There was a lot covered at this year’s 2022 RhythmWorld Security Conference! In one of our more technical sessions, we discussed Microsoft Sysinternals’ recent release of Sysmon for Linux, an open-source Linux system monitoring tool. You can find the project on their Github page to view the documentation and source; there are plenty of resources about how to download, install, and configure the Sysmon for Linux software. In this blog, we will cover the next steps you can take to use the logs that it generates, as well as where to best use them within LogRhythm SIEM.
When assessing how Sysmon for Linux works, there are a lot of similarities to Sysmon for Windows in how it can be configured and how the logs are generated. Of course, with different operating system architectures, there are some changes, too.
When looking at the XML log that it generates, it is nearly identical to its Windows counterpart. However, collecting via Syslog rather than the Windows Event Log makes sense for a *nix system. Similarly, the configuration file that is used to configure Sysmon is shared between the different implementations, but the config files that have a lot of maturity (such as SwiftonSecurity) need to be refactored to look for those *nix processes, folder paths, and other considerations.
Continuing with the similarities, the outputs also provide some resemblance to the Windows version, and the only differences we found were some of the punctuation where there were single versus double quotes being substituted. At the time of writing this blog, there are currently twenty-five Event Types within the Windows Version. Eight of these have been brought over into Sysmon for Linux, keeping the Event IDs the same.
Overall, this allows for a great foundation of both knowledge and usability within LogRhythm SIEM, as the familiarity is there to allow for an easy movement from LogRhythm’s MITRE ATT&CK® module deployment and how we can use the output to monitor the *nix environments in the same way.
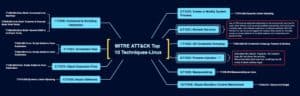
Ten MITRE ATT&CK Techniques to Monitor for
During our presentation at RhythmWorld 2022, we discussed the MITRE ATT&CK Top Attack Calculator. This allows us to input what log visibility we have available and operating systems to focus on. Then it outputs a list of the top ten use cases to monitor for from the MITRE framework. When considering the Sysmon for Linux logs provided, we found these top ten techniques to monitor for below:
- T1059 Command and Scripting Interpreter
- T1053 Scheduled Task/Job
- T1562 Impair Defences
- T1574 Hijack Execution Flow
- T1543 Create or Modify System Processes
- T1021 Remote Services
- T1003 OS Credential Dumping
- T1036 Masquerading
- T1055 Process Injection
- T1548 Abuse Elevation Control Mechanism
To test these techniques, we used the Red Canary Atomics and Caldera. If you want to review some of the testing approaches that we use, check out the Catching True Positives in Network Security blog. When reviewing the techniques listed above, we found that eighty percent can be monitored using the Sysmon for Linux logging. In addition to the monitoring of the Sysmon logs, we found that the default Auditd logging was not providing enough information to properly catch these attacks. While we can get eighty percent, the two that were not triggering are T1021 Remote Services and T1055 Process Injection, where other detection techniques are required. In the below graphic, we highlight the sub-techniques used against the techniques that were highlighted in the calculator.
As part of the follow up from our RhythmWorld 2022 presentation, we wanted to share the eleven use cases that we built out for the eight techniques that we found using Sysmon for Linux. The LogRhythm Community post provides a breakdown of the technique, some example log exports, the AI Engine use case that you can import directly to your SIEM, and even the ECHO use case to test whether the rules are working properly. This will provide a quick start into using and monitoring your Linux Systems with Sysmon for Linux. You can take the logs into the SIEM and provide great visibility on the top ten techniques MITRE recommends monitoring.
For more information about Sysmon for Linux, please check out the video below and LogRhythm Community links for the following articles for setting up, configuring, and use cases for use with Sysmon for Linux.
- RW2022 – Sysmon for Linux – Introduction and Setup
- MITRE: Top 10 Linux Use Cases – Sysinternals: SysmonForLinux


