Here at LogRhythm, we are excited to announce an updated release of our Threat Intelligence Services (TIS). If you’re not familiar with TIS, its easy-to-use utility enables LogRhythm customers to rapidly add and configure a wide array of threat feeds from commercial or open-source feeds.
However, in the new release of TIS (1.5), there is support for Structured Threat Information eXpression (STIX) threat data via Trusted Automated Exchange of Indicator Information (TAXII). But before I cover the details of what STIX and TAXII are, let’s cover the why.
The driver for the creation of a standardized manner around the format and exchange of cyberthreat information (CTI) came from how IT and the security industry was previously sharing (and some still are) threat data, such as relying on emails, private portals or real-time chat. With constantly changing indicators of compromise, it was simply not a scalable approach.
What is STIX?
STIX is a structured language used by computers to describe cyber threats. STIX provides CTI metadata such as IPs, domains, emails, filehashes, URLs, etc. It is used by many organizations that provide CTI, such as:
- The U.S. Department of Homeland Security
- Financial Services Information Sharing and Analysis Centre (FS-ISAC)
- Microsoft Active Protections Program (MAPP)
Click here for the full list of supporters and contributors.
What is TAXII?
TAXII is a standardized transport for the exchange of CTI (or, put another way, a technical analogy is to think of STIX like HTML and TAXII like TCP).
In order to consume STIX CTI, it requires access to the TAXII server (LogRhythm TIS is a TAXII client that consumes STIX from a TAXII server). There are many TAXII servers available, but Soltra Edge is one that LogRhythm customers (especially those in finance) are using (often to meet FFIEC CAT requirements).
Using LogRhythm TIS to Add STIX CTI
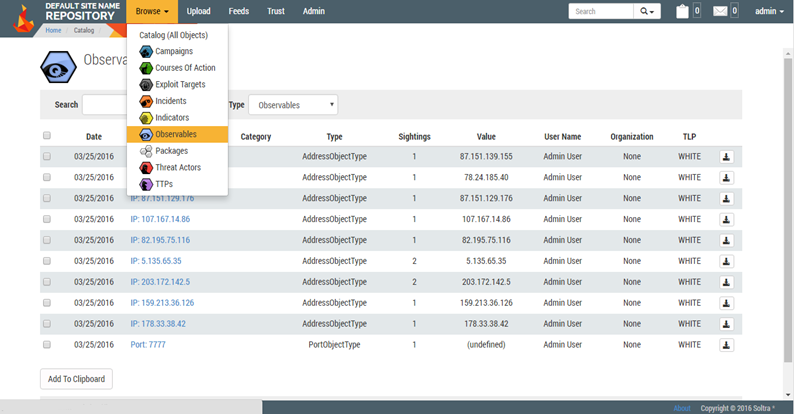
Like all the existing threat data feeds from our security partners and the open-source feeds that LogRhythm supports, adding STIX is a straightforward exercise. Here is an example Soltra® Edge TAXII server configured with the feeds of CTI we wish to consume:
Click images to expand
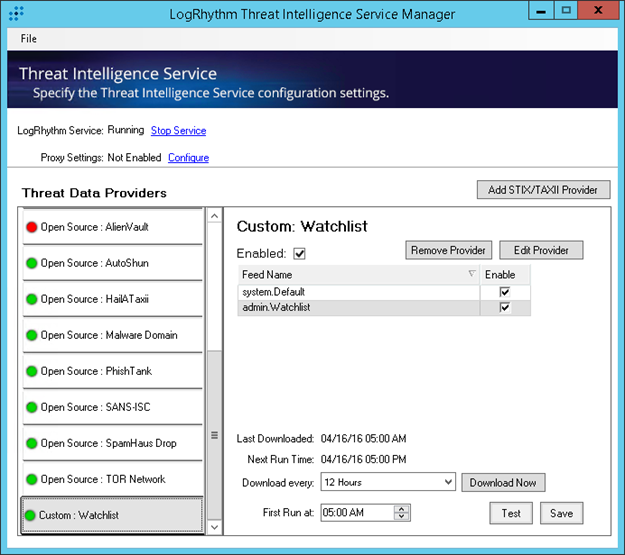
We can then load up the LogRhythm TIS and add our custom TAXII provider (the Soltra Edge TAXII server).
And finally, the STIX CTI is automatically parsed into lists of appropriate types:
And that’s it! A couple of clicks, and you’re consuming STIX CTI which will be utilized by the existing Threat Analytics Suites within the LogRhythm Security Intelligence Platform. LogRhythm’s AI Engine will automatically begin looking for examples of CTI discovered in the environment, such as outbound connections to low reputation IPs, DNS requests to domains associated to attacks, or email file attachments known as phishing attempts, corroborated with other discovered endpoint or user behavior changes.
LogRhythm’s Threat Intelligence Service is available at no extra costs to all LogRhythm customers. It supports 6.2.x, 6.3.x, and 7.1.x LogRhythm deployments. You can download the TIS installation files and documentation from our Support Portal.