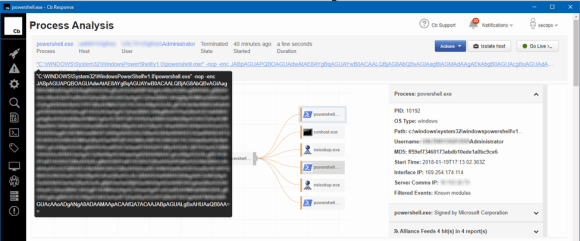
In addition to the alerts generated within the SIEM when the uptick in Coinhive traffic began, two of the affected users submitted IT tickets, noting their systems were slow and that fan icons were spinning non-stop. When we investigated their hosts with Carbon Black Response, we found that the culprit was Internet Explorer running as a background process.
Figure 8: Internet Explorer Runs as a Background Process
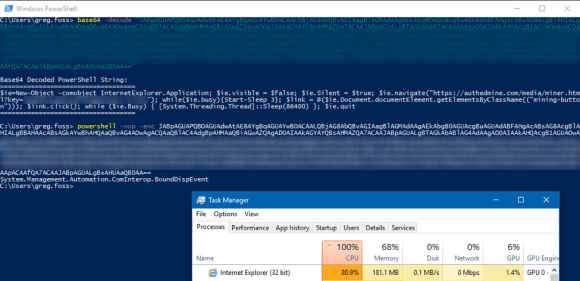
This immediately looked suspicious, so we decoded the Base64 encoded PowerShell and validated that this launched Internet Explorer in headless mode.
Figure 9: The Base64 Encoded PowerShell is Decoded
This code was likely taken from Rvrsh3ll’s CrypoCureencyPowerShell example and compressed.
Identifying the Culprit
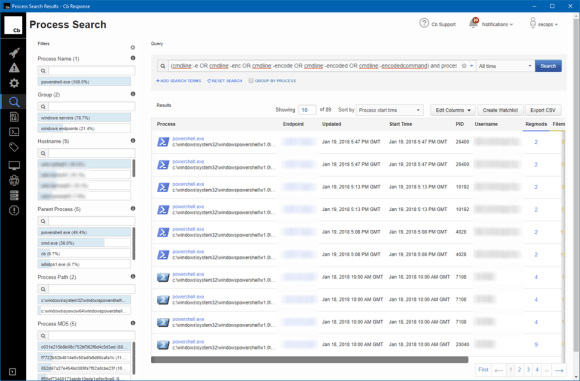
While digging into this suspicious activity, our encoded PowerShell alarms began to trigger on additional systems. Each contained the same mining key and were executed by the same user (our culprit), with the exception of the end-user laptops.
Figure 10: Additional Systems Contain the Same Mining Key
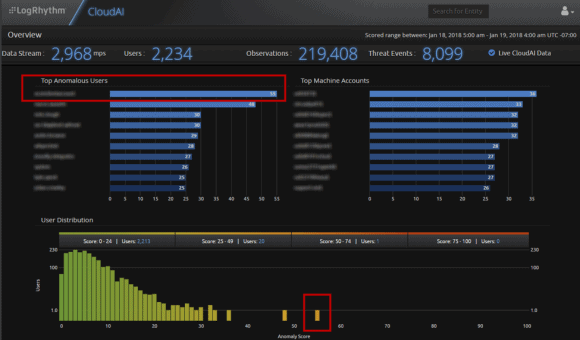
Upon checking in with LogRhythm CloudAI, we confirmed that the user behind this activity was our top most anomalous user during this time period. We’ll refer to this user as “Nick” for the purposes of this blog.
Figure 11: LogRhythm CloudAI Identifies Top Anomalous Users
We traced all authentication activity from Nick’s system to a select few development servers, where Nick used PsExec and Remote Desktop to launch the PowerShell script across other hosts that he access in the development VLAN. For the laptops, we reviewed camera footage and endpoint logs for the time period the scripts were detected. We then determined that Nick used a USB Human Interface Device (HID) to run the script when his co-workers left their systems unlocked.
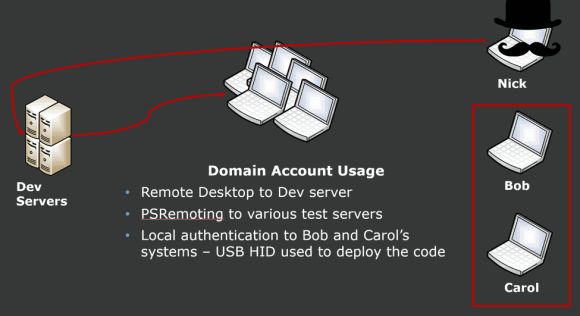 Figure 12: Nick Uses a USB Human Interface Device (HID) to Run a Script on his Co-Workers’ Systems
Figure 12: Nick Uses a USB Human Interface Device (HID) to Run a Script on his Co-Workers’ Systems
All in all, this was a simple insider threat scenario that we easily detected and stopped before this individual turned LogRhythm into a part-time cryptocurrency mining operation. This example highlights the need for focused user entity and behavioral analytics (UEBA) across the organization, as threats to your business can come in many shapes and sizes.
If you’re looking to detect and block this activity on your network, I suggest reviewing the CoinBlockerLists developed by ZeroDot1 available here: https://github.com/ZeroDot1/CoinBlockerLists. These lists can be integrated with the SIEM and NetMon to increase visibility into this activity on your network.
 \
\