Following the steps of her fellow neighbours in the APAC region, Thailand enforced the Personal Data Protection Act (PDPA) as of June 1 2022. Signed in 2019 and postponed twice during the pandemic, this Act has been the talk of the town in Thailand.
In this blog post, we will be discussing what the PDPA is and things to be aware of when trying to comply to this newly-enforced law.
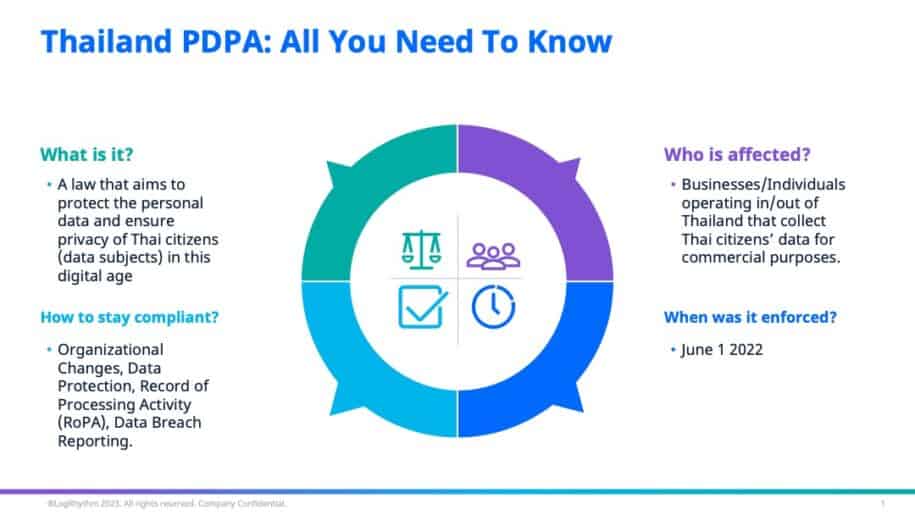
What is PDPA?
Thailand’s PDPA aims to protect the personal data and ensure privacy of her citizens (data subjects) in this digital age. It also regulates the collection, use, disclosure, and/or transfer of personal data by businesses (data controller or data processor) for commercial purposes.
The PDPA covers all individuals, websites and businesses that collects, uses, discloses, or transfers personal data in Thailand for marketing or sales purposes or behaviour tracking. This law also applies to foreign-owned entities that operate outside of Thailand that collect, use or disclose the personal data of Thai citizens.
How to Comply with Thailand PDPA
With the implementation of the PDPA, there is growing importance placed on implementing the right security measures to protect collected Personal Data. In fact, the PDPA affects security professionals and teams in two key areas: Data Protection and Data Breach Reporting.
Under the PDPA, it is essential for your organization to be prepared with the necessary security systems, controls, and response in the event of a data breach. Failure to comply may result in a criminal penalty of up to a year.
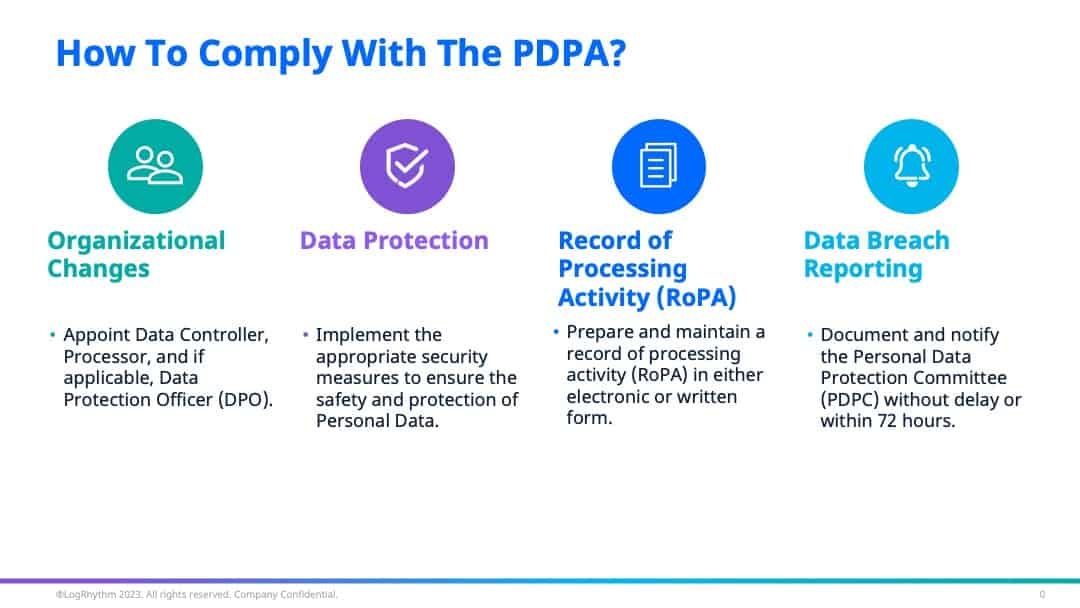
The four key requirements to comply with Thailand PDPA are:
- Organisation Structure
- Data Protection
- Record of Processing Activity (RoPA)
- Data Breach Reporting
Organisation Structure
The first key requirement for your business is to introduce new roles within the organization’s structure for data protection.
Under the data protection law (Section 6), organizations are required to appoint a Data Controller who can make decisions regarding the collection, use, or disclosure of the Personal Data, and a Data Processor who operates in relation to the collection, use or disclosure of the Personal Data based on the orders given by or on behalf of a Data Controller.
Section 41 also outlines the appointment of a Data Protection Officer (DPO) under certain circumstances. If appointed, the DPO’s main duties lies in advising and tracking the performance both the Data Controller and Processor in regards to the compliance of the Act.
Data Protection
Once you have appointed the new roles, it is necessary to implement the relevant security measures for data protection.
Under Section 37, one of the Data controller’s duties is to provide appropriate security measures to prevent the unauthorized or unlawful loss, access to, use, alteration, correction, or disclosure of Personal Data. Additionally, these security measures should be reviewed when it’s necessary or, when technology has changed to efficiently maintain the appropriate security and safety.
Some of these security measures can include:
- Implementing and maintaining data storage systems and data processing devices.
- Implementation of examination system for erasure of Personal Data when retention period ends.
- Limit and manage personal data access to only the designated users.
- Implementation of monitoring systems to detect and respond to a personal data breach.
Record of Processing Activity
Another key requirement for your organization to follow is to prepare and maintain a record of processing activity (RoPA) that provides an overview of all personal data collected in either electronic or written form. These records are to be made available for the Personal Data Protection Committee (PDPC) inspection. Under Section 39, here is a list of information to include:
- Details of the data processor and its representative
- Details of the relevant data controller and its representative
- Details of the data protection officer (if any)
- Nature of collection
- Use or disclosure of personal data, including personal data and purposes of the collection, use or disclosure of such personal data, as assigned by the data controller
- Types of persons or entities that receive personal data in case of transmitting or transferring personal data abroad; and
- Description of security measures.
Data Breach Reporting
The final requirement for your organization is to ensure a smooth reporting in the event of a personal data breach.
Section 37 of the PDPA had also outline the necessity to document and notify the PDPC of any Personal Data breach. This notification must be done without delay and, where feasible, within 72 hours after detecting it. If there is a high risk to the rights and freedoms of the affected individuals, it is also necessary to notify all impacted data subjects without delay.
Focusing your energy into ensuring these 4 key requirements are met is will help you check the box towards compliance to the PDPA.
Differences between GDPR and PDPA
As with most personal data protection regulations, the General Data Protection Regulation (GDPR) is a well-established framework from the European Union that performs a similar function. While the PDPA is similar to the GDPR in many aspects, there are still key differences between these two laws to pay attention to when trying to work towards compliance:
- Personal Scope
- Definition of ‘Personal Data’
- Penalties
Personal Scope
In terms of personal scope, Thailand’s PDPA does not apply to public agencies that maintain state security, including financial security of the state or public safety, prevention and suppression of money laundering, forensic science or cybersecurity. However, the GDPR may apply to public authorities. This means that most organisations will have to ensure that they re
Definition of Personal Data
In comparison to the GDPR, the PDPA’s definition of ‘personal data’ is not as detailed. For its European counterpart, it specifically includes IP addresses and cookie identifiers. However, in the PDPA, there is no mention of these. Additionally, despite the mention of the subject’s right to anonymise their personal data, the PDPA does not define anonymised or pseudonymised data.
Penalties
In regards to monetary penalties, the maximum penalty for non-compliance of the PDPA is a fine not exceeding THB 5 million (approx. €136k). This fine may feel little, especially when compared to its European counterpart where the penalty can be up to either 2% of global annual turnover or €10 million, or 4% of global annual turnover or €20 million. However, this is also discounting other losses in terms of potential deals and reputation damage that non-compliance can cause.
Thailand PDPA also outlines criminal penalties such as an imprisonment term not exceeding one year, as opposed to the pure administrative penalties associated in GDPR. This shows the stance the country is taking with the protection of personal data.
Achieve Compliance Easily with LogRhythm
When it comes to achieving compliance with regulations, LogRhythm’s suite of products and team of experts can help you easily do so.
With our SIEM platform, you can collect data from different devices across your environment (i.e. network, firewalls, anti-malware, etc.) and consolidate them into a single view. Your security teams can easily view, analyze and correlate these data to detect any suspicious behavior or a potential data breach before swiftly responding. In addition, the SIEM comes with compliance automation modules that simplifies your compliance program by providing a core, shared module mapped to dozens of regulations, encompassing the majority of common cybersecurity controls. Our experts are also able to assist you in mapping controls to the relevant regulations in the Thai PDPA. In addition, the LogRhythm NDR help you gather PCAPs that can be used as evidence in the event of a data leak.
Once you’ve checked the boxes of compliance, we can also help you continue your journey from monitoring to active threat hunting. In this case, our user entity and behavior analytics (UEBA) solution can be delivered as an integrated component in our SIEM. The LogRhythm UEBA uses machine learning to detect user-based attacks, allowing you to monitor and manage user access, keeping you alerted in case of any unauthorized access or exfiltration of any protected data.
To learn more about we can help, speak with us today!