Today, CyberEdge released their third installment of the Cyberthreat Defense Report in order to gain an understanding and provide awareness of how IT security teams defend against threats.
The report analyzes the current state of cyber security, including the perceptions and concerns of cyber security professionals. It reveals what the respondents believe are the next steps in defending themselves and ensuring they aren’t immortalized on the cover of The Wall Street Journal as the next high-profile breach victim.
The report shed both positive and negative light on the state of the industry. Overall, I believe companies are starting to understand that cyber threats are here to stay and investing in the right technologies and strategies is just good business.
Click image to expand
Here are my seven most significant insights from the CyberEdge Cyberthreat Defense Report:
1. Firms now see information security as a business driver
In the past, the gold standard for IT security budgets hovered around 10% of the total IT spend with the majority of organizations spending much less. This year, the CyberEdge report revealed that over 58% of budgets allocated to security will eclipse 11%. The positive trend forward suggests that, as cyber security receives board-level attention, companies are realizing the quick return on investment.
Security is often an influential factor as it relates to business decisions. Companies must look at markets, market conditions, the return on investment or value but they also have to understand the security risks of entering into a new line of business, an agreement or partnerships with other businesses, or entering into a new country.
Investing in security is also investing in your brand. When your company lacks or is weak in security, it puts the brand at risk. A successful breach could cause irrevocable brand damage, potentially putting your company out of business.
2. Consumer devices are intertwined with business, making it hard to develop an enforceable policy
The report suggests that respondents feel insecure in their ability to defend against cyber threats on mobile devices, with 65% of participants experiencing an increase in mobile attacks and attack vectors over the past year. However, the adoption of bring-your-own-device (BYOD) policies dropped for the third consecutive year.
The root of the BYOD problem has always been about access to data or the unintended proliferation and exposure of sensitive data. The pace of innovation associated with the Internet of Things (IoT), including mobile or embedded devices, surpasses our ability to protect this data. Consumer devices are so intertwined now with the business, it becomes very hard to develop an enforceable policy.
3. Employee behaviors are the most difficult aspect of security today
The biggest barrier in establishing an effective defense in many organizations remains the inability to raise awareness of security best practices amongst employees. While this is discouraging, it’s not a surprise.
In an ideal world, user behavior, as it relates to security, is about the understanding and awareness of threats and the tactics, techniques, and processes used by those threats. It’s an understanding of the impact each individual can have on the overall success or downfall of the company. It’s an understanding and awareness that a single person can actually make THE difference. People should understand that they are a target every single day and they should be careful with emails, websites, and even phone calls that seem out of the norm.
Although security awareness and user behavior is critical to the success of any security program, we can never fully expect users to be mistake-free—that is a part of being human. As such, there will always be compensating controls needed in anything that involves a human at a keyboard on a network.
4. Ignorance is not bliss when it comes to the maturity of vulnerability management
The report mentioned ignorance being bliss as it relates to vulnerability scanning. I think that’s a little misleading.
Vulnerability scanning large infrastructures can be intense if not done right. There are so many things you don’t want to scan as it might severely impact or cripple your core business.
Vulnerability scanning also adds a ton of stress to the network. At the end of the day, they are just going to tell you that have a patch management problem, and best case, it can provide you with a source of intelligence that you can operationalize in order to reduce risk and implement protections (monitoring and detection) as compensating controls to that risk.
Vulnerability management needs to be seamlessly integrated into your IT operations. The best way I’ve seen this done is to use your DHCP infrastructure as a triggering mechanism for vulnerability scanning.
A new system pops online, and if you haven’t scanned it in two weeks, it is automatically scanned. If it has been scanned in the last two weeks, you leave it alone. This reduces scanning down to a nominal number of systems at a time vs. trying to schedule whole scale sweeps over the course of a long weekend.
If you look at the report, the majority of folks do quarterly scans, that’s historically been the de facto standard—especially when conducting large scale sweeps. By integrating with the DHCP infrastructure, you get an accurate gauge of the risk of exploitation much more often than quarterly while reducing management overhead and infrastructure stress.
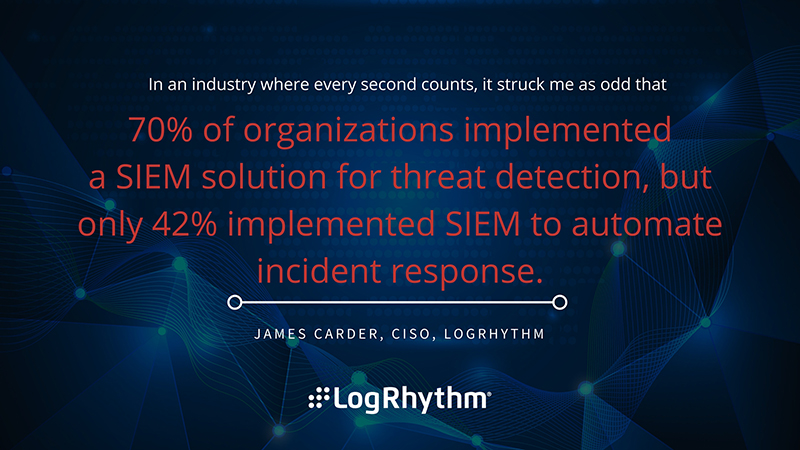
5. There is a gap between detecting a threat and responding to a threat
In an industry where every second counts, it struck me as odd that 70% of organizations implemented a SIEM solution for threat detection, but only 42% implemented SIEM to automate incident response.
For those organizations with a SIEM solution, successfully integrating with security infrastructure (endpoint, network, etc.), operationalizing the data from each of those and automating detection and remediation is vital.
SIEM is considered the central brain for almost every cybersecurity program and fundamentally bridges the gap between detection and response, yet an unnecessary gap remains in the industry. To me, detection and response go hand-in-hand, and if you have one without the other, then you are introducing unnecessary risk into your organization and extending the mean time to detect, respond and contain.
Likewise, the report mentioned 1/3 of organizations struggle to automate remediation of malware infected hosts. In this case, organizations rely on manual techniques and processes that generally involve reimaging and restoring systems to recover compromised systems and data. Automating the manual remediation process, even the ability to rollback to seconds before you were infected, can make all the difference and can be triggered and executed at your SIEM.
6. Antivirus is not the answer
Eighty-six percent of people are looking to replace their end-point defenses. Obviously, organizations finally understand antivirus alone is not the answer. Though it can be a component to your overall security strategy, organizations need to adopt a holistic security approach, focusing on detection and response.
7. Adopt big data to answer security questions
Ten years ago, the use of big data analytics to answer cyber security questions was a bit of a pipe dream. While plausible in theory, very few were able to get their arms around the sheer volume of available data—let alone use it successfully to answer security questions or solve security problems. The analysts, skilled in system administration and lightly skilled in security were instead forced to manually comb through data and try to make heads or tails of what the data was saying.
As an industry, we’ve have some recent success stories in using technology to corral and correlate various data sources using analytics and machine learning to answer tough security questions and solve complex security problems, taking some of the work away from the lightly skilled analysts.
That trend of success has led to wider scale adoption as companies understand that technology has to be used as a way to operationalize cyber security, as they cannot rely on hiring and retaining an army of skilled resources necessary to detect and prevent breaches from occurring.
According to the report, SIEM, analytics and threat intelligence ranked highest for planned technology acquisition in 2016 (35% of organizations planned to acquire).
As the focus shifts from prevention to incident response, the use of SIEM as an integration engine for big data and intelligence will make the difference in detecting and containing a security event before it ever becomes a breach.
Overall, organizations have a heightened awareness of cybersecurity and a high level understanding of how to solve the problem. However, there is still a gap right now between awareness and execution. Remember, it’s not often about what you know that makes the difference, it’s about taking what you know and doing the hard work necessary to put it in action. As Thomas Edison once said, “Genius is 1% inspiration and 99% perspiration.”