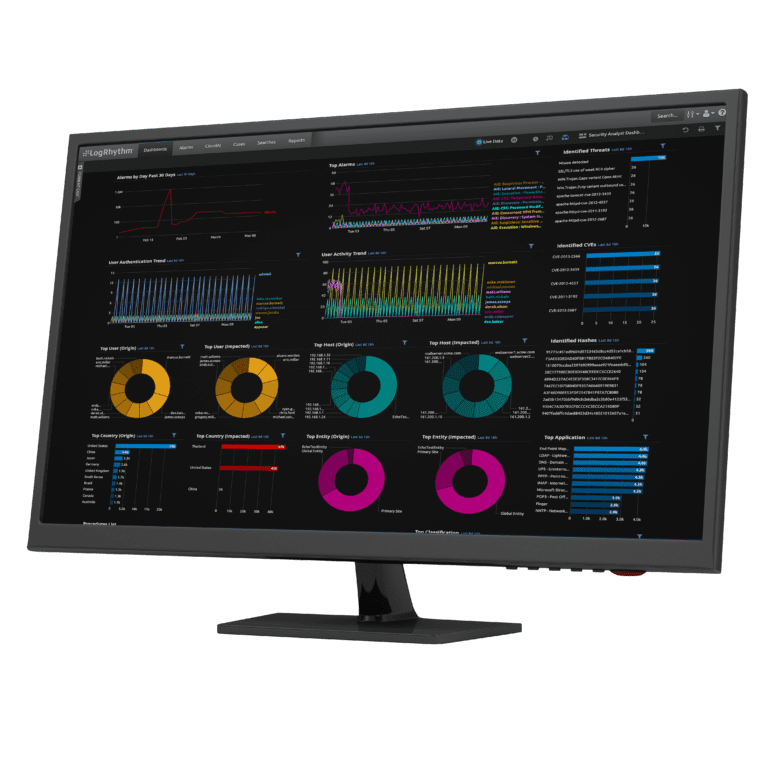
Protect your organization’s critical files, wherever they’re stored. Alert on malware-related registry changes, improper access of confidential files, and theft of sensitive data.
User-aware file integrity monitoring
Continuously monitor all files. Easily see who has changed what.
View user & file activity holistically
Pivot from a file access or change to a specific user. View a full timeline of their activity, including both file integrity monitoring (FIM) and other behavioral information.
Monitor what matters
Selectively monitor file views, modifications and deletions, and modifications, as well as group, owner and permissions changes.
Enrich your security analytics
Use data generated by FIM to solve new use cases for User & Entity Behavior Analytics (UEBA) and Endpoint Threat Detection.
Alarm on unauthorized changes
Alarm on an unauthorized change to sensitive files and registry settings, whether caused by an attack or a change management error.
Identify abnormal behavior
Alert on anomalous user activity related to important files. Reduce false positives by corroborating with other data.
Achieve rapid time-to-value
Configure FIM to protect your files and intellectual property using out-of-the-box policies for many common applications.
Comply and secure
Address over 80 PCI DSS control requirements and many core HIPAA requirements. Alert and report using FIM policies. Streamline your compliance objectives so you can focus on your most important security priorities.
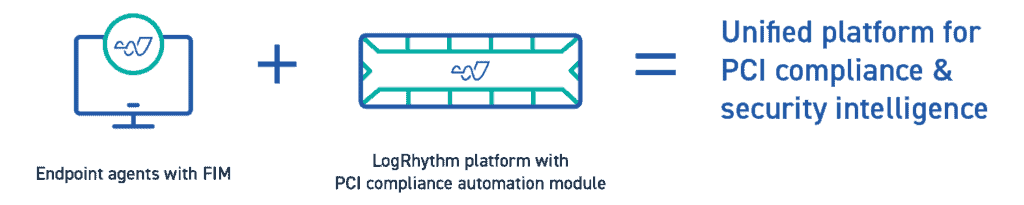
Achieve more on a unified platform
Get FIM as an embedded part of LogRhythm’s endpoint monitoring & forensics solution, a lightweight agent that also provides activity monitoring and process monitoring.
Endpoint monitoring & forensics is an integrated component of our LogRhythm SIEM Platform, helping you gain pervasive visibility and reduce your total cost of ownership.
FIM in action
Problem
You need to know if an attacker installs malware on your point-of-sale systems in an attempt to begin exfiltrating cardholder data.
Solution
Detect POS infiltration as soon as it begins by alerting on malware-related registry changes.
Problem
You spend significant time collecting data and creating reports for compliance audits (e.g., PCI DSS and HIPAA).
Solution
Generate reports on file access and other user activity rapidly. Give compliance auditors the data the need in the format they require.
Problem
You need to mitigate user-based threats to privileged files (e.g., payroll files) from both insiders and outsiders.
Solution
Enrich your UEBA with FIM data to identify users with anomalous file access behavior. See all that a user does before and after unusual access behavior.
Problem
A server has been improperly accessed and you need to know if sensitive files have been leaked.
Solution
Secure a complete set of forensic data to rapidly identify the cause and scope of the security incident.
Ready to see LogRhythm in action?
Watch how the LogRhythm SIEM Platform drastically reduces mean time to detect and respond to advanced cyber threats.
Watch the Demo to See the LogRhythm NextGen SIEM in Action
Keeping up with an increasingly sophisticated threat landscape while facing resource constraints isn’t easy. The LogRhythm NextGen SIEM Platform can help you stay one step ahead and keep threats from slipping through the cracks. It gives your team the advanced solutions it needs to solve challenges and reduce complexities it faces every day in a single, end-to-end platform.