Detect and remediate security incidents quickly and for a lower cost of ownership. LogRhythm SIEM offers embedded modules, dashboards, and rules that help you quickly deliver on the mission of your security operations center (SOC).
Mitigate Cyberthreats in Minutes
With intuitive, high-performance analytics, enhanced collection, and a seamless incident response workflow, LogRhythm SIEM helps your organization uncover threats, mitigate attacks, and comply with necessary mandates.
In this demo, watch a potential real-world scenario of a security analyst using LogRhythm SIEM to detect targeted phishing and MFA fatigue attacks.
How LogRhythm SIEM Can Help Your Security Operations
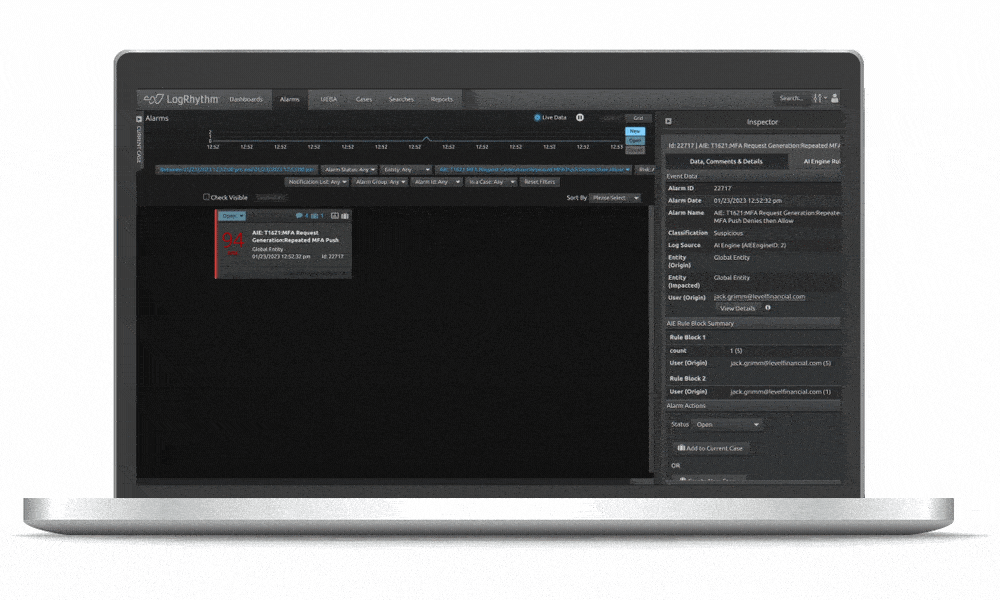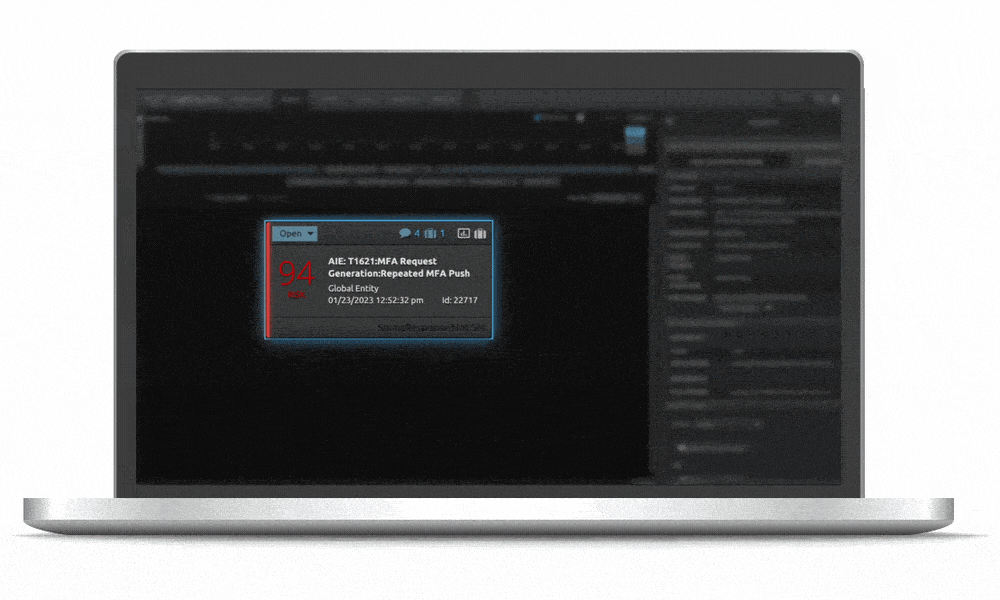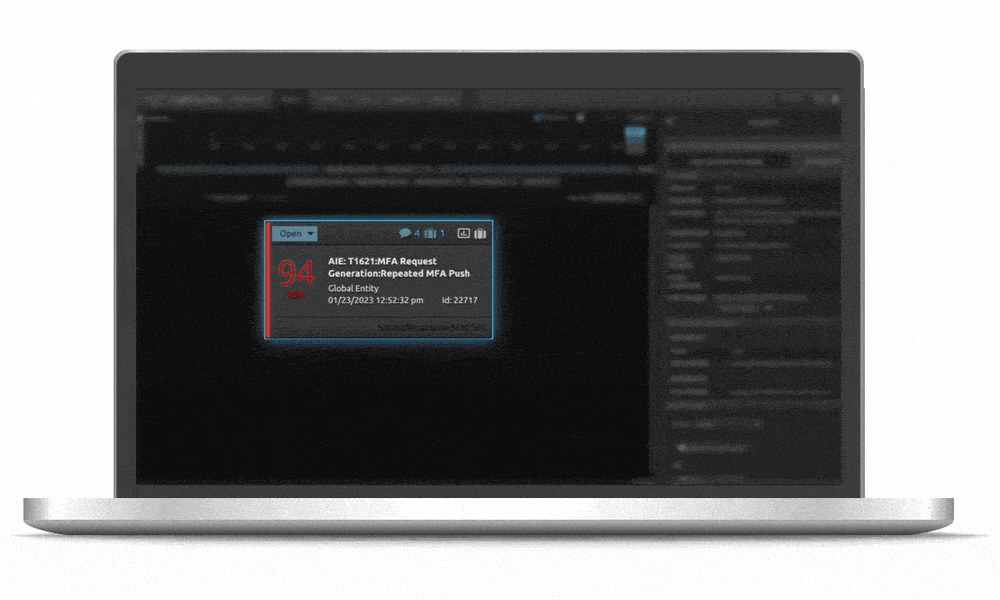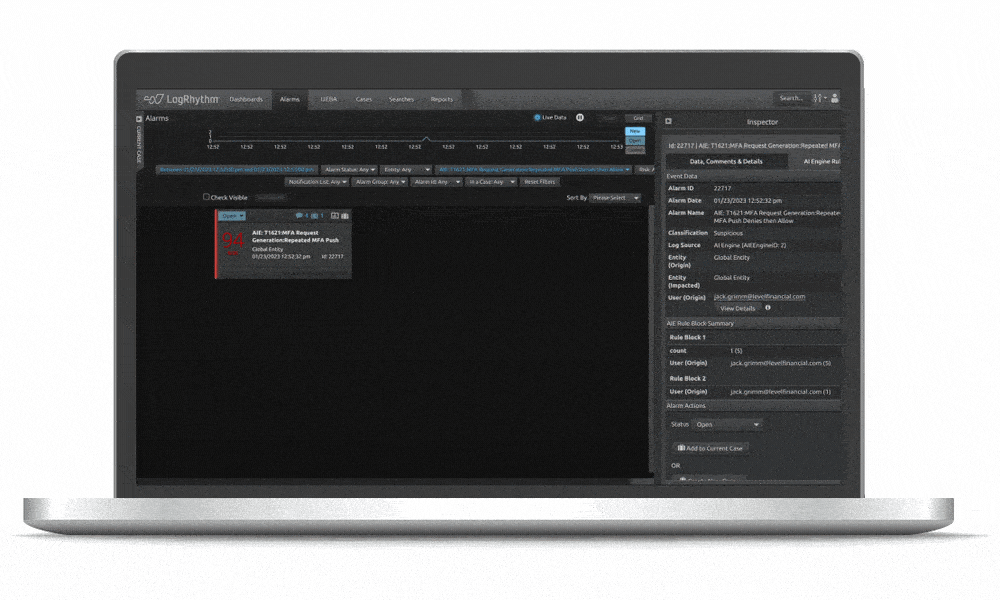
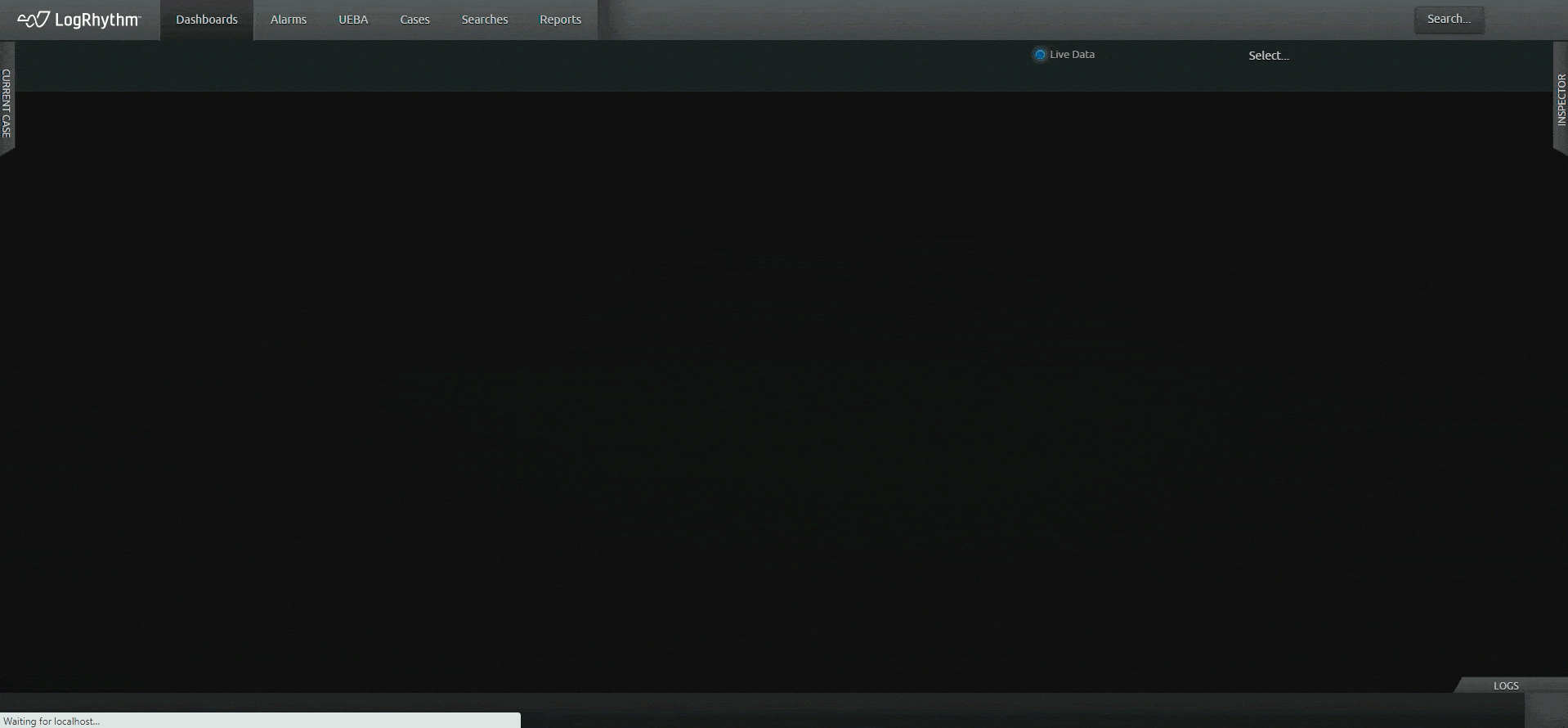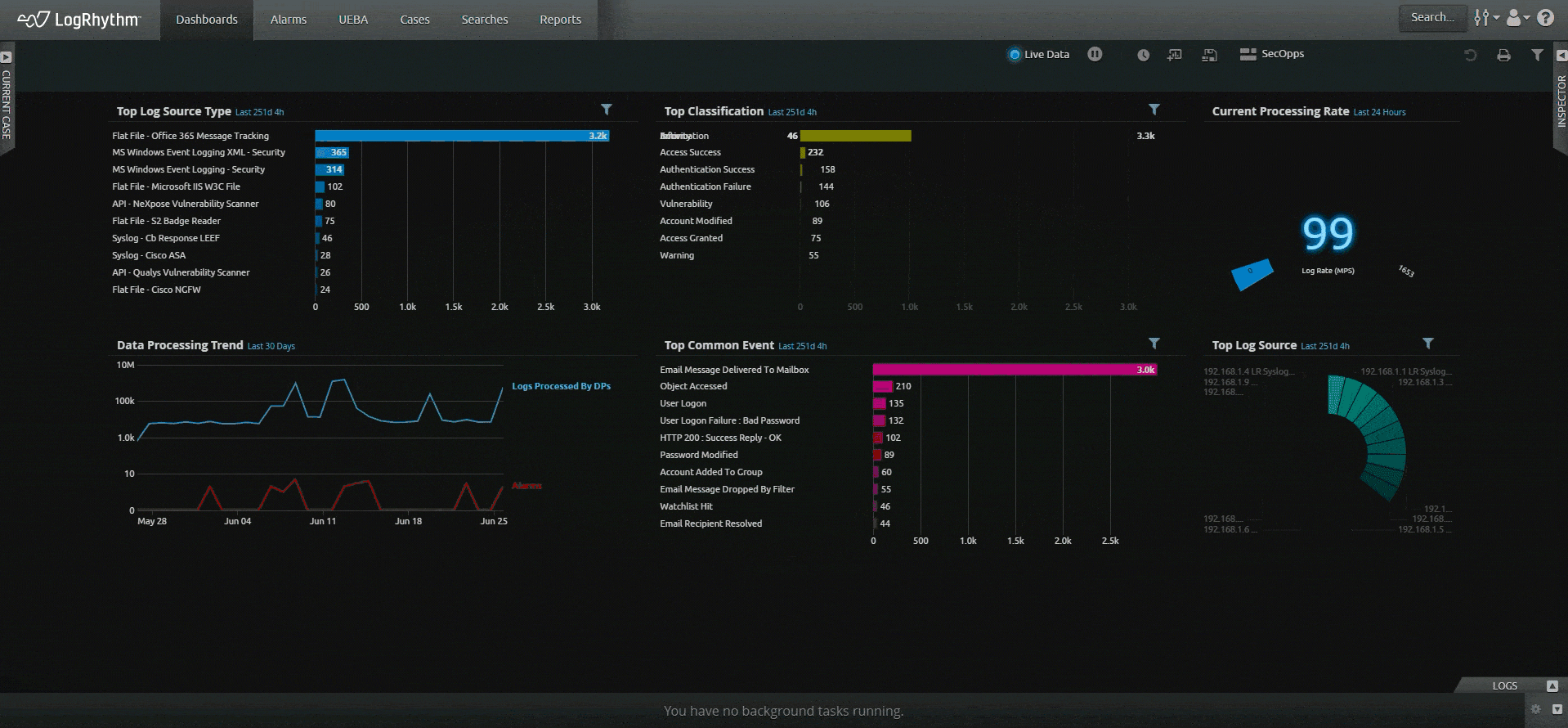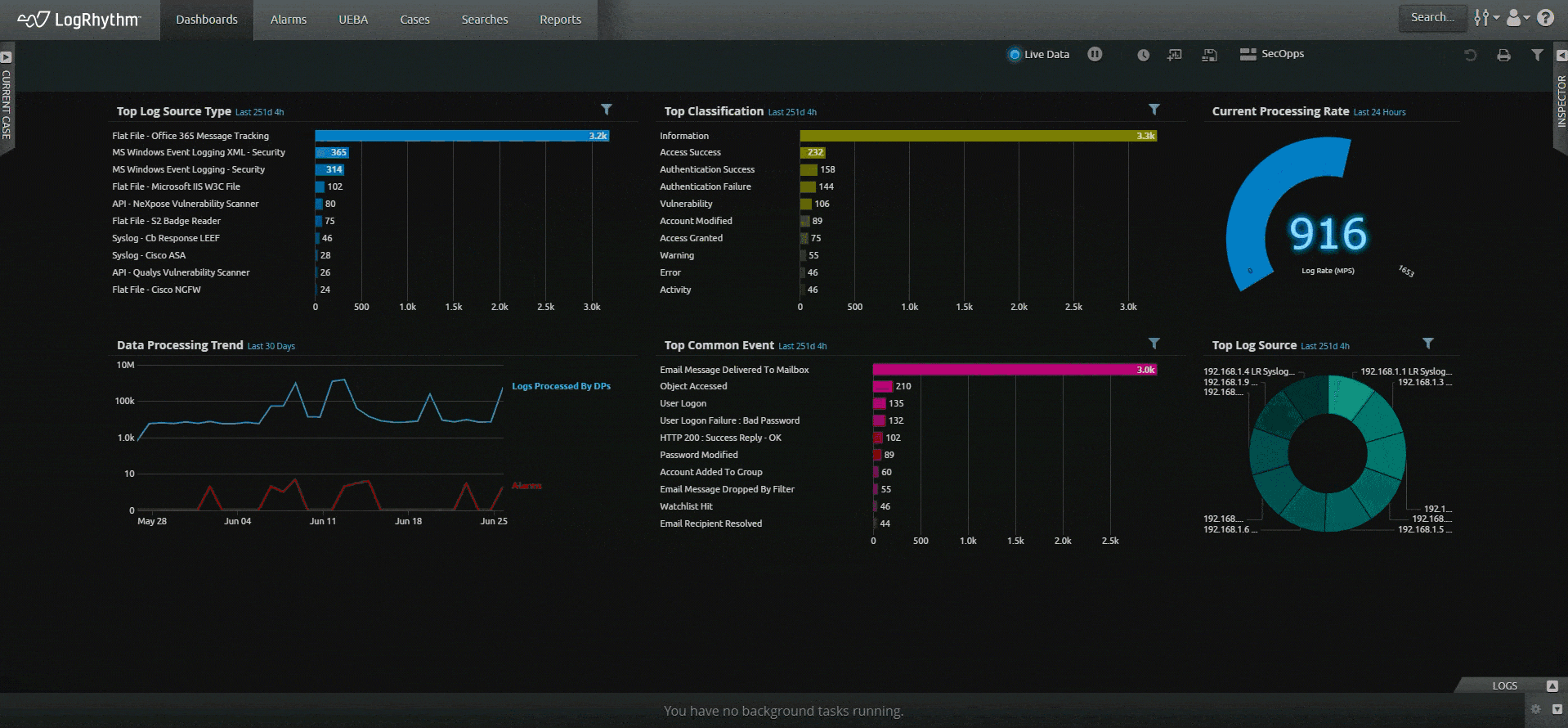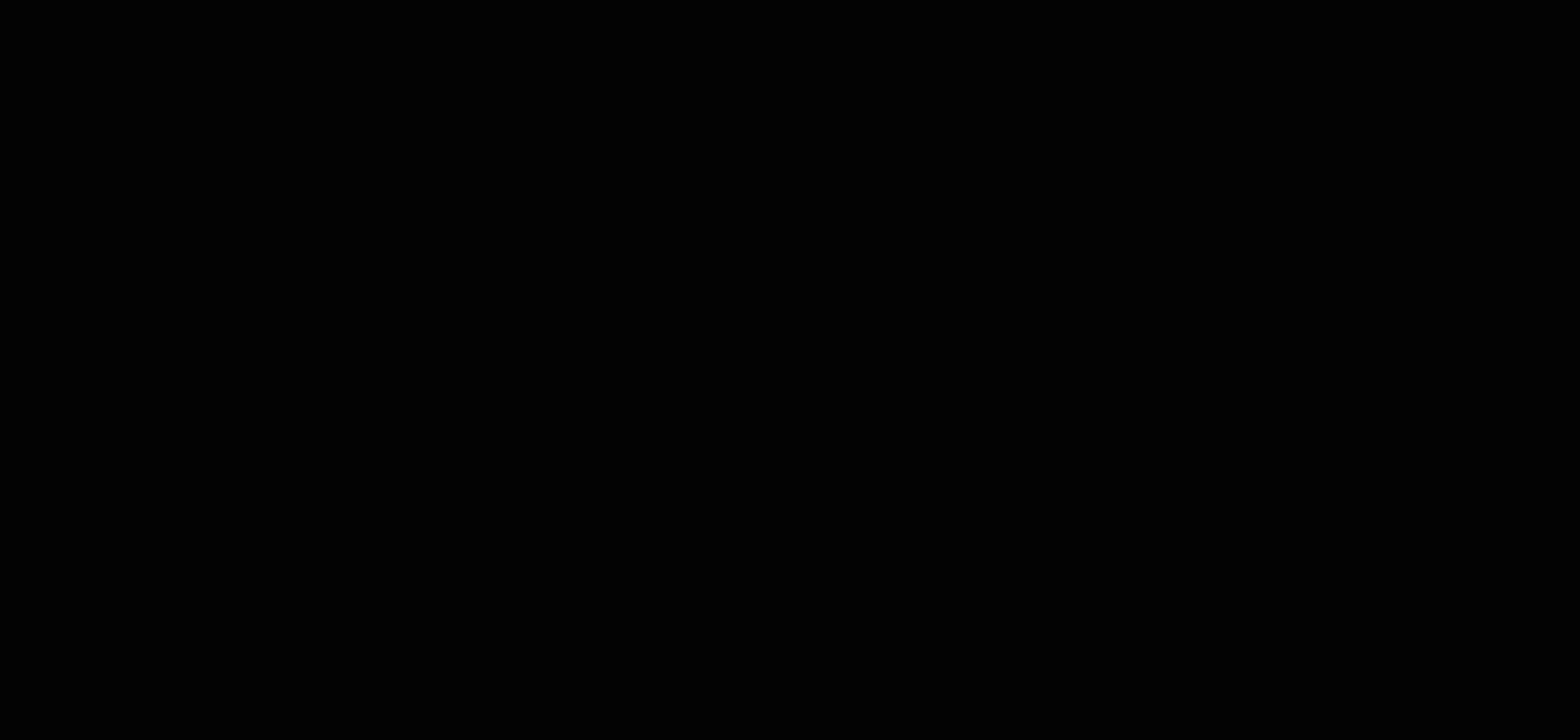
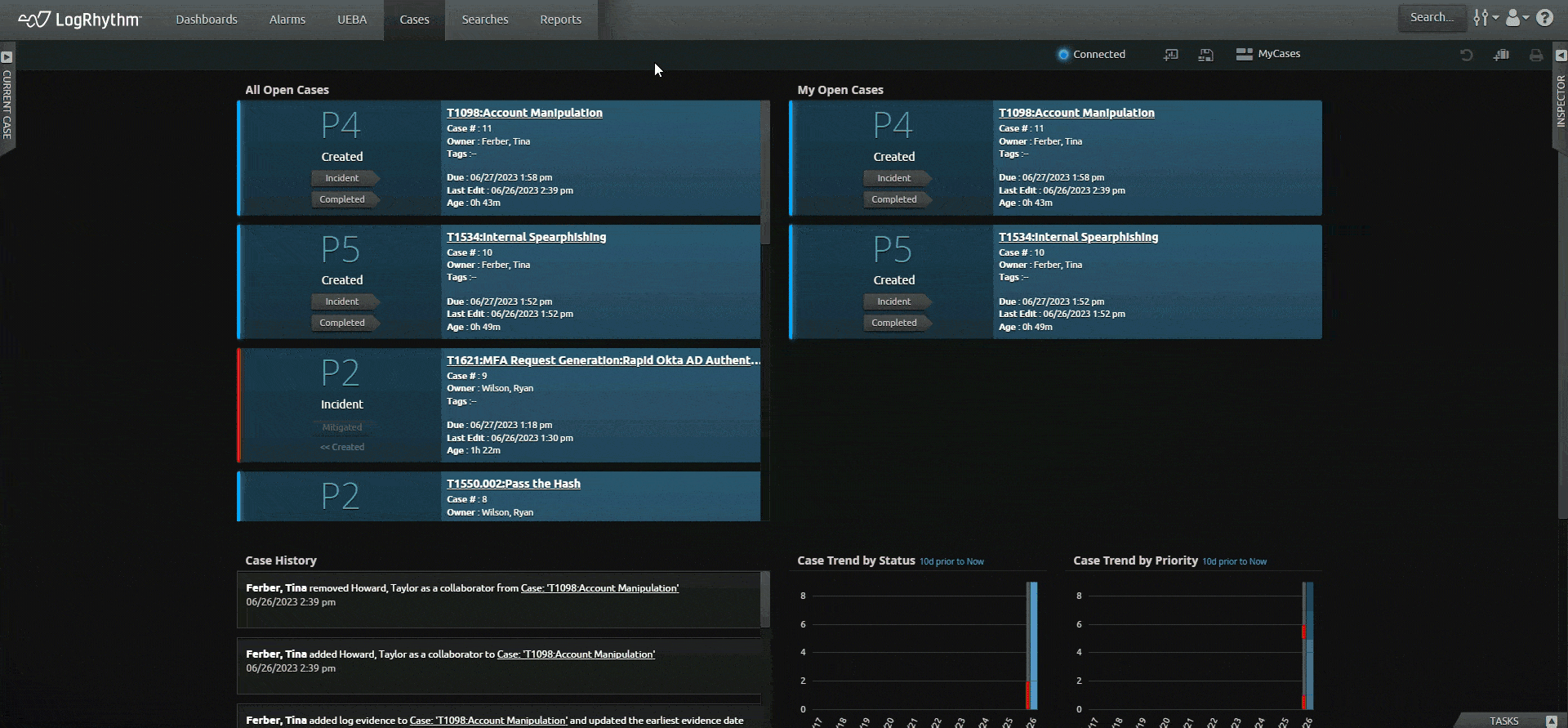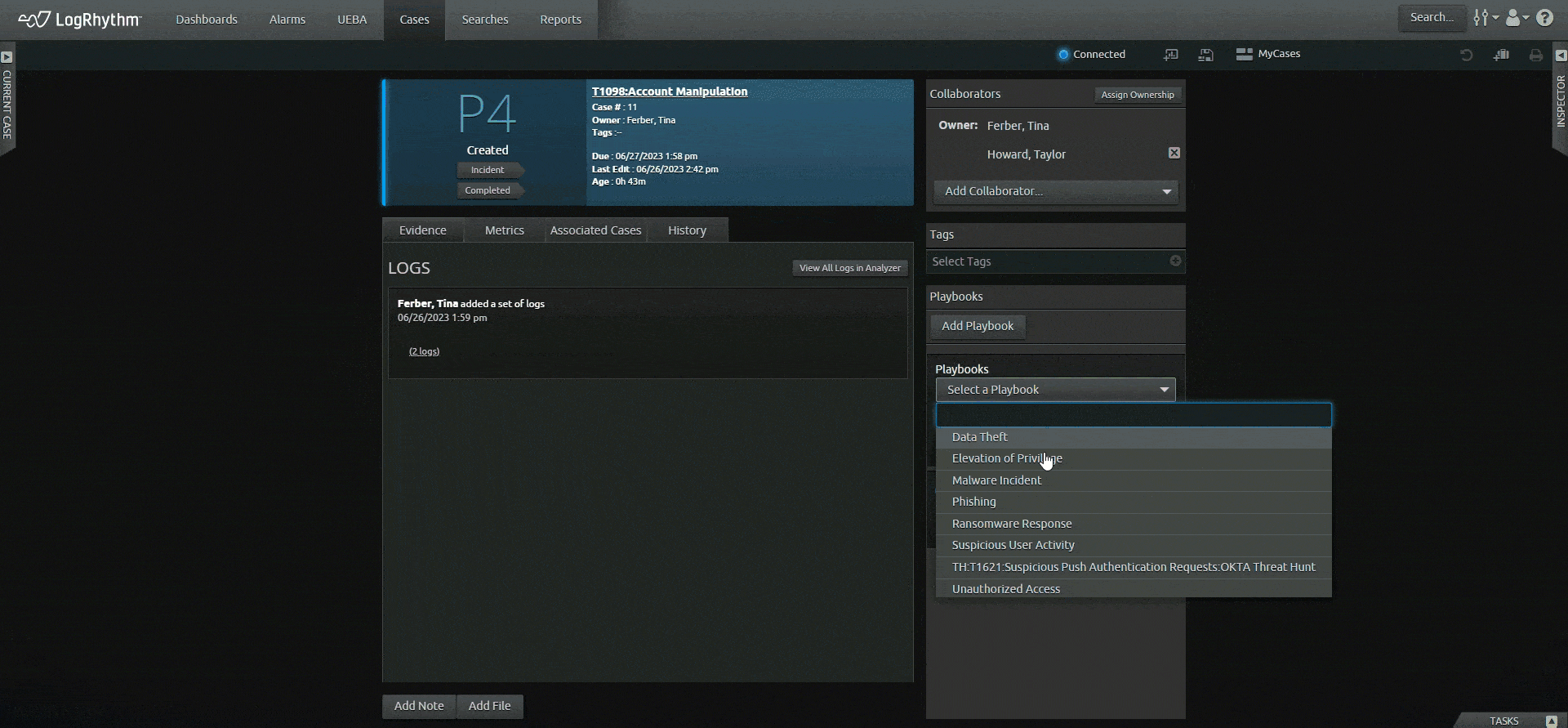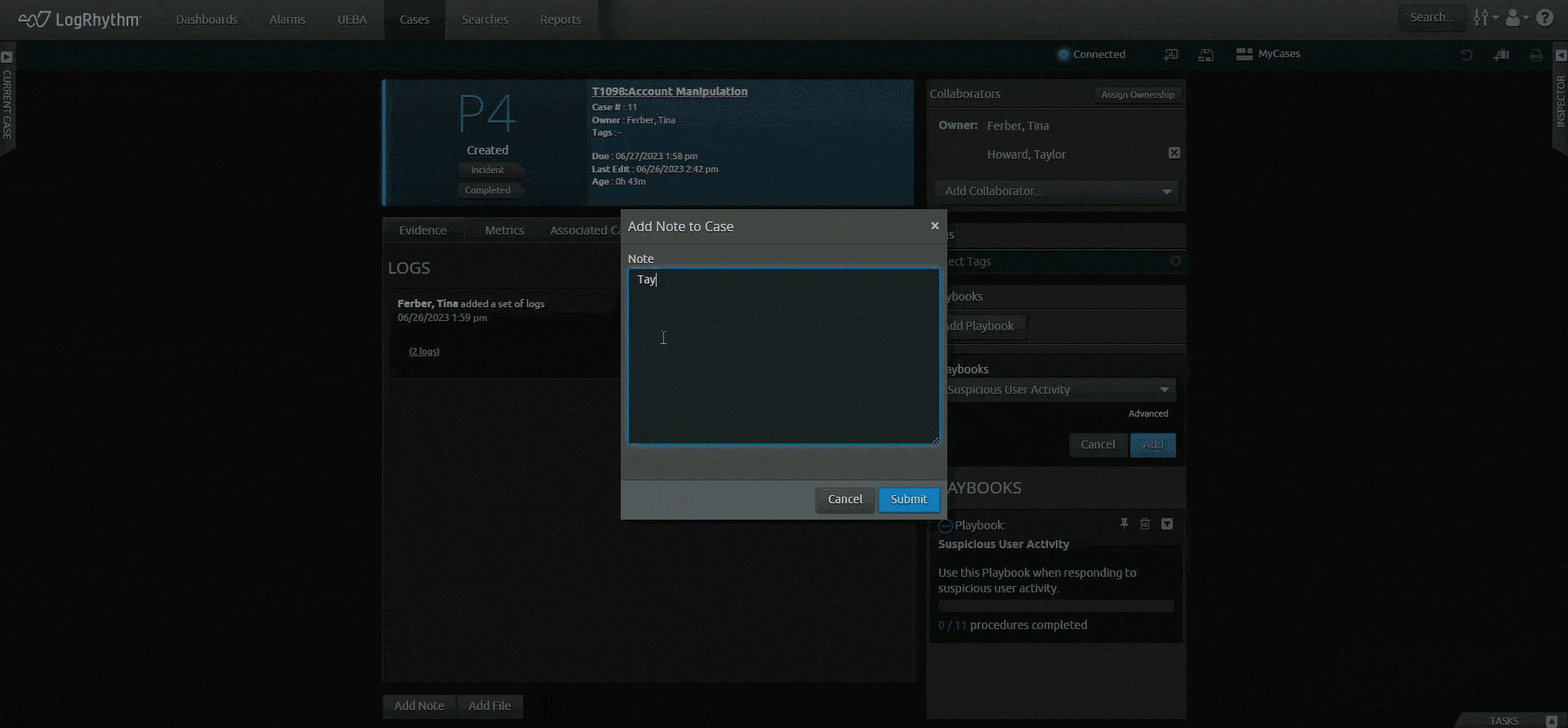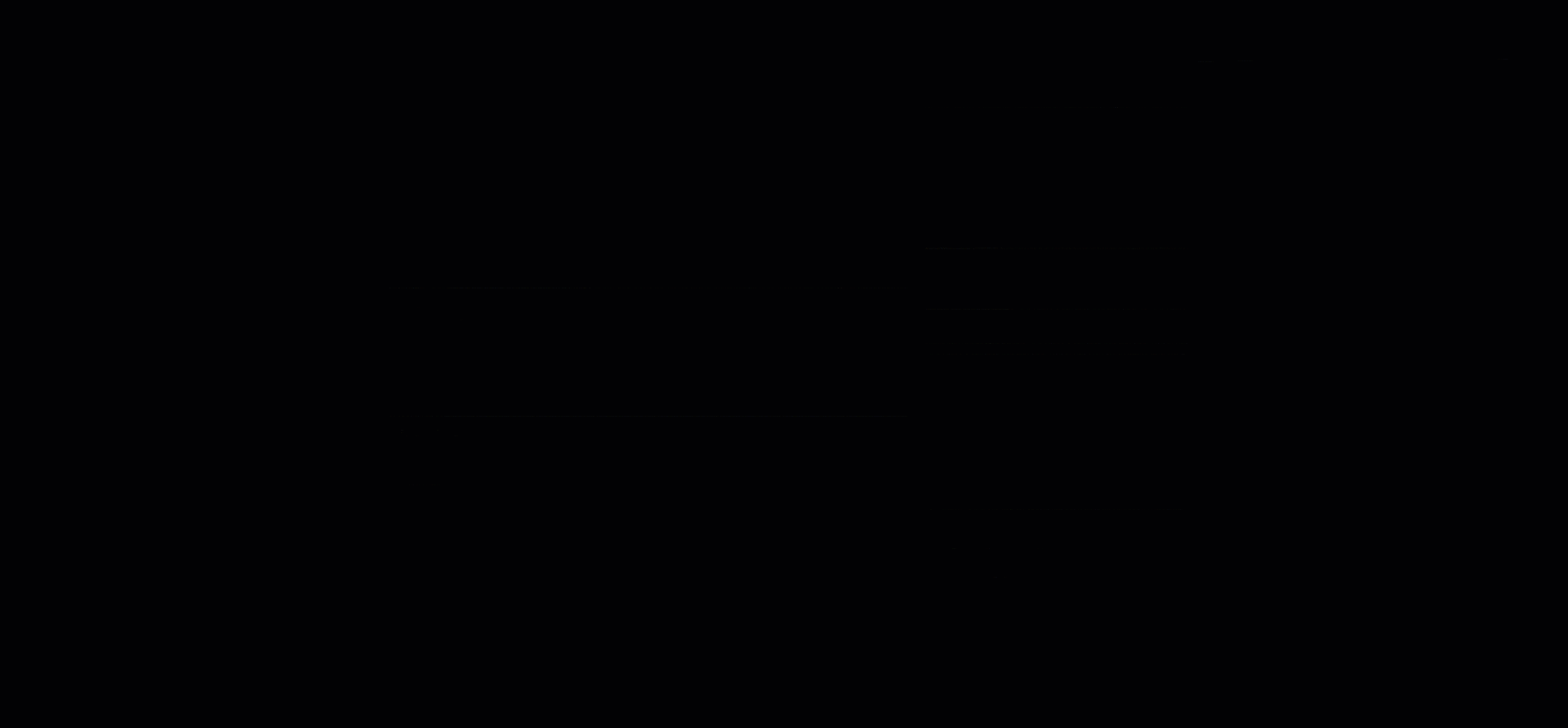
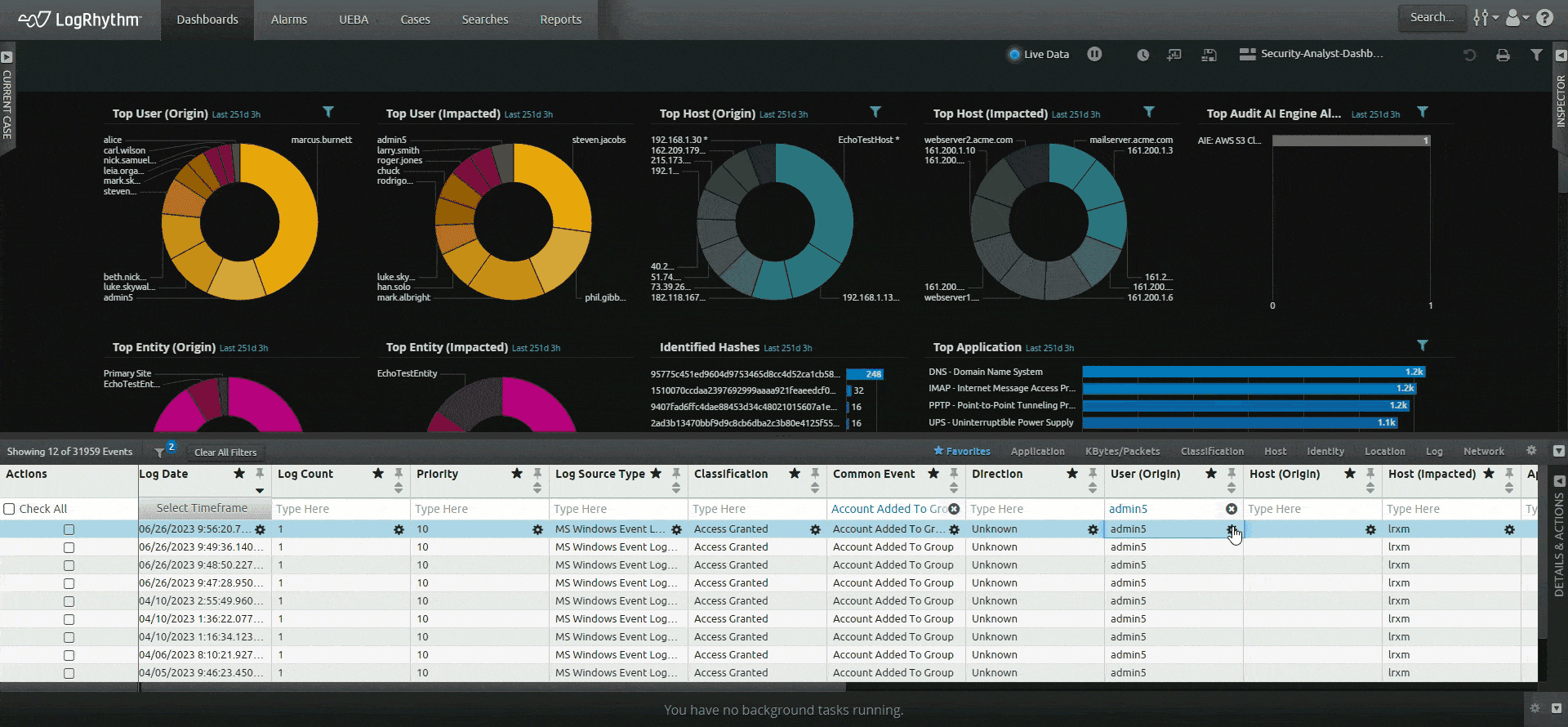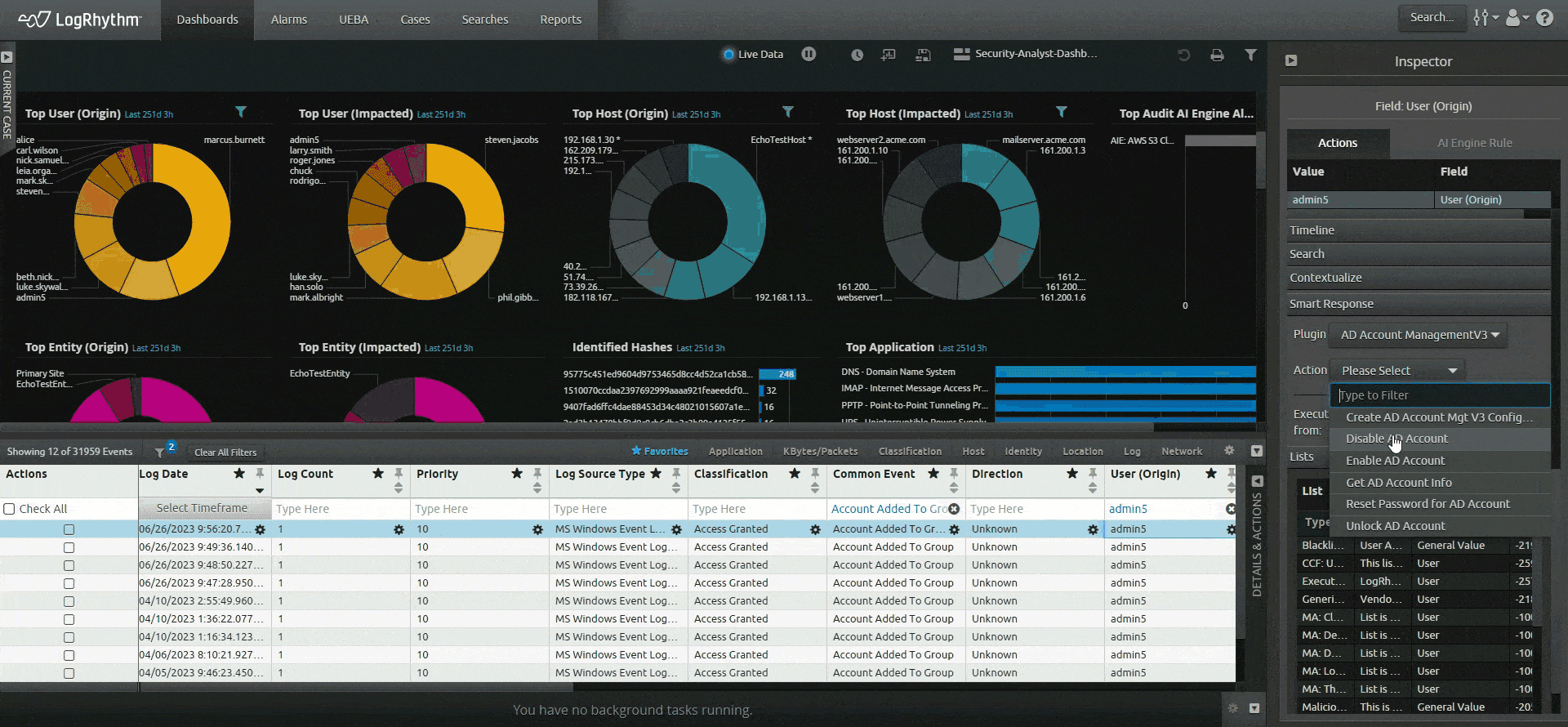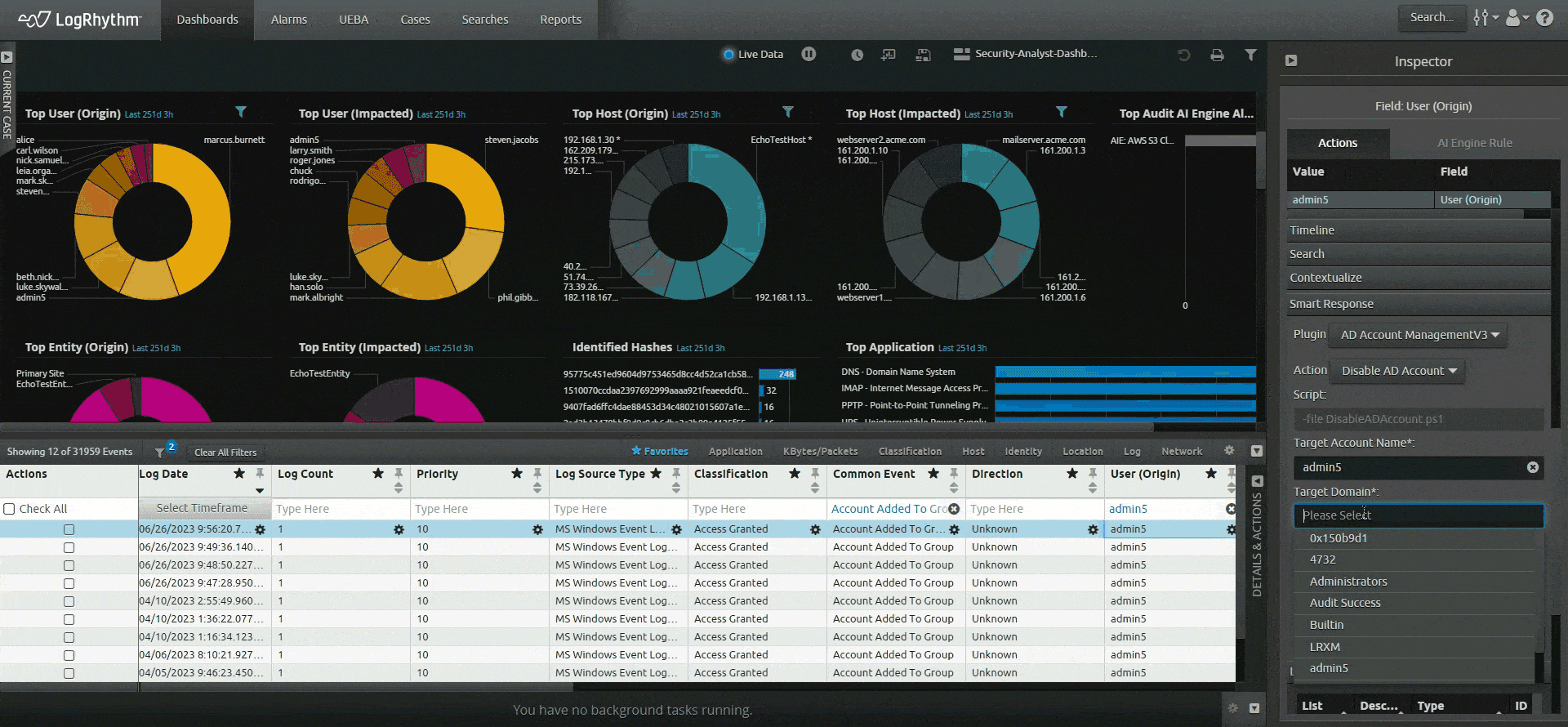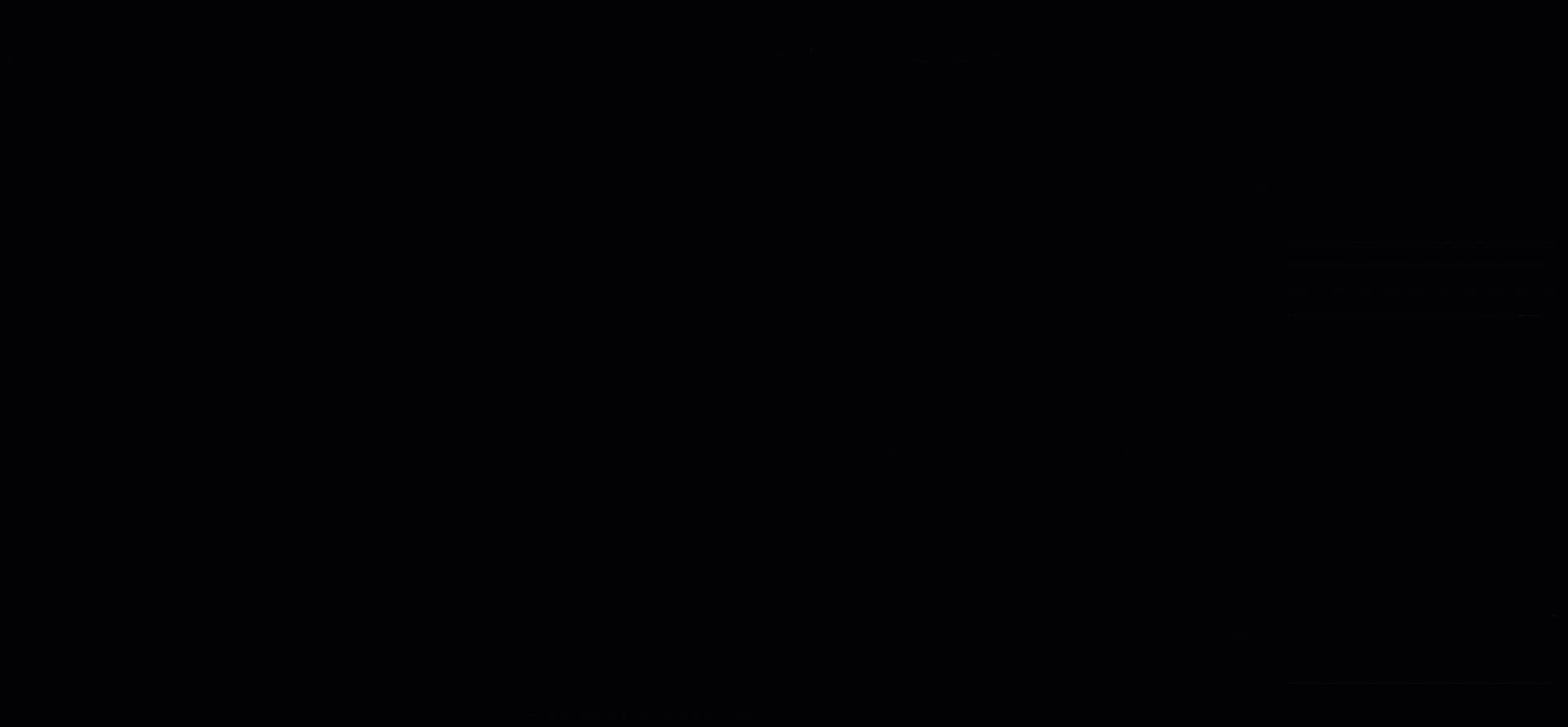
LogRhythm SIEM creates an easy-to-follow security narrative that consolidates user or host data and activity into one view, helping analysts quickly understand and remediate security incidents. LogRhythm SIEM streamlines incident investigation and response with a visual analyst experience that tells a security story about a user or host using all available data within the SIEM, helping security teams prioritize and focus on things that matter most.
Detect Threats Earlier and Faster
When it comes to stopping threats, seconds matter. That’s why we built our SIEM platform for speed. You’ll quickly identify threats, automate and collaborate on investigations, and remediate threats with agility. With LogRhythm’s Threat Intelligence Service (TIS), LogRhythm SIEM can synchronize with third-parties to obtain the most up-to-date threat data to use during threat detection.
Gain Visibility Across Your Environment
Gain greater insight across your entire enterprise — from your endpoints to the network to the cloud. Easily search across your log and other machine data to find the answers you need and know what’s happening across your environment.
Easy to Use
Enable analysts at all levels to quickly understand the severity of threats and use LogRhythm’s native built-in response capabilities to eliminate them fast. Remove the blockers that slow your team down with the easy-to-use capabilities of the SIEM. Get your organization up and running rapidly with our fast time to deployment.
Build for Today, Scale for Tomorrow
The complexity and scale of your environment is growing rapidly. Don’t settle for an entry-level solution that you’ll soon outgrow. Get high performance and reduced operating costs — for today and tomorrow.
Get SIEM in the Cloud
Are you looking for a cloud-native solution that reduces the burden of managing infrastructure and software updates?
LogRhythm Axon is our cloud-native SaaS SIEM platform with powerful security analytics, an intuitive analyst workflow, and effortless incident management that enables seamless threat detection, investigation, and response. Built to easily scale and manage, Axon helps security teams focus on the work that matters.

Achieve Success with Professional Services
Our Professional Services team can help you maximize your operations through expert support and work with you to identify use cases that address specific business needs to achieve fast results.
Explore LogRhythm's Unlimited Upgrades Service
Gain peace of mind when it comes to product upgrades with LogRhythm’s Unlimited Upgrades Service. Ensure your software is on the latest version and schedule upgrades on your time with a predictable budget.
Designed with the Analyst Experience in Mind
Gain Actionable Insight
Filter out the noise and gain actionable insight with centralized log management. Ingest logs from a variety of sources with LogRhythm’s log collection capabilities.
A Unified Platform
Let the SIEM platform do the work for you. Save time from navigating across screens and products with LogRhythm’s unified experience. Our easy-to-understand timeline of events, our prebuilt content — dashboards, alerts, and reports — and our built-in incident management tools (case management and playbooks) help you do your job quickly so you can achieve more immediate outcomes.
Work Smarter, Not Harder
Spend your time on impactful work instead of maintaining, caring for, and feeding your SIEM tool. Automate repetitive tasks and labor-intensive work with embedded security orchestration, automation and response (SOAR) capabilities so your team can focus on the areas where their expertise can make a difference.

Protect Your Critical Infrastructure with SIEM
LogRhythm can help you tell a cohesive story around user and host data, making it easier to gain proper insight needed to remediate security incidents faster.
In this demo inspired by real-life events, watch a security analyst use our SIEM platform to detect a life-threatening cyberattack on a water treatment plant.
Learn why LogRhythm is a recognized Leader for SIEM
Schedule a Custom LogRhythm SIEM Demo
Let one of our security experts review your use cases and demonstrate how the LogRhythm SIEM platform can help you detect and respond to threats faster than ever before.