Attackers use a number of resources to find a way into your organization. That’s why it’s important to understand the vulnerabilities that exist to keep your organization protected.
One common method of attack is to leverage routing protocol to eavesdrop. Specifically, an attacker could redirect an entire organization’s traffic to any destination by leveraging routing protocol such as Open Shortest Path First (OSPF).
How can you stay protected? The key is to keep your OSPF routing protocol networks safe from attackers.
Open Shortest Path (OSPF) First Monitoring
Open Shortest Path First (OSPF) is the most popular interior gateway routing protocol on the internet. Internet service providers (ISPs) and large customers use OSPF as a routing protocol. OSPF is a link state routing protocol. Every router in the OSPF network will form a trusted relationship with the neighbor routers. These neighbor routers should be in the same subnet and they should have the same characteristics such as (area id, hello and dead timers, and network mask). OSPF is often used within an autonomous system.
OSPF dynamically discovers neighbors using hello protocol and the hello protocol is sent as a broadcast to an OSPF listening multicast address 224.0.0.5.
 Figure 1: OSPF uses hello protocol to discover neighbors
Figure 1: OSPF uses hello protocol to discover neighbors
Once the neighbor routers are discovered, the router advertises its links to them, which are called Link State Advertisements (LSAs). The LSAs are advertised throughout the autonomous system. A router receiving an LSA from one of its neighbors resends the LSA to other neighbor routers. The routing database is identical in all routers. Using this database, a router obtains a complete picture of that topology.
Problems with OSPF Networks
One issue with OSPF routing protocol networks is that they can be easily compromised. Network administrators or security teams do not pay attention to routing attacks and are negligent. Mostly these types of attacks go undetected, and the impact is usually significant.
The integrity of your routing domain depends on the security of the least secure router in the domain. By owning a single router in an OSPF network in a remote branch or headquarters, an attacker could control that entire routing domain.
For example, the adversary could force traffic toward a bogus gateway for eavesdropping/network cuts/traffic diversion/longer route, and more through an adversary-controlled gateway router. You should note that an OSPF network can be divided into sub-domains called areas. An area is a logical collection of OSPF networks, routers, and links that have the same area.
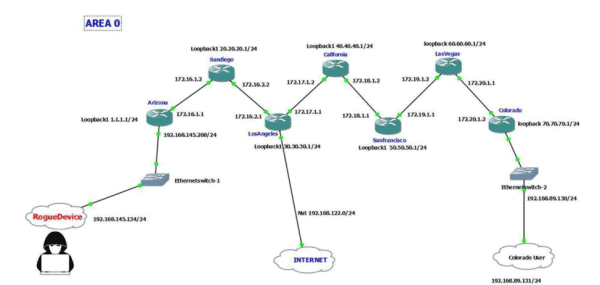 Figure 2: An attacker that gains access to your routing domain could redirect traffic by injecting a bogus route
Figure 2: An attacker that gains access to your routing domain could redirect traffic by injecting a bogus route
An adversary (rogue device) could also join the OSPF network and form a trusted relationship with the adjacent router and learn about that entire routing domain such network types, links etc. Additionally, the attacker could inject routes to redirect traffic.
In the above design (see Figure 2), every router should go to the Los Angeles router for internet access. Someone using a Colorado router who needs internet access will be forwarded to the Los Angeles router by the Colorado router. An attacker, by joining the OSPF trusted relationship as a rouge device, could inject a bogus route and redirect the required or all traffic to the rogue device for passive eavesdropping.
Targeted attacks could even redirect only certain sets of traffic such as DNS traffic. Users could ask for Google.com, and the rogue device could give the IP of Facebook.com as a response, and the remaining DNS queries could receive the legitimate response.
Every router running in a single area will have an identical OSPF database. The below screenshots were taken from a simulated Cisco demo environment. The command “show ip ospf database” displays the list of routers that are part of the OSPF routing domain. Every router is identified with Router ID. For example, 0.0.0.1 is not an IP address — it’s an identifier that we configured in every router. The below screenshot (Figure 3) is before the rogue device joined the OSPF network.
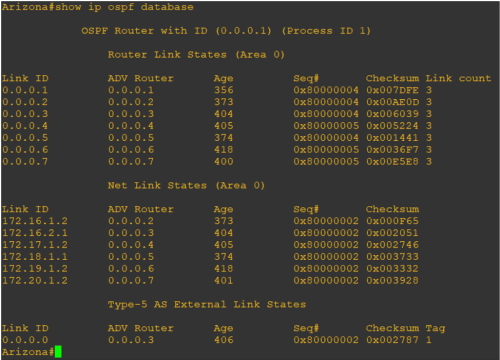 Figure 3: The OSPF database before a rogue device joins the network
Figure 3: The OSPF database before a rogue device joins the network
The below screenshot (Figure 4) is after the rogue device 192.168.145.134 joined the OSPF neighborship.
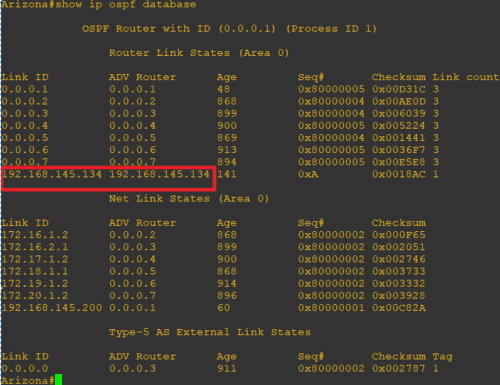 Figure 4: The OSPF database after a rogue device joins the network
Figure 4: The OSPF database after a rogue device joins the network
An OSPF-running network could have hundreds of routers with multiple areas. So, how do you protect against a rogue device joining the OSPF neighborship?
Configuring an interface as passive will not participate in OSPF and does not establish adjacencies or send routing updates. A second method is OSPF authentication with hashing — a good word list is all an adversary needs to break into the OSPF authentication. Unfortunately, we have never seen authentication or passive interface. The network or operations teams never consider security, and the security team does not have any control over routers.
Determine a Solution
To detect whether a rogue device has joined OSPF neighborship using LogRhythm, you should monitor the routers joining the OSPF neighborship with an observed LogRhythm AI Engine rule. AI Engine, which is part of the LogRhythm NextGen SIEM Platform, gives you visibility into risks, threats, and operational issues that might otherwise go undetected.
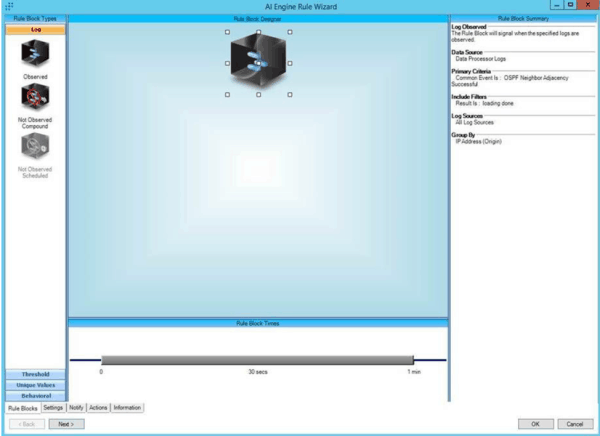 Figure 5: Monitor routers that join the OSPF neighborship to detect a rogue device
Figure 5: Monitor routers that join the OSPF neighborship to detect a rogue device
 Figure 6: LogRhythm AI Engine helps monitor for rogue devices
Figure 6: LogRhythm AI Engine helps monitor for rogue devices
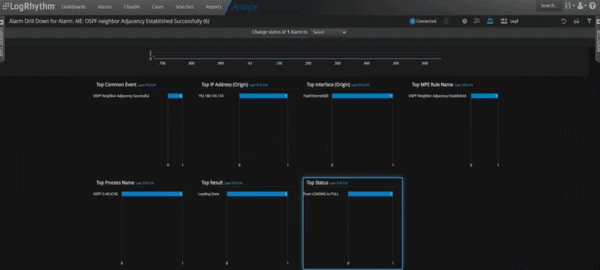 Figure 7: Adversary running router 192.168.145.134 joins an OSPF neighborship with 192.168.145.200
Figure 7: Adversary running router 192.168.145.134 joins an OSPF neighborship with 192.168.145.200
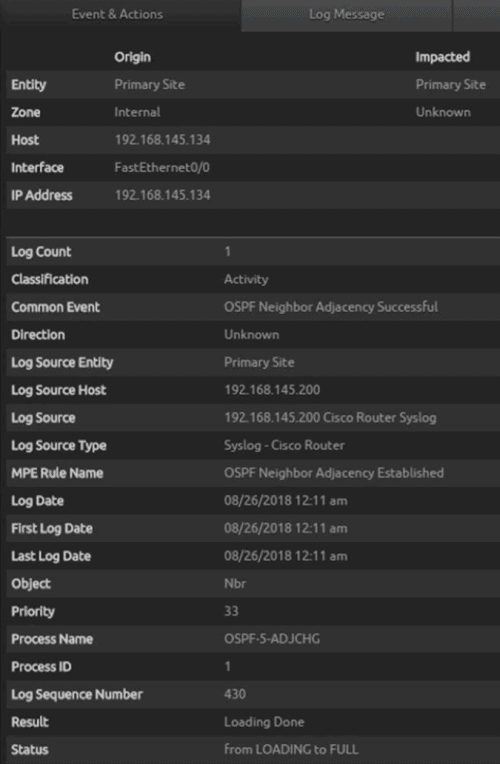 Figure 8: LogRhythm AI Engine gives you visibility into issues you might otherwise miss
Figure 8: LogRhythm AI Engine gives you visibility into issues you might otherwise miss
The next step is to create an exclude filter list with “show IP OSPF database.” Different vendors should use a different command. Legitimate routers’ links could be flapping sometimes by creating an exclude filter that will have no false positives or alarm fatigue.
 Figure 9: Create an exclude filter list to show the IP OSPF database
Figure 9: Create an exclude filter list to show the IP OSPF database
Finding Value in Monitoring Routing Protocols
Monitoring routing protocols is crucial in every organization. LogRhythm detects and responds to OSPF malicious activity executed by an adversary that joined the OSPF routing domain. That’s not all. LogRhythm can also shut down the OSPF speaking interface of the router that tried joining the OSPF neighborship.
Let us know how this works for you and other tips you’ve encountered!