Featured
Security Made Easy
Protect your critical data with confidence. Learn how LogRhythm can help you detect, investigate, and respond to cyberthreats.
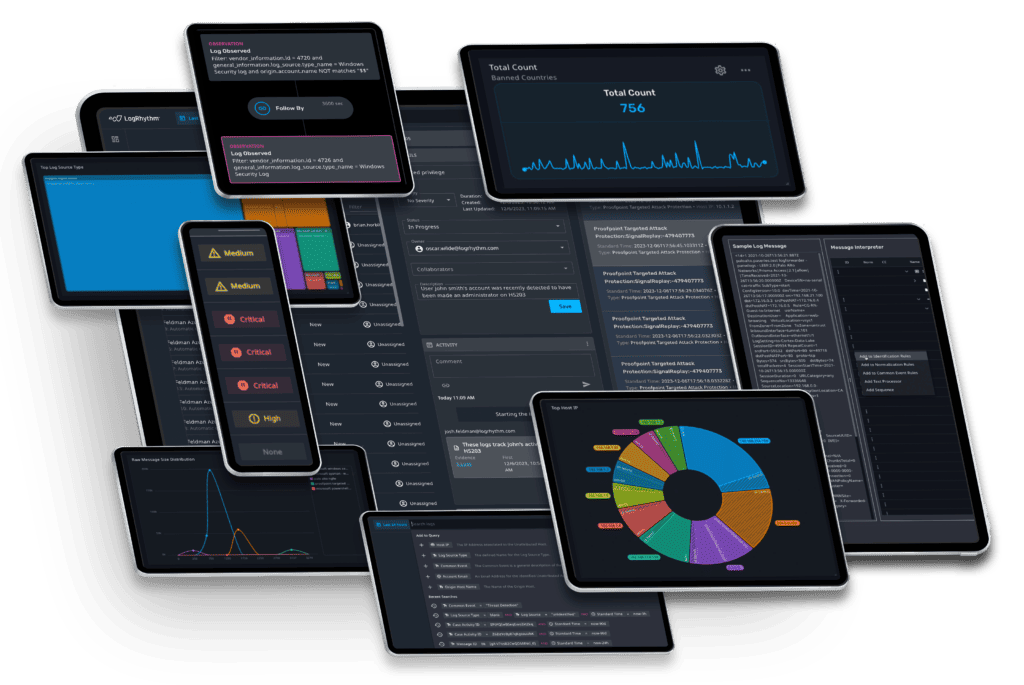
SecOps teams trust LogRhythm
0
+











LogRhythm Axon Detects Compromised User Accounts
Discover how LogRhythm's cloud-native SIEM platform detects compromised user accounts with improbable travel in this guided product tour
Compete in Virtual LogWars CTF
Do you have what it takes to be the next LogWars champion? It’s time to put your SIEM threat hunting skills to the test in our next friendly competition!
Join our virtual capture-the-flag event to compete against other cybersecurity professionals and test drive LogRhythm Axon.
Your Trusted Security Partner
We understand the amount of work and pressure security teams face. To ease the burden, LogRhythm delivers threat research and out-of-the-box content so that you can quickly defend against emerging cyberthreats.
- 950+ third-party and cloud integrations
- 1,100+ preconfigured correlation rules
- Prebuilt threat analytics, threat intelligence service feeds, and risk-based prioritization
- Prebuilt playbooks and automated response
SIEM Security Solutions for the SOC
Learn About Our Customer-Centric Approach
LogRhythm provides security operations center (SOC) services to our customers so they can build their strongest defense and maximize return on investment.
Whether you’re a large enterprise or a small team with limited resources, we’re dedicated to your success.
SecOps teams trust LogRhythm
0
+






















Recommended for You
How Can We Help?
LogRhythm is here for you every step of the way throughout your security journey. Contact us to learn more about how we can address your security challenges and requirements.
 Using the MITRE ATT&CK Framework to Boost Ransomware Defenses
Using the MITRE ATT&CK Framework to Boost Ransomware Defenses Forrester Total Economic Impact of The LogRhythm Platform
Forrester Total Economic Impact of The LogRhythm Platform Using the MITRE ATT&CK Framework to Boost Ransomware Defenses
Using the MITRE ATT&CK Framework to Boost Ransomware Defenses Forrester Total Economic Impact of The LogRhythm Platform
Forrester Total Economic Impact of The LogRhythm Platform SIEM Demo: Track the Progression of a Critical Infrastructure Attack
SIEM Demo: Track the Progression of a Critical Infrastructure Attack